Cost of getting in-house certificate authority trusted
Solution 1
If I remember correctly, we were quoted something like 150k to start then 75k per year when we looked into this.
Solution 2
To get an idea of actually getting a root certificate trusted, take a look at CAcert's ongoing process. It's been a rather complex multi-year process (and they aren't done), but being an open organization all the details of the process are on their web site.
A more likely options is getting a subordinate CA under one of the big roots. I don't recall which offhand, but at least one had an option a while back for them hosting the subordinate CA (IIRC wisc.edu does this with Equifax/Geotrust). I think the ongoing cost was in the low 5 figures per year plus a few dollars per cert (startup costs not included). I don't have links handy, but several schools have gone this way and have the technical details published either on their web sites or in presentations given at conferences. Working from memory and my cert cache, wisc.edu, lsu.edu, and tmc.edu look like good places to start.
Related videos on Youtube
Milan
Updated on September 17, 2022Comments
-
Milan over 1 year
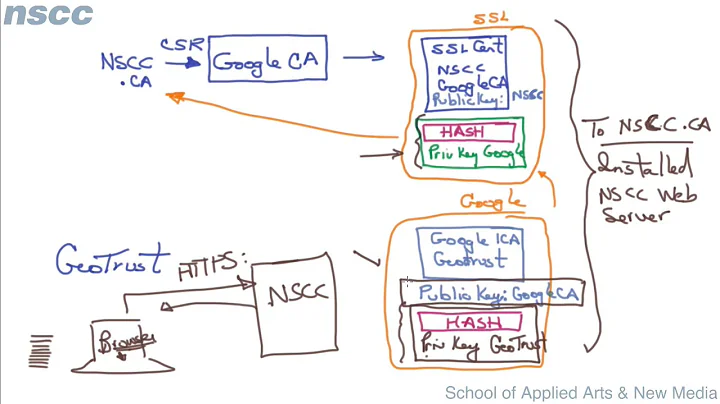
My company has an in-house certificate authority that is currently self-signed. Since we want to start using it for external SSL and secure email to our customers, we need to get it trusted.
Does anyone have a ballpark as to what it costs to get trusted root certificate for an in-house PKI? 4 figures? 5 figures? 6 figures? We employ between 2000-3000.
-
Milan almost 14 yearsWow.. That's some serious coin. Any clue why it costs so much?
-
Zypher almost 14 yearsAnd that is just to get your CA's root cert signed by a well known authority (read already trusted by just about everyone). I have no idea what it would cost to get into the vendor's trusted root stores. There is some VERY heavy duty security that goes into having a trusted root, and that is most of the cost, secondly is it acts as a barrier to entry would be my guess. The cost is second hand knowledge i wasn't involved in the pricing, but my friends where.
-
Kara Marfia almost 14 yearsLooks like annual security audits from places like this - webtrust.org ... I'm guessing that's not the only hoop that needs jumping through.
-
Zypher almost 14 yearsJeremy, the numbers i mentioned where for a subordinate CA so your low 5 figures would be right for ongoing there are MASSIVE startup costs.
-
Anwill almost 14 yearsYea, I should have mentioned that's the per year cost. Thanks for the reminder.
-
Aashraya Singal almost 14 yearsIsn't that kind of setup cost to allow you to issue certificates to other organisations? The OP seems to be asking about issuing certificates underneath a domain he already owns, and already owns a certificate for. Surely you don't have to setup as a complete root CA if you just want to issue certificates for subdomains to your own domain?
-
Milan almost 14 yearsChris is correct. I just want to biggyback on an existing trusted root CA and issue CAs for our domain.
-
Zypher almost 14 years@Chris nope that cost was to piggyback on a trusted root CA.
-
Aashraya Singal almost 14 yearsSo once you obtain a certificate for yourdomain.com, you can't then generate certificates for subdomain.yourdomain.com without setting up a full-blown CA? Oof. My cert knowledge is sketchy, but I'd assumed that was the point of chaining.
-
Zypher almost 14 years@Chris nope ... you need a full blown CA to issue certs, the chaining part comes when a trusted CA signs your CA's cert. It would negate the purpose of certs if you could just get one cert and then have it and anything it signed be trusted by anyone. Getting your CA's certs signed is a big deal.


![[FIX]certificate authority is installed on this device. Your secure network traffic may be modified](https://i.ytimg.com/vi/_jcqP8BTUMo/hqdefault.jpg?sqp=-oaymwEcCOADEI4CSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLD7nlmMcrL1mOfFQW3SYQFNoN0Nkg)
