Can I be my own trusted CA via an signed intermediate certificate?
Solution 1
Your question reads to me and to others as "How do I issue certificates to entities inside and outside of my organization that are trusted by arbitrary internet users?"
If that is your question than the answer is "You don't.". If it isn't, please clarify.
I also recommend reading "Windows Server 2008 PKI and Certificate Security by Brian Komar" and consider all of the various PKI scenarios for your applications. You don't need to use Microsoft's CA to get something out of the book.
Solution 2
A quick search shows that such things exist, but with the 'contact us for a quote' suggests it won't be cheap:
https://www.globalsign.com/en/certificate-authority-root-signing/
I make no claims about the company, but that page might give you terms to use to find other companies doing the same.
Solution 3
If you could do this, what's going to prevent Joe Malware from issuing a cert for www.microsoft.com and giving you his own "special" brand of updates through a DNS hijack?
FWIW, here's how to get your root certificate included by Microsoft in the OS:
http://technet.microsoft.com/en-us/library/cc751157.aspx
The requirements are pretty steep.
Solution 4
This is basically indistinguishable from becoming a reseller for that root CA, which almost certainly costs lot of effort and money to be. This is because, as Tim notes, you can make a valid certificate for any domain, which shouldn't be allowed unless you control that domain.
An alternative is RapidSSL's reseller program in which they do all the hard work and issue from their root CA.
Solution 5
It is possible for a root CA to issue a certificate which makes it possible to issue other certificates, but only under a specific domain. They need to set basicConstraints/CA:true and nameConstraints/permitted;DNS.0=example.com
Then you are free to run your own CA and issue certificates like test.example.com (but not test.foobar.com) which in turn will be trusted by the public web. I don't know any root CA that provides this service, but it is indeed possible. If anyone stumbles upon such a provider, please let me know.
Related videos on Youtube
Clint Miller
Director of IT, Sysadmin, DBA & Software Developer for RT Creative. Yes, I have lots of questions.
Updated on September 17, 2022Comments
-
Clint Miller over 1 year
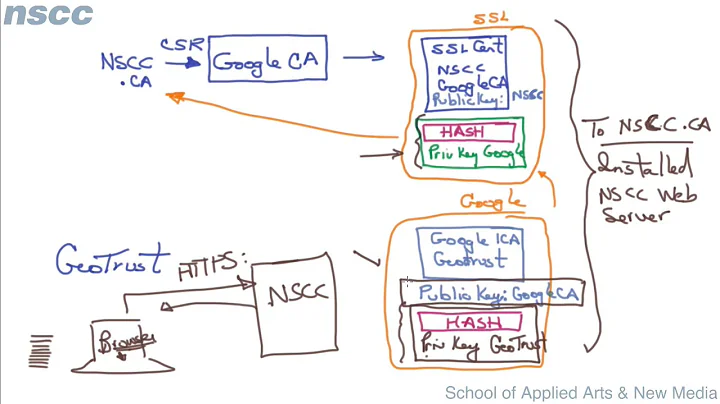
Can I get a certificate from a root CA that I can then use to sign my own web server certificates? I would, if possible, use a signed certificate as an intermediate to sign other certs.
I know that I would have to configure my systems in a certain way with "my" intermediate certificate in order to supply information about the chain of trust to my clients.
Is this possible? Are root CAs willing to sign a certificate like this? Is it expensive?
BACKGROUND
I'm familiar with the basics of SSL as it pertains to securing web traffic over HTTP. I also have a basic understanding of the way the chain of trust works, in that web traffic is secured "by default" if you encrypt with a certificate that has a valid chain all the way back to a root CA, as determined by the browser/OS vendor.
I am also aware that many of the root CAs have begun signing certificates for end users (like me) with intermediate certificates. That may require a bit more setup on my end, but otherwise, those certificates will work fine. I guess this has to do with protecting their all-valuable private key for the CA and the disaster that it would be if i were ever compromised.
EXAMPLES
- https://www.microsoft.com
- https://www.sun.com
- https://ecomm.dell.com/myaccount/ga/login.aspx?c=us&cs=19&l=en&s=dhs
Now, we are definitely not the size of any of those organizations, but they seem to be doing something like this. It would definitely make the management of these certificates a lot more palatable, especially considering one way we are expanding the reach of our e-commerce platform.
-
Clint Miller over 14 yearsWell, 2 things, I suppose. 1. It's obvious that no root CA is going to allow me to sign certs for other entities that are not part of my organization. They may not be able to prevent me from doing it once, but it won't be long until the cert they signed for me is on revocation lists and then it will all be over. 2. Even more significantly, what "global" scale techniques are there for DNS hijacking? The cache-poisoning issue that Kaminsky made famous has been patched by the DNS vendors, right?
-
Clint Miller over 14 yearsI couldn't disagree more! I don't want to resell certs to others. I want to make the management of securing communications within our business and between our business and clients easier. Tim asked a legitimate question, but I think you're missing the point.
-
Clint Miller over 14 yearsI appreciate the input, but I think the examples I cited establish the "You don't" portion of your statement as incorrect. Look at the chain of trust for those certificates and you'll see that there is an enterprise-specific certificate between the root CA (distributed with browser/OS) and the certificate which the web server is using to encrypt HTTPS traffic.
-
duffbeer703 over 14 yearsIt's not just a certificate. Sun/Microsoft/Dell is operating an intermediate CA. Operating an enterprise, public-facing CA is an expensive, complicated task that requires periodic external audit. The Komar book explains a number of CA scenarios and illustrate why it is so complex. If your application design is leading you down the road to becoming a CA, you need to think long and hard about your design goals and implementation strategy.
-
Tim Howland over 14 yearsIf all the certs that you are talking about are owned by your organization, are they in the same top-level domain? If so, a wildcard SSL cert (*.mydomain.com) might be a better strategy.
-
feverzsj over 14 yearsI'm looking at it from the CA's point of view - to them, what you're asking is to become a fully-fledged CA in your own right, which is quite risky for them - just because you say you don't want to make certs for others doesn't mean that you won't have the technical ability to, hence they'll want serious controls to make sure you don't.
-
Clint Miller over 14 yearsUnfortunately I have more domains to secure, so the wildcard (which was the initial strategy) will not work for us as we have expanded our business to cases where a different domain is desired. My solution for the time being is SAN certs (subject alternative names), but it's somewhat painful to create a new certificate for every addition/deletion of another domain.
-
 Konrad Gajewski over 8 yearsPlease consider expanding your answer from the link provided. Link only answers get downvoted.
Konrad Gajewski over 8 yearsPlease consider expanding your answer from the link provided. Link only answers get downvoted.