FortiGate IPsec VPN: Configuring Multiple Phase 2 Connections (Multiple Subnets)
Solution 1
1 & 2) You are correct that you need two phase 2s, in some instances. For instance, when dealing with additional security (previous in the flow to firewall policies, for example), splitting two subnets across two phase 2s is required. Unless you don't have this complexity and can create quick mode selectors wide enough to encompass the two subnets within the same phase 2.
3) Multiple phase 1s? Yes. It will drop like you describe. Multiple phase 2s with the same phase 1? It will not drop.
I do not know openswan, but the FortiOS supports at least the IPsec specs. Your best bet is to debug on both sides and see exactly what is going on.
Solution 2
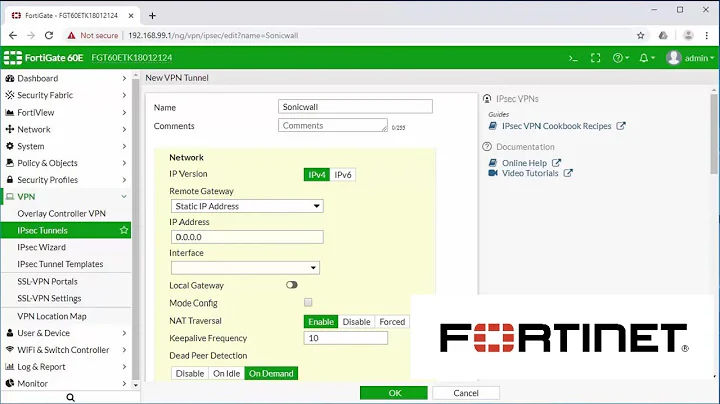
I cannot help you on the OpenSwan side, but I recently had to connect a Cyberoam to a Fortigate with multiple subnets as well. For each subnet, you can create another phase 2 (bound to the same phase 1 object):

Here's an example of such a phase 2 object:

In the quick mode selector section, specify the local address and subnet, that's what is different with the other phase 2 objects. In my case, I've created address objects (under firewall menu) for reusability.
On our fortigate, we use a different physical port for each subnet, so we created a VPN policy for each subnet:

I hoipe this helps you on the fortigate side of things.
PS: I've renamed most of the things on the screenshot, it's better to give more meaningful names.
Related videos on Youtube
FixMaker
Updated on September 18, 2022Comments
-
FixMaker over 1 year
I am trying to make an IPsec connection to a FortiGate router using OpenSwan. The FortiGate sits on two distinct subnets and I need to access both of them. In the FortiGate I have defined one Phase 1 connection and one Phase 2 connection. This allows me to successfully make a connection to one of the subnets.
I need to be able to access both subnets at the same time. The received wisdom seems to be to create two separate connections (one per subnet) in OpenSwan and when making an additional connection it will automatically attempt to reuse an existing phase 1 tunnel (when creating a new phase 2 tunnel for the additional connection).
When I bring up both connections, according to the logs it seems OpenSwan is stuck in a continuous loop of attempting renegotiate each connection in turn (I can only ping one subnet at any one time). I'm guessing this is because the FortiGate is dropping the existing connection when a new one is attempted.
I have the following questions:
How should I configure the FortiGate to allow two concurrent connections from the same IPsec initiator (one connection per subnet)? Is this even possible? (The documentation seems to be a bit vague on this.)
Do I need to specifically associate a phase 2 connection in the FortiGate to a specific subnet, and if so, how do I go about doing this?
Are there any issues/gotchas when making multiple IPsec VPN connections between the same endpoints?
-
Terry over 9 years1 phase 1, 3 phase 2 solved my issue. Thanks for this info.
-
FixMaker over 9 years@Terry, did you do this on a FortiGate?
-
Terry over 9 years@Lorax: Indeed, made a phase 1 connection to our address (Cyberoam firewall), then connected 3 phase 2 objects to that same phase 1 object. Also don't forget to add a VPN policy for each phase 2 you create.
-
 Christophe Drevet over 4 yearsThanks for your input. However, it seems to better fit as a comment than an answer. For example, the "above answer" is not meaningful since answers' order will most likely change with votes.
Christophe Drevet over 4 yearsThanks for your input. However, it seems to better fit as a comment than an answer. For example, the "above answer" is not meaningful since answers' order will most likely change with votes.