file ownership for new files with administrator - why is it giving ownership to the group administrators?
Solution 1
Update: This GP setting is no longer available starting with Vista/Server 2008. https://support.microsoft.com/en-us/kb/947721
A Group Policy setting is not available in the security policy settings list on a computer that is running Windows Server 2008
SYMPTOMSWhen you try to access the "System objects: Default owner for objects created by members of the Administrators group" Group Policy setting on a computer that is running Windows Vista or newer, this setting is not available in the security policy settings list. When the setting is present in your security group policy, it will be ignored by Windows Vista and newer domain members.
CAUSEWindows Vista, Windows 7, Windows Server 2008 and Windows Server 2008 R2 do not support this setting any longer. When enabled, User Account Control (UAC) will ensure the user account is being used as owner for all objects created locally. For remote access, the administrators group will be used there is no restricted token for network sessions.
Since the support for the setting was removed, the system security policy "System objects: Default owner for objects created by members of the Administrators group" setting is not available in the Security Templates user interface anymore.
Have a look in Group Policy for the setting "System objects: Default owner for objects created by members of the Administrators group". It's located under:
- Computer Configuration
- Windows Settings
- Security Settings
- Local Policies
- Security Options
- Local Policies
- Security Settings
- Windows Settings
When this setting is enabled members of the "Administrators" group will have objects they create set with the owner "Administrators".
To be honest, I'm not immediately sure on Microsoft's rationale for this behaviour, except to say that it would allow for a common ability to reset permissions on objects w/o taking ownership by all "Administrators". I'd guess that was the intent. I'd be interested to see if anybody has a link to an explicit statement of purpose on this setting from Microsoft.
I noticed that this setting's default differs between Windows XP and Windows Server 2003 (here's an article from Microsoft on it http://support.microsoft.com/kb/318825), but I still don't see a statement of purpose behind why you would want things set one way versus the other.
Solution 2
The difference between XP and Vista/7 default ownership settings relates to the introduction of UAE (better security). Under UAE an administrator is effectively demoted to a limited user account, thereby, restricting any administrator account's ability to change OS settings for files not owned by it. When UAE detects a change requiring administrative privileges, it prompts the user to escalate the account's security token to the increased privileges offered by the account's role as an administrator. You can either decline or accept the UAE request. Unfortunately, even when running with UAE, a demoted administrative account can still affect OS settings by changing files it owns. Ownership of a resource grants full access to this resource even when other permission settings do not. To circumvent this security hole, Vista/7 files created by any specific administrator are now owned by the Administrators group. Therefore individual administrators can no longer change any files without first being promoted to the administrators group.
Before UAE in Vista/7 you could effectively simulate this scheme by using a program called "Drop My Rights". It was developed by a MS engineer and freely distributed by MS. However, before installing the program, you needed to change the registry settings to establish the default Administrator owner to be the Administrators group, so future program installs would set the Administrators group as the owner, as well as alter the file ownership of files in the Windows and Program File directories using the subinacl.exe utility to change the ownership of existing files to the Administrators group.
I would not change the default owner setting unless you wish to introduce a security vulnerability.
Related videos on Youtube
Brian R. Bondy
About me: Work mostly with C++, Python, C#, Win32 Programming for 15+ years; Graduate of the University of Waterloo; Married with twins boys and a red tri-colored border collie Links: Blog/Personal website; Twitter: @brianbondy; African monkey vs European monkey throwing force;
Updated on September 17, 2022Comments
-
Brian R. Bondy over 1 year
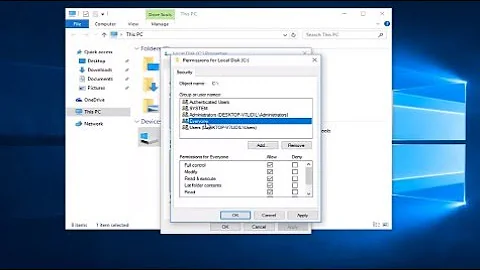
I am logged in as administrator and I right click on a folder and then go to properties, then the security tab, then advanced, then the owner tab. I am not on a domain.
I see that the folder has a group ownership of administrators.
I change this ownership of this item and all subitems to the user administrator. I verified and all subitems do indeed now have the ownerhip of administrator.But then I try to create a new txt file inside that folder, and when I go to see what the ownership is on it, it is administrators. I expected the new ownership to inherit the ownership from it's parent item or take it from me the logged on user administrator.
What can be done to solve this problem so that new files I create when logged on with administrator will create them with an owner of administrator instead of administrators?
-
surfasb over 12 yearsIt becomes obvious once you realize what kind of privileges ownership of an object entails to you.
-
colemik over 12 yearsIn Windows XP, the 'System objects: Default owner [...]' policy setting is: 'Object creator' (as opposed to 'Administrators group') so the author of the question is probably using Windows Server 2003 instead of Windows XP.
-
starfry over 9 yearsDoes this option exist on Windows 7? My gpedit doesn't list it in the path given in the answer.
-
Wouter about 9 yearsIt's no longer available in Windows Server 2012. technet.microsoft.com/en-us/library/cc775434(v=ws.10).aspx