Export installed certificate and private key from a command line remotely in Windows using something besides the certmgr.MSC tool
Solution 1
See Stack Overflow question Export certificate from IIS using PowerShell.
If the answer works for you, then you can run PowerShell code on remote server using PSRemoting (Enter-PSSession or Invoke-Command) or psexec.
Does anyone know how to dir the cert store like, "dir cert:\localmachine\my | Where-Object { $_.hasPrivateKey } | " AND then feed that to the certutil export with the thumbprint?
Try this, works for me:
Get-ChildItem -Path 'Cert:\localmachine\My' |
Where-Object { $_.hasPrivateKey } |
Foreach-Object {
&certutil.exe @('-exportpfx', '-p', 'secret', $_.Thumbprint, "$($_.Subject).pfx")
}
Beware, that sometimes you wouldn't be able to use Subject as file name, due to invalid foreign-language characters in the Unicode.
Solution 2
Do this in PowerShell to export the cert from a long list of Windows servers remotely. $servers is a list of servers.
foreach ($server in $servers){
Invoke-command $server {
Get-ChildItem -Path 'Cert:\localmachine\My' |
Where-Object { $_.hasPrivateKey } |
Foreach-Object {&certutil.exe @('-exportpfx', '-f', '-p','your_password',$_.Thumbprint, "d:\$($_.Subject).pfx")}
}
Move-Item -Path \\$server\d$\*.pfx -Destination C:\$server.pfx -Force
}
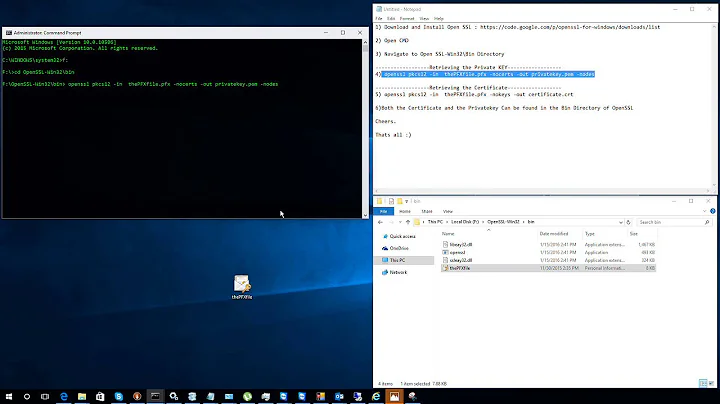
Use Java keytool.exe to turn each pfx file in to a JKS keystore file. Keytool is part of every Java installation. You can do this on your local machine or one the remote server if it already has Java installed.
keytool.exe -importkeystore -srckeystore C:\server1.pfx -destkeystore C:\server1.jks -srcstoretype pkcs12 -deststoretype JKS -srcstorepass your_password -deststorepass your_password
You can also run this with Powershell ($server is the name of the server) ($pwd is a variable holding the password we use to encrypt the file):
foreach ($server in $servers){
& "C:\Program Files\Java\jre6\bin\keytool.exe" -importkeystore -srckeystore C:\$server.pfx -destkeystore C:\$server.jks -srcstoretype pkcs12 -deststoretype JKS -srcstorepass $pwd -deststorepass $pwd
}
Related videos on Youtube
user1991791
Updated on September 18, 2022Comments
-
user1991791 over 1 year
I need to be able to remotely export an installed computer certificate with the full certificate chain and private keys on a Windows server. The cert is used for IIS, and I want to use it for an apache instance running on the same server.
I know how to to do this manually with the certmgr.MSC mmc snap in tool, but how can this be done from a command line or from a remote machine on the same domain?
I also know how to view just the certificate with
openssl s-client. Can that be used to save both the certificate and private key for importing to a Java keystore file?Certmgr via RDP is too slow for what I need. I need a scripting solution.
My environment is all Windows Server 2008 R2. PowerShell remoting is not on, but I can get it on.
I have confirmed that I cannot use the
PowerShell Export-PfxCertificate, because my servers are not new enough...So, if I can use PowerShell to get the thumbprint of the certificate I want, I can then feed it to the "certutil -exportpfx" command. I have confirmed that will work.
How do I dir the certificate store like, "dir cert:\localmachine\my | Where-Object { $_.hasPrivateKey } | " AND then feed that to the certutil export with the thumbprint?
OR, could I do the dir first and tell it to only print out the thumbprint and not the whole thing? Then save that to a file, and read the file a make the certutil command?
-
user1991791 about 9 yearsThanks. The problems with that are its not command line, its very slow, keyboard automation is tricky because its slow, and when you export remotely in the console it won't let you include the private keys.
-
 megamorf about 9 yearsfor command line automation you need to tell us more about your environment. Are you using server 2012 (R2)? Is powershell remoting enabled?
megamorf about 9 yearsfor command line automation you need to tell us more about your environment. Are you using server 2012 (R2)? Is powershell remoting enabled? -
user1991791 about 9 yearsMy environment is all Windows Server 2008 R2. Powershell remoting might be on? How do I test?
-
user1991791 about 9 yearsNevermind, I am testing now to determine if I will be able to use Enter-PSSession Remoting..
-
 megamorf about 9 yearsopen a powershell console wtih admin permissions and enter the following command: enter-pssession -computername "remoteserver" where remoteserver is a system you're trying to connect to via powershell remoting. If you receive an error saying that the connection failed it's disabled, if your prompt changes and includes the remote server name it's enabled.
megamorf about 9 yearsopen a powershell console wtih admin permissions and enter the following command: enter-pssession -computername "remoteserver" where remoteserver is a system you're trying to connect to via powershell remoting. If you receive an error saying that the connection failed it's disabled, if your prompt changes and includes the remote server name it's enabled. -
user1991791 about 9 yearsOK, it is not enabled BUT I can enable it. So, yes assume it can be used..
-
user1991791 about 9 yearsThat is pretty darn close, but for my specific purpose it actually doesn't work. When I first do PS Remote connection with Enter-PSSession, and then run the certutil -exportpfx THAT works. I get a pfx file that when I import it with with Java keytool to a keystore file, the application that uses it is happy.. When I use that PS code I do get a valid pfx file, but it is missing something... The file is a little smaller and when I import it to the keystore file, it mostly works, BUT the application says that the certificate is Pending Approval.
-
user1991791 about 9 yearsI think that PS command is not getting the whole cert chain? The certutil command works, but its not nearly as elegant as this PS command. The PS command will both find the cert I need and export it, while with the certutil I have to first find the cert by its crazy long guid name
-
user1991791 about 9 yearsSo, I just need to figure out how to run that PS command with ChainOption -Force and Extended Properties.. technet.microsoft.com/en-us/library/hh848635.aspx
-
 beatcracker about 9 yearsI'm not sure that
beatcracker about 9 yearsI'm not sure thatExport-PfxCertificatewill work for you, because this page says it applies to: Windows 8.1, Windows PowerShell 4.0, Windows Server 2012 R2. And you're using 2008 R2. -
user1991791 about 9 yearsIs is possible to feed the first half the cert store dir Foreach-object to the certutil command?
-
 beatcracker about 9 yearsYes, I've updated my answer, see if it works for you.
beatcracker about 9 yearsYes, I've updated my answer, see if it works for you. -
user1991791 about 9 yearsOh snap, I have a good feeling about that.. How would I save the pfx to the root of d:\ ? like "d:\$($_.Subject).pfx")
-
 beatcracker about 9 yearsYep,
beatcracker about 9 yearsYep,$($_.Subject)is certificate's subject, anything else around it in quotes is just strings to form a path. So you can do:"d:\my\favorite\folder\$($_.Subject).pfx". -
user1991791 about 9 yearsOhh heck yeah. That works perfectly. The cert is now recognized as signed and fully valid when I import to the Java keystore file. THANK YOU! THANK YOU! THANK YOU! YOU ROCK! HAVE A GREAT DAY!