How to block broadcast messages (Apple's mDNS traffic)
6,567
UDP cannot have state - try without the state clause.
Also, be aware that if you are checking incoming traffic with tcpdump, this listens OUTSIDE the firewall.
Related videos on Youtube
Author by
orezvani
Updated on September 18, 2022Comments
-
orezvani over 1 year
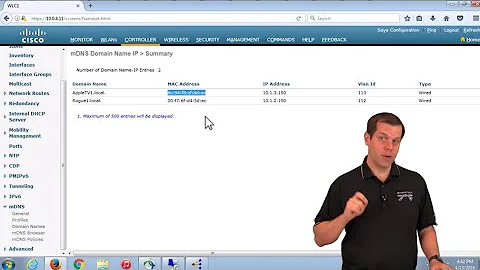
I am in a network and a user is sending broadcast messages on udp port 5353. Regardless of what that is and what their purpose is, I decided to block all the traffic, so I ran:
sudo iptables -A INPUT -i eth0 -p udp -m state --state NEW -m udp --dport 5353 -j DROPBut I am still getting the traffic (in wireshark), but with different source and destinations (neither the source nor the destination matches my IP). Apparently I need a mechanism to drop the broadcasts, is there any way of doing that using
iptablesor ufw?-
 EEAA about 8 yearsWhy do you feel the need to block this traffic?
EEAA about 8 yearsWhy do you feel the need to block this traffic? -
orezvani about 8 yearsWhy shouldn't I block this traffic? There is no need to it, so I want to get rid of it. Secondly, and most importantly, there is security risk, which you can search and find out.
-
fpmurphy about 8 yearsWhy not simply drop all traffic to port 5353? Why the complicated rule?
-
orezvani about 8 years@fpmurphy1 I was trying to do that.
-
 meuh about 8 yearsTry
meuh about 8 yearsTry-I(or--insert) instead of-Ato get the rule placed at the front of the processing. -
orezvani about 8 years@meuh There shouldn't be any difference between
-Aor-I num. As far as I know,-Iplaces the rule in a certain row of the chain table. Since there is no other rule specified in the table, it will automatically have the highest priority.
-
-
orezvani about 8 yearsTried that, but still getting the traffic:
sudo iptables -A INPUT -i eth0 -p udp -m udp --dport 5353 -j DROP -
 meuh about 8 years@emab you are right, wireshark sits between the hardware interface and iptables, so you will still see the packets arriving, before they are dropped by iptables.
meuh about 8 years@emab you are right, wireshark sits between the hardware interface and iptables, so you will still see the packets arriving, before they are dropped by iptables. -
orezvani about 8 yearsThen the problem is probably solved, since I am monitoring the packets in wireshark.
-
 meuh about 8 years@emab You can look at the number of packets matched by a rule with
meuh about 8 years@emab You can look at the number of packets matched by a rule withiptables -L -nvx. -
orezvani about 8 years@meuh Then it is working all good.
-
Jonas Dahlbæk almost 7 yearsAs far as I can tell, UDP 'state' can be handled with
-m conntrack --ctstate, see iptables.info/en/connection-state.html


![How To Hide / Disable Preview From iMessage / Text Messages on Your Mac [macOs Tutorial]](https://i.ytimg.com/vi/i0e4Qow_lDs/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLCymldH4RgxM8UwvnTY9jM6KaThmg)