convert .p7b key to a .pfx
Solution 1
PKCS#7 does not include the private (key) part of a certificate/private-key pair, it is commonly used for certificate dissemination (e.g. as the response to a PKCS#10 certificate request, as a means to distribute S/MIME certs used to encrypt messages, or to validate signed messages etc). It is important to remember that it is only for certificates which are by definition public items.
PKCS#12 is a more universal container - it is intended to store both the private key and public certificate parts together so that they can be moved around. It has the capability of being password protected to provide some protection to the keys.
PFX was the predecessor of PKCS#12.
You cannot (as Anitak points out) convert from PKCS#7 to PKCS#12 without additional data (the private key part) because PKCS#7 doesn't have all of the data.
Mark Sutton has pointed out why you are unable to export as PFX - the certificate in question has its private key flagged as non-exportable. The Cryptographic Service Provider (CSP)will not allow that key to be moved, this is intentional. The only* way you can get an exportable cert\key pair is if the original Certificate was issued with the exportable flag set. It is also possible that there is no private key associated with the cert but I'm assuming that that is not the case here.
There is a good summary of the various PKCS types on Wikipedia.
- The only legitimate way at least. Depending on the CSP\Crypto Hardware there may be mechanisms, especially for software only CSP's, but that's an area for security vulnerability research only as far as I'm concerned, not systems admin.
Solution 2
I go through this every 2 years (when I renew a code-signing cert) and it's a pain each time.
A key piece of info is that you can simply rename .p7b files to .spc (as stated here: http://support.microsoft.com/kb/269395).
You can then use the pvk2pfx.exe tool to convert your PVK + SPC into a PFX.
pvk2pfx.exe -pvk input.pvk -pi <existing_input.pvk_password> -spc input.spc -pfx output.pfx -po <new_output.pfx_password>
(you may be able to skip the p7b renaming step & use it directly; I haven't tried...)
Solution 3
With the windows tool if the pfx option is disabled it means that the private key is not able to be exported from the local store. This is either because its not there (because the keys weren't generated on the box your using) or because when you generated the keys the private key was not marked as exportable and the windows certificate template was not configured to allow export.
I'm assuming your using a Microsoft certificate authority to issue your certificates. Is this correct?
If so then:-
1.Make sure that the certificate template allows the export of private keys.
2.How are you generating your certificate request, you can use the following technique
CREATE INF file as follows
[Version]
Signature="$Windows NT$
[NewRequest]
Subject="etc"
KeySpec=1
Exportable=1
MachineKeySet=TRUE
ProviderName="CSPName"
ProviderType=1
[RequestAttributes]
CertificateTemplate=
NOTE the Exportable =1
Then use the fllowing commands at the command prompt
certreq -new infile.inf reqfile.req //where infile.inf is the file above and reqfile is the output request file
certreq -submit -config \ reqfile.req //Submits the cert request to the CA
Once this is complete you will be able to export the cert as a pfx
Alternatively goto http://www.blacktipconsulting.com/Site/Products.html where i've put my free command line tool that does all this for you and exports the cert as pfx once finished
Solution 4
As Helvick pointed out, PKCS10's response is PKCS7 and it does not contain the private key. So while generating the CSR you should have generated privatekey.key file. You can use the following commands. ( I know this is four years old question but I could not do it while following the discussion on the page ).
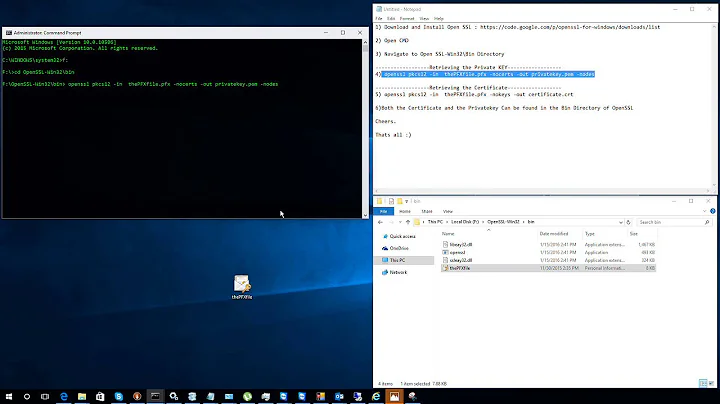
openssl pkcs7 -inform DER -in PK7BDownloadedArchive.p7b -text -print_certs -out intermediateCert.pem openssl pkcs12 -export -in intermediateCert.pem -inkey privateKey.key -out FinalPKCS12Cert.p12
Good luck!
Regards, JE
Solution 5
I could be wrong, but I think your PCKCS#7 file only includes the public half of your certificate.
The PKCS#12 file would need to have both halves - hence why it needs the -inkey option.
Related videos on Youtube
Comments
-
DrStalker over 1 year
I have an SSL certificate in .p7b format that I need to convert to .pfx. If I try this through the windows certificate managment the option to expert as a .pfx is disabled.
Trying with openssl I have found the following two commands to do the conversion:
openssl pkcs7 -print_certs -in certificate.p7b -out certificate.cer openssl pkcs12 -export -in certificate.cer -inkey privateKey.key -out certificate.pfx -certfile CACert.cerbut I'm not sure what key to use for teh esecond command, or what certificate CACert.cer refers to.
How can I convert this key to .pfx format?
-
DrStalker over 14 yearsThanks - looks like buying a new certificate may be cheaper than recovering it, based on the amount of time we'll have to deal with a third-party to do this.
-
Tim about 13 yearsthis is far more useful than the accepted answer. I am amazed at the state of the code signing nonsense. I cringe at the thought of having to repeat this over and over when the certificates expire.
-
palswim about 4 yearsYou may not need the
-informargument.