How do I set up SFTP file access logging for OpenSSH?
Solution 1
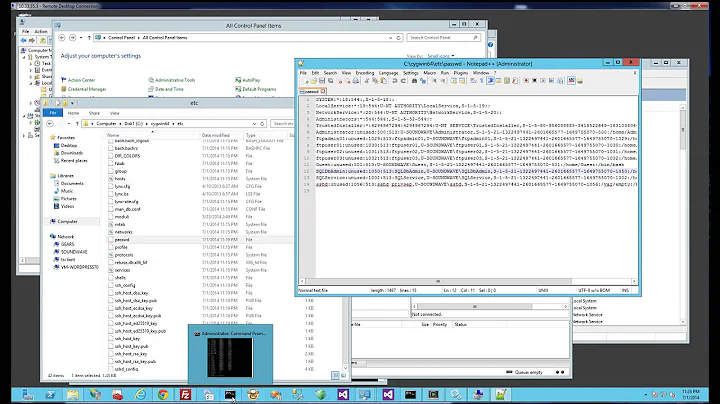
By default sshd logs to the system logs, with log level INFO and syslog facility AUTH. So the place to look for log data from sshd is in
/var/log/auth.log
These defaults can be overridden using the SyslogFacility and LogLevel directives. Below is a typical server startup entry in the authorization log.
In most cases the default level of logging is fine.
The following should give you only ssh related log lines
grep 'sshd' /var/log/auth.log
To be on the safe side, get the last few hundred lines and then search (because if the log file is too large, grep on the whole file would consume more system resources, not to mention will take longer to run)
tail -500 /var/log/auth.log | grep 'sshd'
EDIT:
From man sshd_config
LogLevel
Gives the verbosity level that is used when logging messages from
sshd(8). The possible values are: QUIET, FATAL, ERROR, INFO,
VERBOSE, DEBUG, DEBUG1, DEBUG2, and DEBUG3. The default is INFO.
DEBUG and DEBUG1 are equivalent. DEBUG2 and DEBUG3 each specify
higher levels of debugging output. Logging with a DEBUG level
violates the privacy of users and is not recommended.
so you can change this parameter in sshd_config. But seems it doesn't track files.
You can investigate a bit though:
1) To find all files NOT owned by your logged on user in your home folder, type:
find ~ -type f ! -user $USER
1.1) To find all files that do not belong to any legitimate user (they should not exist), type:
find ~ -type f -nouser
2) As files on the system have three timestamps called mtime (file modification time), ctime (inode change time and permissions), and atime (file access time), these can be queried to find out how files have been modified. It is often debated which of these are the best to use, but probably the best way to find out when files were accessed or modified is to use the find command to search atime and mtime, with which you specify days ago, and the additional find options amin and mmin, with which you specify minutes ago.
For each of these commands, the same command switches are used: for example,-atime 1 will match those files that were accessed exactly 1 day ago; to specify more or less than, append a + or a - respectively. The examples below may clarify all this (specify -type d for directories):
find ~ -type f -atime 1
find ~ -type f -amin -23
find ~ -type f -mtime 2
find ~ -type f -mmin -45
To combine my approaches so far, you could enter the following commands from your home folder; the first searches for files accessed by a person who is NOT your user, and the second for any files modified by persons other than by your user less than two days ago.
find ~ -type f -atime -2 ! -user $USER
find ~ -type f -mtime -2 ! -user $USER
Solution 2
In your sshd_config (mostly /etc/ssh/sshd_config), Try something like
Subsystem sftp internal-sftp -f AUTH -l INFO
or
Subsystem sftp internal-sftp -l INFO
I think these are the logging levels:
QUIET, FATAL, ERROR, INFO, VERBOSE, DEBUG, DEBUG1, DEBUG2, and DEBUG3
If you need more details on log, increase the logging level
Solution 3
You can use a wrapper around you sftp-server executable as such :
`
#!/bin/sh
# sftpd wrapper script for executing pre/post session actions
# pre session actions and logging here
SOURCE_IP=${SSH_CLIENT%% *}
MSG_SESSION_START="user $LOGNAME session start from $SOURCE_IP"
logger -p local5.notice -t sftpd-wrapper -i "$MSG_SESSION_START"
# start actual SFTP session
/usr/libexec/openssh/sftp-server
# add post session actions here
`
... And then, adjust your syslogd.conf configuration to direct the local5.notice to a proper logfile, as such:
local5.* /var/log/sftpd.log
And lastly, to see which files are being transferred, you can adjust globally in sshd_config; or per-user by adjusting the above script, simply by adding the following setting to make the sftp subprocess log the files being transfered:
/usr/libexec/openssh/sftp-server -f local5 -l info
hope this helps ! :p
Related videos on Youtube
kraxor
Updated on September 18, 2022Comments
-
kraxor over 1 year
I have an SFTP setup using the built-in sftp-subsystem of OpenSSH with chrooted users.
In the old days when I used to use FTP, I was able to see what files were accessed by users in the logs.
How do I achieve the same using OpenSSH/SFTP?
Relevant parts of my
/etc/ssh/sshd_config:Subsystem sftp internal-sftp Match group sftponly ChrootDirectory /home/%u X11Forwarding no AllowTcpForwarding no ForceCommand internal-sftp -
kraxor almost 10 yearsThanks, but I can only see "session open" and "session close" messages in
/var/log/auth.log. What I'm looking for is a file access log. -
 Ruslan Gerasimov almost 10 yearsI added some info to the answer.
Ruslan Gerasimov almost 10 yearsI added some info to the answer. -
 Andre Leon Rangel over 4 yearsthank you for your answer but the user wants to know how to achieve the logging of the file operations for users with a Chroot jail...
Andre Leon Rangel over 4 yearsthank you for your answer but the user wants to know how to achieve the logging of the file operations for users with a Chroot jail... -
 Andre Leon Rangel over 4 yearsyes but the user is in a Chroot jail and requires a little extra.
Andre Leon Rangel over 4 yearsyes but the user is in a Chroot jail and requires a little extra. -
 Andre Leon Rangel over 4 yearsdo you require some permissions in the jail folder? in ubuntu18 there is
Andre Leon Rangel over 4 yearsdo you require some permissions in the jail folder? in ubuntu18 there is/etc/rsyslog.dand/etc/rsyslog.conf