Getting auditd to record the original user
Solution 1
As stated here:
Using
session required pam_loginuid.so
in all login related PAM config files (not the ones for su and sudo) will let auditd log the calling user's uid in the field auid.
You can search auditd's logs for this id with
ausearch -ua <uid>
yielding all commands the user issued, even while impersonating another account.
Solution 2
The information you're requesting is, joyfully, already included in the logs. The specific field that you want to look for is aud. From the manpage for auditctl:
auid The original ID the user logged in with. Its an abbreviation of audit uid. Sometimes its referred to as loginuid. Either the user account text or number may be used.
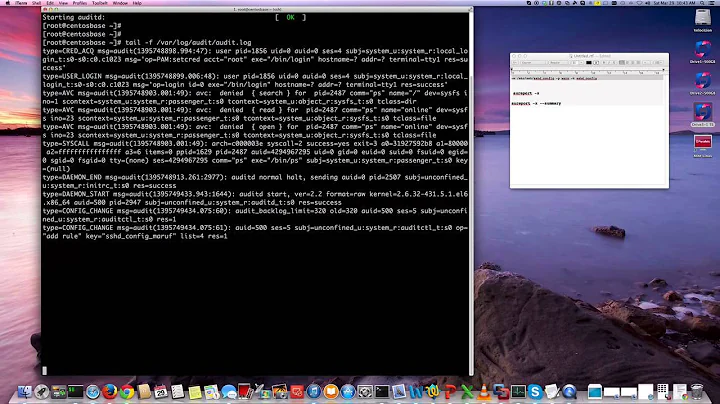
As an example, here is a lot entry that I generated using the following methodology:
- Add the rule:
-a always,exit -S sethostname -S setdomainname -k system-locale - Login to the system with my user account and launch a root shell by issuing
su - - Execute the command:
hostname audit-test.home.private
type=SYSCALL msg=audit(1358306046.744:260): arch=c000003e syscall=170 success=yes exit=0 a0=2025010 a1=17 a2=7 a3=18 items=0 ppid=23922 pid=26742 auid=1000 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts4 ses=16 comm="hostname" exe="/usr/bin/hostname" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key="system-locale"
So, while yes, the log message is quite verbose we can clearly see auid=1000 in the log message, which corresponds to the uid of my user account.
For more details on the above example, as well as a brief description of auditd, check out this blog post from IT Security a community blogger (me) imaginatively entitled A Brief Introduction to Auditd.
The ausearch command mentioned by fuero is part of a suite of applications used to search and run reports against these rather thorough logs.
Related videos on Youtube
Soviero
Updated on September 18, 2022Comments
-
 Soviero almost 2 years
Soviero almost 2 yearsThis question is related to my previous question: Log all commands run by admins on production servers
It is company policy for admins to login to the servers via a personal username, and then run
sudo -ito become root. Upon runningsudo -i, sudo will create an environmental variable calledSUDO_USER, which contains the original user's username.Is it possible to have
auditdinclude this variable in it's logs for each command? Or a functional equivalent.This is the current rule set for
auditd:# First rule - delete all -D # Increase the buffers to survive stress events. # Make this bigger for busy systems -b 320 # Log any command run on this system #-a exit,always -F arch=b64 -S execve -a exit,always -F arch=b32 -S execve-
 Soviero over 11 years@AaronCopley I skimmed through it, but I didn't see anything allowing me to include a custom variable (such as
Soviero over 11 years@AaronCopley I skimmed through it, but I didn't see anything allowing me to include a custom variable (such asSUDO_USER) in the log... -
 Soviero over 11 years@AaronCopley Not a problem, it was still very useful in it's own right. Thank you.
Soviero over 11 years@AaronCopley Not a problem, it was still very useful in it's own right. Thank you. -
 Soviero over 11 years@cstamas That was indeed useful. However, on my Ubuntu 12.04 workstation, it did not seem to work.
Soviero over 11 years@cstamas That was indeed useful. However, on my Ubuntu 12.04 workstation, it did not seem to work. -
fuero over 11 years@Kevin: did you look at my answer at your original post? it seems to me like it covers your issue. Could you perhaps elaborate why it doesn't? (and perhaps accept an answer)
-
 Soviero over 11 years@fuero This question was posted before you had posted your answer, and the original question had become stale and the existing answers didn't answer the whole question. I am still waiting to get my hands on a CentOS sandbox at work, and will accept your answer when I've had a chance to test it. Thank you for your answer though.
Soviero over 11 years@fuero This question was posted before you had posted your answer, and the original question had become stale and the existing answers didn't answer the whole question. I am still waiting to get my hands on a CentOS sandbox at work, and will accept your answer when I've had a chance to test it. Thank you for your answer though.
-