How can user mount an encrypted file container in VeraCrypt?
Solution 1
I did it. The solution's adapted from here: https://wiki.archlinux.org/index.php/TrueCrypt#Mount_volumes_as_a_normal_user and from my other question regarding modern sudoers config: adding local content in /etc/sudoers.d/ instead of directly modifying sodoers file via visudo
- Create a new group called say
veracryptusersand give it the necessary permissions to use VeraCrypt without root password. Any user that belongs to that group will be able to use VeraCrypt.
Note: this dramatically increases attack surface for user rights elevation, so be sure to add only trusted users to this group.
# groupadd veracryptusers
- Now let's give this group sudo permissions limited to VeraCrypt:
$ sudo visudo -f /etc/sudoers.d/veracrypt GNU nano 2.5.3 File: /etc/sudoers.d/veracrypt.tmp # Users in the veracryptusers group are allowed to run veracrypt as root. %veracryptusers ALL=(root) NOPASSWD:/usr/bin/veracrypt
Also please make sure that veracrypt and /usr/bin have the proper permissions and are NOT writable by groups nor others:
$ ls -al /usr/bin/vera* -rwxr-xr-x 1 root root 6341016 paź 17 2016 /usr/bin/veracrypt $ ls -ald /usr/bin drwxr-xr-x 2 root root 69632 lip 25 10:09 /usr/bin
Otherwise a malicious user may replace the executable and gain total root right at his wish.
Now reboot (or relogin) to have groups membership revaluated and voilà - you can mount and unmount your favourite volumes.
Please also be sure to review privilege escalation loophole described at the link below and before adding users to the group consider whether you can trust them
Solution 2
Warning: Only use @Pawel Debski solution if agree the following:
- Any user or hacker getting access to an user account in veracryptusers group can run any commands as root, by downloading a prepared container file containing malicious code running as root.
So using that solution you might consider to use a special user profile for veracrypt. As a result, sodo is easier to use.
Steps to test the security problem:
- Create a container file (ext2-4)
- Copy or create a binary file (e.g. whoami)
- Change binary owner to root
- Add setuid to the binary
- Call the binary with a non-root-user account
The binary will run with root privilege.
Hint: I added this solution as the warning at Pawel Debski is inconspicuously. The risk is much greater than the benefit as long as the system has an internet connection.
Related videos on Youtube
Pawel Debski
Salesforce, Cornerstone on Demand, GxP Validation, TIBCO, WebMethods, SAP, Java, Microsoft.Net C#, SQL, Oracle, Informatica, Business Objects, IT Outsourcing To join us: cv ! econsulting @ pl To contract us: salesteam ! econsulting @ pl
Updated on September 18, 2022Comments
-
 Pawel Debski 5 months
Pawel Debski 5 monthsI have a number of external media with VeraCrypt encrypted file containers and I would like the users to mount and use them without giving root privileges to the users.
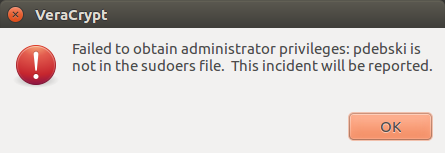
However at the moment VeraCrypt's always asking for user/admin password apparently sudo-ing mount operation:
How can a user, who's not in the sudoers file mount an .hc file?
-
 Tom K. almost 5 years
Tom K. almost 5 years -
 forest almost 5 yearsThis answer is incorrect and will lead to trivial privilege escalation. As I answered in the link @TomK. provided, this solution provides no protection and will be giving anyone in the
forest almost 5 yearsThis answer is incorrect and will lead to trivial privilege escalation. As I answered in the link @TomK. provided, this solution provides no protection and will be giving anyone in theveracryptusersgroup full root access. Do not do this. -
 Pawel Debski over 4 yearsIt is a very good idea to add this as an answer. Tx.
Pawel Debski over 4 yearsIt is a very good idea to add this as an answer. Tx. -
 Pawel Debski over 3 yearsRussel, read carefully priviledge escalation descriptions from other answers. Your solution does not address the problem and there is no way to avoid the loophole. Both answers are applicable to personal system or when you're working with trusted users.
Pawel Debski over 3 yearsRussel, read carefully priviledge escalation descriptions from other answers. Your solution does not address the problem and there is no way to avoid the loophole. Both answers are applicable to personal system or when you're working with trusted users. -
 Pawel Debski almost 2 yearsIt is not if you trust the users. If you had a malicious user or a system would be somehow exposed, for example accessible to anyone in a lobby, obviously you'd not use the solution proposed. If you had a knife you can make a sandwich or you can cut yourself. It is up to you.
Pawel Debski almost 2 yearsIt is not if you trust the users. If you had a malicious user or a system would be somehow exposed, for example accessible to anyone in a lobby, obviously you'd not use the solution proposed. If you had a knife you can make a sandwich or you can cut yourself. It is up to you. -
 Zanna over 1 yearIf you want people to answer you as to whether this is a good plan, I suggest posting it as a question instead of as an answer (I'd tell you in this comment if I knew, but unfortunately I don't)
Zanna over 1 yearIf you want people to answer you as to whether this is a good plan, I suggest posting it as a question instead of as an answer (I'd tell you in this comment if I knew, but unfortunately I don't)