Enabling cipher TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) on Windows Server 2003+ISA 2006
If your registry change didn't take effect immediately, then just restart your computer.
Related videos on Youtube
Vesper
I'm a hobby programmer, I specialize in common mistakes and blind debugging. I live in Moscow, Russia, and I'm pretty happy with it.
Updated on September 18, 2022Comments
-
 Vesper over 1 year
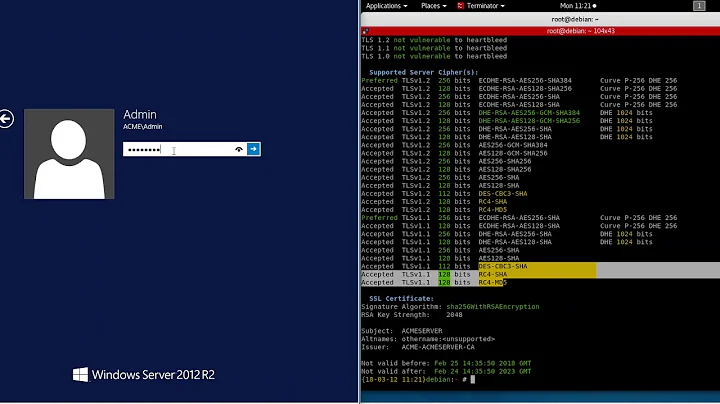
Vesper over 1 yearI have been given a task to disable all "weak" ciphers/protocols on our very old ISA server based on Windows Server 2003. I have disabled all protocols but TLS1.0, and all ciphers but RC2/128, RC4/128 and Triple DES 168/168. But Qualys SSL Labs test utility does not display me that I have a 3DES encryption available on my ISA server. The only cipher suites listed are:
TLS_RSA_WITH_RC4_128_MD5 (0x4) TLS_RSA_WITH_RC4_128_SHA (0x5)This KB says that when Triple DES 168 cipher is enabled, the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher suite is available. However, it is not. We need this cipher suite to allow a Windows 8.1 Phone connecting to ActiveSync published by this ISA. What could be the reason of 3DES encryption to be unavailable in this configuration, and what should we do in order to allow the connection for a Windows 8.1 phone without being vulnerable to POODLE?
EDIT: There was apparently a server-side malfunction of some sort, a reboot fixed 3DES availability, although the same KB states that registry change should have worked at once. I've got another server with the same problem, got it fixed with registry modification only, though.
-
 Michael Hampton over 9 yearsAnd I hope you're ready to decommission that thing. It goes out of support in a few months.
Michael Hampton over 9 yearsAnd I hope you're ready to decommission that thing. It goes out of support in a few months. -
 Vesper over 9 yearsNO :D While the ISA server is about to get decommissioned indeed, the other server is about to last a few more years.
Vesper over 9 yearsNO :D While the ISA server is about to get decommissioned indeed, the other server is about to last a few more years. -
 Vesper over 9 yearsME? No, my BOSS plans to. While I agree about it should be migrated away to more modern platforms, the actual decision hits money wall.
Vesper over 9 yearsME? No, my BOSS plans to. While I agree about it should be migrated away to more modern platforms, the actual decision hits money wall. -
 Michael Bailey almost 9 yearsHe's gonna have to pay a hell of a lot more money when you guys inevitably get hacked, sued, and/or your application breaks. I've attached a rough cost justification as to what may happen should your ISA server be compromised: origin.ih.constantcontact.com/fs195/1118397859495/img/18.gif
Michael Bailey almost 9 yearsHe's gonna have to pay a hell of a lot more money when you guys inevitably get hacked, sued, and/or your application breaks. I've attached a rough cost justification as to what may happen should your ISA server be compromised: origin.ih.constantcontact.com/fs195/1118397859495/img/18.gif -
 Michael Bailey almost 9 yearsBasically what I'm saying is it may be in your best interest to cost justify. Show him the potential outcomes should you guys remain with '03. Infosec pains, IT guys won't even be trained in '03 two years from now is my guess.
Michael Bailey almost 9 yearsBasically what I'm saying is it may be in your best interest to cost justify. Show him the potential outcomes should you guys remain with '03. Infosec pains, IT guys won't even be trained in '03 two years from now is my guess. -
 Vesper almost 9 yearsGiven that a lot of nowadays viruses depend on .NET, having a standalone W2000 server on an obsolete hardware (just enough to carry the workload involved) can be a "security through obscurity" measure against most if not all undirected attacks. Directed attacks are not usually targeted against the front door, but rather target users by spear-phishing, or use a vulnerability on an exposed server of some kind (RDP, HTTP/S, etc). Anyway, I went away from that company already.
Vesper almost 9 yearsGiven that a lot of nowadays viruses depend on .NET, having a standalone W2000 server on an obsolete hardware (just enough to carry the workload involved) can be a "security through obscurity" measure against most if not all undirected attacks. Directed attacks are not usually targeted against the front door, but rather target users by spear-phishing, or use a vulnerability on an exposed server of some kind (RDP, HTTP/S, etc). Anyway, I went away from that company already.
-
-
 Vesper over 9 yearsThat'll be a good solution if that restart won't impact other users en masse. Still, a restart of any Windows system is likely to fix many problems.
Vesper over 9 yearsThat'll be a good solution if that restart won't impact other users en masse. Still, a restart of any Windows system is likely to fix many problems. -
 Vesper almost 9 yearsStill, a restart indeed fixed this stupid problem.
Vesper almost 9 yearsStill, a restart indeed fixed this stupid problem.