CentOS Dual WAN - Load Balance and Failover
Actually reference you provided, describes a solution for your gateway router. What is misses, it's local lan setup. Here it goes:
- set up your NAT, on both interfaces
iptables -t nat -A POSTROUTING -o eth2 -s -j MASQUERADE
iptables -t nat -A POSTROUTING -o eth3 -s -j MASQUERADE
make sure you've enabled forwarding (
sysctl -w net.ipv4.ip_forward=1)check if facebook.com is alive, by pinging it, or trying http request - if it is alive, do nothing ;-) You may assume that if facebook.com is alive, your WAN link works fine. If it's down - people will call you anyway yelling the Internet is down, because facebook does not work anymore. You may write a script to do this.
in case the connection is down - you have to do only one task: add ip rule and direct your traffic through failover WAN link. It primary wan is on again - delete the rule, and flush the cache. Like this:
ip rule add from 1.2.3.0/24 table WAN2
ip route flush cache
or restore traffic:
ip rule delete from 1.2.3.0/24 table WAN2
ip route flush cache
Make your changes permanent. I'm not familiar with CentOS, but sysctl.conf and rc.local should be at your service.
Why you don't have to switch default gateway on your box? According to your reference, you have already added default routes to different routing tables. It means, your box will be still available through secondary routing table. And yes, even with primary gateway dead, you will be able to reach it with secondary table, which has it's own default route.
I'd also avoid balancing traffic through different prociders, as load balancing is based on route cache, so it may cause a lot of unidentified connectivity problems. I'd rather stick with failover.
There's just final thing - if your wan links are private networks, you won't be able to reach your box from outside your network other way than redirecting ports or setting up vpn link. In this case, switching gateways might be required.
For source reference check here.
Related videos on Youtube
Tom O'Connor
You can contact me by email for consultancy and similar requests, on [email protected] if you so desire. If you've got a question, or require linux consultancy, don't hesitate to get in touch. Here's a snippet from my CV: Good leadership skills and able to efficiently work alone or as part of a multi-disciplinary team. Extensive linux, networking and virtualization knowledge in parallel with windows desktop and server administration experience. Programming: Python, Django, Java, Perl, C, C++, Qt, MySQL, Postgres, XHTML, CSS, Javascript, Linux/UNIX shell scripting, SVN, CVS, Bazaar, Hudson, Selenium Applications: Adobe Creative Suite, Microsoft Office, Blackberry Enterprise Server, Microsoft Exchange, OpenOffice, Pro/Desktop CAD and electronic circuit design packages such as Proteus ISIS Operating Systems: Ubuntu and Debian Linux, VMware ESX & ESXi, XenServer, KVM, Microsoft Windows 7/Vista/XP/2000 and Server 2008, Apple OS X, Solaris, and other Linux/UNIX distributions. Network Technologies: iSCSI SAN, GlusterFS, Cisco IOS, Monitoring with Nagios, Munin and Zabbix, MySQL replication, Message Queues (RabbitMQ), High Availability & Scalable Network Architecture
Updated on September 18, 2022Comments
-
Tom O'Connor over 1 year
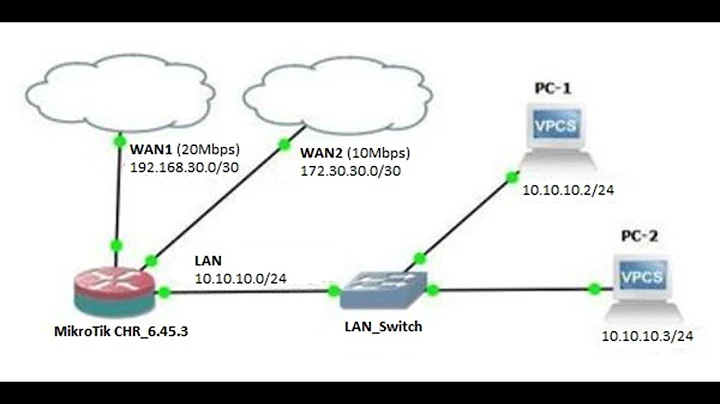
I am setting up a Linux server (CentOS) to act as a router with load balacing and failover (when one internet line is down, another one should take over). The clients conected to eth1 ( LAN ) should be able to access the internet.
My reference ( http://fatalsite.net/?p=90 )
Interfaces :
eth1 = LAN
eth2 = WAN1 - 192.168.1.100 / gateway 192.168.1.1 - ISP1
eth3 = WAN2 - 192.168.10.5 / gateway 192.168.10.1 - ISP2
How do i do that?
Thank you!
ok. so i did setup the nat and enabled forwarding, but still can reach the internet via LAN interface.
i've also did this, but no luck :
iptables -A INPUT -i eth2 -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A INPUT -i eth3 -m state --state ESTABLISHED,RELATED -j ACCEPT iptables --table nat --append POSTROUTING --out-interface eth2 -j MASQUERADE iptables --table nat --append POSTROUTING --out-interface eth3 -j MASQUERADE iptables --append FORWARD --in-interface eth1 -j ACCEPT