How should I change encryption according to *** WARNING : deprecated key derivation used
Solution 1
Comparing the Synopsys of the two main and recent versions of OpenSSL, let me quote the man pages.
OpenSSL 1.1.0
openssl enc -ciphername [-help] [-ciphers] [-in filename] [-out filename] [-pass arg] [-e] [-d] [-a/-base64] [-A] [-k password] [-kfile filename] [-K key] [-iv IV] [-S salt] [-salt] [-nosalt] [-z] [-md digest] [-p] [-P] [-bufsize number] [-nopad] [-debug] [-none] [-engine id]
OpenSSL 1.1.1
openssl enc -cipher [-help] [-ciphers] [-in filename] [-out filename] [-pass arg] [-e] [-d] [-a] [-base64] [-A] [-k password] [-kfile filename] [-K key] [-iv IV] [-S salt] [-salt] [-nosalt] [-z] [-md digest] [-iter count] [-pbkdf2] [-p] [-P] [-bufsize number] [-nopad] [-debug] [-none] [-rand file...] [-writerand file] [-engine id]
There obviously are some greater differences, namely considering this question, there are these two switches missing in the 1.1.0:
-
pbkdf2 -
iter
You have basically two options now. Either ignore the warning or adjust your encryption command to something like:
openssl enc -aes-256-cbc -md sha512 -pbkdf2 -iter 100000 -salt -in InputFilePath -out OutputFilePath
Where these switches:
-
-aes-256-cbcis what you should use for maximum protection or the 128-bit version, the 3DES (Triple DES) got abandoned some time ago, see Triple DES has been deprecated by NIST in 2017, while AES gets accelerated by all modern CPUs by a lot; you can simply verify if your CPU has the AES-NI instruction set for example usinggrep aes /proc/cpuinfo; win, win -
-md sha512is the faster variant of SHA-2 functions family compared to SHA-256 while it might be a bit more secure; win, win -
-pbkdf2: use PBKDF2 (Password-Based Key Derivation Function 2) algorithm -
-iter 100000is overriding the default count of iterations for the password, quoting the man page:Use a given number of iterations on the password in deriving the encryption key. High values increase the time required to brute-force the resulting file. This option enables the use of PBKDF2 algorithm to derive the key.
Solution 2
The other answer is essentially correct. though other things have changed around these versions (v1.1.0 and v1.1.1) that is good to be aware of.
First the default password hashing digest has changed, going from md5 to sha512
And second the addition the "-pbkdf2" "-iter" which has been needed for a long time. However the default iteration count is far too low, and should be set as high as possible without becoming too annoying. Big enough to take 1 to 2 seconds is generally acceptable for both encrypting and decrypting, but makes it very very difficult for brute forced password guessing.
The problem is now we have all these new options and defaults, as well as different digests and cyphers, you need to remember all these options do you can decrypt the encrypted file. That is whatever options was decided on to encrypt must be used to decrypt. However openssl only stores some 'file magic' (EG "Salted__" at the start of the file), and the random "salt" that was used, with the encrypted file. It leaves it up to you to remember everything else!
Aespipe is a old program that got around this by saving some of this information as a extra header to the encrypted data, but it is now becomming dated, and its format does not allow for the new options, or for easy expansion.
As a alternative I have been creating a new script "keepout" as a wrapper around "openssl enc" to save those extra options that is needed to remember how to decrypt that specific file, even as newer options, cyphers, or larger iterations are used when encrypting. Basically it saves the openssl option needed with the data.
https://antofthy.gitlab.io/software/#keepout
Related videos on Youtube
Tommy Pollák
Retired (manager of) developers for Univac 1100, DEC-PDP 11, DEC VMS, Solaris, HP-Unix now playing around on Ubuntu.
Updated on September 18, 2022Comments
-
Tommy Pollák over 1 year
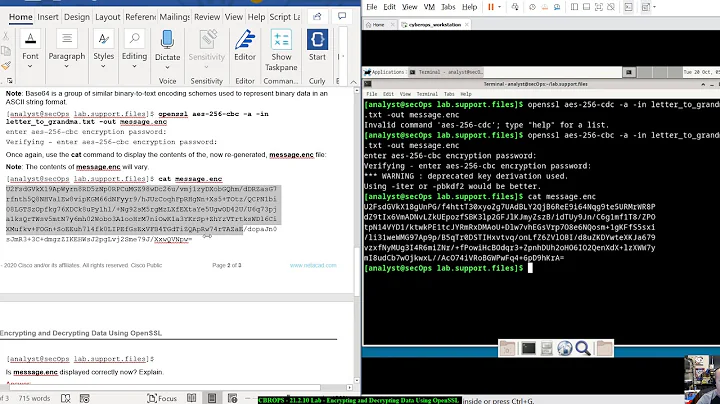
When I encrypt or decrypt a file I get
*** WARNING : deprecated key derivation used. Using -iter or -pbkdf2 would be better.I do not understand what this means, how i should change the my procedures. Could you help me? I encrypt with
openssl des3 <input >output.des3and decrypt withopenssl des3 -d <input.des3 >outputAbout the environment
Ubuntu 18.10
~$ openssl version OpenSSL 1.1.1 11 Sep 2018 -
Ferris almost 5 yearsThen, how to decrypt it when use
openssl enc -aes-256-cbc -md sha512 -pbkdf2 -iter 1000 -salt -in InputFilePath -out OutputFilePath。 -
Eduard Itrich over 4 yearsBy simply adding
-dto the command:openssl enc -aes-256-cbc -md sha512 -pbkdf2 -iter 1000 -salt -d -in InputFilePath -
oskarpearson over 4 yearsI'm pretty sure there are a few issues with this suggestion. As per en.wikipedia.org/wiki/Key_derivation_function you want the slowest variant of key derivation algorithm. In other words don't use sha512 As per en.wikipedia.org/wiki/PBKDF2
in the year 2000 the recommended minimum number of iterations was 1000, but the parameter is intended to be increased over time as CPU speeds increase- so I'd recommend somewhere between 10,000 and 100,000 iterations rather than 1000. -
anthony about 4 years@oskarpearson What hash do you recommend then?
-
 mgutt almost 4 years"This option enables the use of PBKDF2" So,
mgutt almost 4 years"This option enables the use of PBKDF2" So,-pbkdf2is not needed, correct?