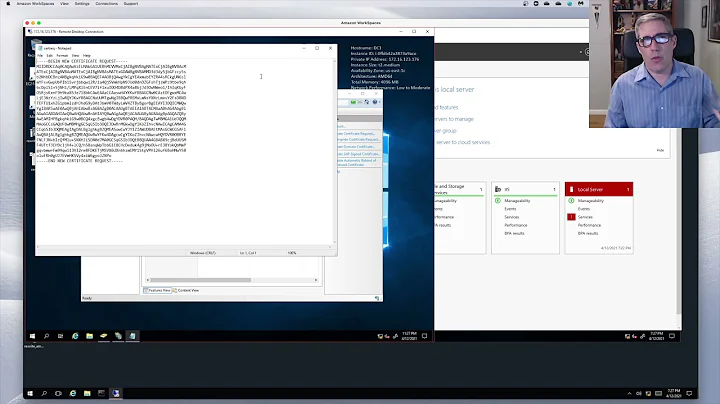
Getting CentOS 6 to trust a certificate from AD
You need to trust the certificate which signed the certificate you are presented with. Typically this will be the trust root (the CA certificate) which you can get from the certificate store of a computer running AD CS, though it may also be an intermediate (in which case the whole chain should be presented, so the trust root is still the one to trust). You should be able to simply concatenate the certificate onto the end of /etc/openldap/cacerts/some_pem_file.pem and have things work.
Related videos on Youtube
John Hunt
Updated on September 18, 2022Comments
-
John Hunt over 1 year
I'm trying to get my CentOS server to trust a certificate I've installed from an active directory server (I converted the .cer to .pem earlier.)
When I try to connect, the debug information is:
[root@web1 cacerts]# ldapsearch -d1 -v -D SOMEDN\pretenduser01 -w SOMEPASSWORD -H ldaps://1.2.3.4:636 -x ldap_url_parse_ext(ldaps://1.2.3.4:636) ldap_initialize( ldaps://1.2.3.4/??base ) ldap_create ldap_url_parse_ext(ldaps://1.2.3.4:636/??base) ldap_sasl_bind ldap_send_initial_request ldap_new_connection 1 1 0 ldap_int_open_connection ldap_connect_to_host: TCP 1.2.3.4:636 ldap_new_socket: 3 ldap_prepare_socket: 3 ldap_connect_to_host: Trying 1.2.3.4:636 ldap_pvt_connect: fd: 3 tm: -1 async: 0 TLS: certdb config: configDir='/etc/openldap/cacerts' tokenDescription='ldap(0)' certPrefix='' keyPrefix='' flags=readOnly TLS: using moznss security dir /etc/openldap/cacerts prefix . TLS: loaded CA certificate file /etc/openldap/cacerts/some_pem_file.pem. TLS: certificate [CN=SRV-DC3-RG.hiddendomain.co.uk] is not valid - error -8179:Peer's Certificate issuer is not recognized.. TLS: error: connect - force handshake failure: errno 21 - moznss error -8179 TLS: can't connect: TLS error -8179:Peer's Certificate issuer is not recognized.. ldap_err2string ldap_sasl_bind(SIMPLE): Can't contact LDAP server (-1)I don't really know what the next steps are in solving this.. I can connect just fine without SSL but that's not really very good :)
-
John Hunt almost 11 yearsWill give that a try, now it's just waiting for our client to provide said certificate...
-
Falcon Momot almost 11 yearsThe way in which you trust it is adding it to the trust root. You cannot cross-certify the certificate, but you can add the certificate which signed it (normally provided in the chain presented when you connect) to your trust root.