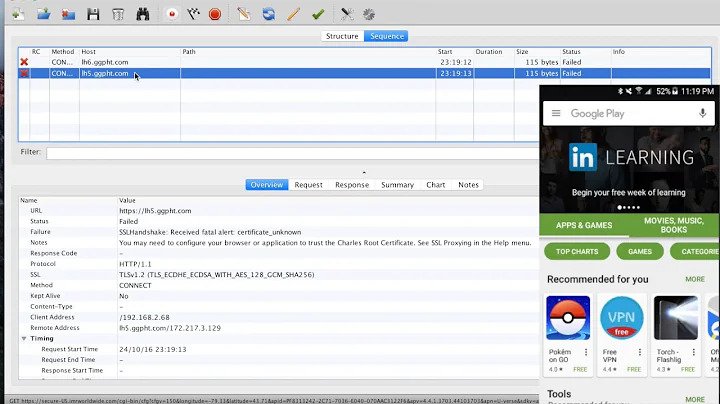
Received TLS alert from the server: Handshake failed (40)
Solution 1
The root of problem was an absence of TLSProtocol directive in /etc/proftpd.conf. Default value is TLSv1 and it prevents usage of TLSv1.2.
I have added
TLSProtocol TLSv1.2
to /etc/proftpd.conf, restarted the server and the problem was solved.
https://forum.filezilla-project.org/viewtopic.php?f=2&t=45829&p=157134#p157134 http://www.proftpd.org/docs/contrib/mod_tls.html#TLSProtocol
Although it solved my case, it is also recommended to use
TLSProtocol ALL -SSLv3
instead.
https://forum.filezilla-project.org/viewtopic.php?p=157135#p157135
Solution 2
Assuming you're using the system-installed OpenSSL libraries (e.g. your RedHat RPM installation), you can view the available ciphers by running:
openssl ciphers -v 'ALL:!ADH:!DES:!SSLv2:!SSLv3'
If filezilla simply doesn't speak SSLv3/TLSv1 (roughly equivalent), you're out of luck and should look if there is an updated version available that does.
There may be another configuration/ciphersuite setting that is suitable for your workload, but getting it from this forum without properly analysing the requirements of your situation is not advisable.
Related videos on Youtube
user619271
Updated on September 18, 2022Comments
-
user619271 over 1 year
I've got new web server with
proftpdonboard. The problem is I can't connect to it throughfilezillaFTP client because it gives me an errorStatus: Connection established, waiting for welcome message... Response: 220 FTP Server ready. Command: AUTH TLS Response: 234 AUTH TLS successful Status: Initializing TLS... Error: Received TLS alert from the server: Handshake failed (40) Error: Could not connect to serverI found that the error corresponds to the proftpd log
/var/log/proftpd/tls.log/var/log/proftpd/tls.logrecord:Jul 24 13:50:47 mod_tls/2.4.2[1572]: unable to accept TLS connection: protocol error: (1) error:1408A0C1:SSL routines:SSL3_GET_CLIENT_HELLO:no shared cipherWhich means that the ftp client supports none of the encryption algorythms proposed by the server. As a result, the connection fails.
I have also found a
TLSCipherSuitedirective in/etc/proftpd.confthat disablesADH,DES,SSLv2andSSLv3ciphers.TLSCipherSuite ALL:!ADH:!DES:!SSLv2:!SSLv3When I remove
:!SSLv3from the directive and restart the server, filezilla connects without any problems. But enablingSSLv3seems to be a bad idea because it is vulnerable and insecure, according to the http://disablessl3.com/Question
So my question is what can I do to make
proftpdprovide at least one secure cipher to successfully negotiate withfilezillaFTP client?Additional note
There is a similar question Recieved TLS alert from the server: Handshake failed (40) that tells
Use only plain FTP (insecure)
but I want connection to be secure thus the answer for me is unsuitable.
Additional note #2
List of available ciphers:
[root@server ~]# openssl ciphers -v 'ALL:!ADH:!DES:!SSLv2:!SSLv3' ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 DHE-DSS-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=DSS Enc=AESGCM(256) Mac=AEAD DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256 DHE-DSS-AES256-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AES(256) Mac=SHA256 ECDH-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AESGCM(256) Mac=AEAD ECDH-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AESGCM(256) Mac=AEAD ECDH-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AES(256) Mac=SHA384 ECDH-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AES(256) Mac=SHA384 AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256 ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 DHE-DSS-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AESGCM(128) Mac=AEAD DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256 DHE-DSS-AES128-SHA256 TLSv1.2 Kx=DH Au=DSS Enc=AES(128) Mac=SHA256 ECDH-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AESGCM(128) Mac=AEAD ECDH-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AESGCM(128) Mac=AEAD ECDH-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH/RSA Au=ECDH Enc=AES(128) Mac=SHA256 ECDH-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH/ECDSA Au=ECDH Enc=AES(128) Mac=SHA256 AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256 -
 Liam Dennehy over 6 yearsNow you need to see which ciphers and SSL/TLS versions are supported by your filezilla client. If there isn't at least one that overlaps, this will never work.
Liam Dennehy over 6 yearsNow you need to see which ciphers and SSL/TLS versions are supported by your filezilla client. If there isn't at least one that overlaps, this will never work.