Generating an SHA256 SSL CSR on CentOS/RHEL using genkey
Solution 1
The interactive genkey command wont give you the option to change the defaults, but you should be able to update your /etc/pki/tls/openssl.cnf if you really want to use that command.
Change:
default_md = sha1
To:
default_md = sha256
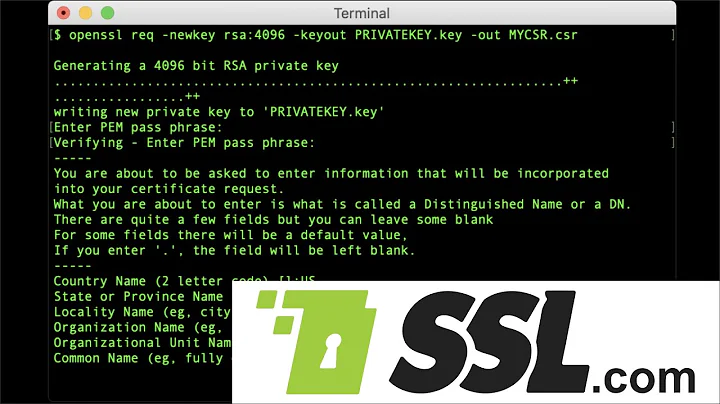
Or you can use the openssl command direct. If the hashing algorithm is set to SHA1 by default, you can use the switch -sha256 to force SHA2.
openssl req -new -sha256 -key private.key > new_sha256.csr
Solution 2
The signature you are referring to is found in the SSL Certificate, not the CSR. This is why you can't find the option. :)
What you need to do is make sure your Certificate Issuer is generating your certs based off of your CSR with the correct options. The exact method to do so changes from CA to CA. For example, GoDaddy generally have a drop-down box on the certificate request screen right under where you paste your CSR, and you can select SHA-1 or SHA-2(which will generate the SHA256 cert).
Related videos on Youtube
steevithak
Updated on September 18, 2022Comments
-
steevithak almost 2 years
The officially recommended method of generating a web server SSL certificate CSR (according to RHEL6 and CentOS 6 documentation) is to use the genkey utility. When used according to the docs, this produces a CSR with an SHA1 signature. Our CA has requested a CSR with an SHA256 signature (because we want an SHA256 SSL cert as per the new chrome/ie browser requirements). I've not been able to find any docs on how to do this using genkey. I tried the --sha256 command line flag but it's not recognized by genkey. Can anyone describe how to do this?
-
steevithak almost 10 yearsSo, I gather it's not possible to generate a CSR with SHA256 sig on RHEL/CentOS? (I understand it may not necessary but I'd still like to know how to do it if it's possible)
-
-
steevithak almost 10 yearsSo I think you're saying I can get an SHA256 signed cert using an SHA1 signed CSR, is that correct?
-
 Unix-Ninja almost 10 yearsYes, that is correct. I just re-keyed 3 SSL certs for this on Friday. All of the CSRs have SHA1 RSA signatures in them, but the actual certs we requested are signed with SHA256 (SHA2 family).
Unix-Ninja almost 10 yearsYes, that is correct. I just re-keyed 3 SSL certs for this on Friday. All of the CSRs have SHA1 RSA signatures in them, but the actual certs we requested are signed with SHA256 (SHA2 family). -
steevithak over 9 yearsChanging the default_md value didn't work - it caused genkey to use MD5 instead of SHA1. However, generating the CSR directly with the openssl -sha256 command you provided worked perfectly. Thanks!
-
Unknown_Guy about 9 yearsAdded
default_md = sha256in[ req ]and it worked when using conf file.