How to list all the current network connections for a given PID?
Solution 1
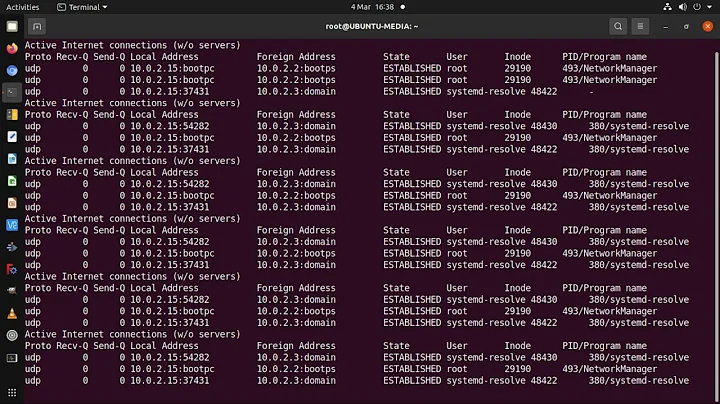
With lsof:
lsof -ai -p "$pid"
If you're not root, you'll only be able to get that for your processes.
Technically, that's only for the internet sockets (connected or not).
If you want all established connections (or associations), internet or not (like for Unix domain sockets), you could try (at least on Linux and with lsof 4.89):
lsof -Ep "$pid" | grep -e '(ESTABLISHED)$' -e '->INO=.* '
For instance, for the process I use to write this answer, that gives:
firefox 6261 chazelas 3u unix 0xffff88026785d000 0t0 741948 type=STREAM ->INO=743009 4244,dbus-daem,58u
firefox 6261 chazelas 4u unix 0xffff88017194c000 0t0 741280 type=STREAM ->INO=742999 3575,Xorg,57u
firefox 6261 chazelas 6u unix 0xffff8802f544d400 0t0 743000 type=STREAM ->INO=741281 4244,dbus-daem,56u
firefox 6261 chazelas 11u unix 0xffff8802f544e800 0t0 743004 type=STREAM ->INO=737278 4167,cinnamon-,21u
firefox 6261 chazelas 14u unix 0xffff8801474b3c00 0t0 737279 type=STREAM ->INO=737280 6261,firefox,15u
firefox 6261 chazelas 15u unix 0xffff8801474b7c00 0t0 737280 type=STREAM ->INO=737279 6261,firefox,14u
firefox 6261 chazelas 34u unix 0xffff8801d0d01800 0t0 741294 type=STREAM ->INO=743006 4244,dbus-daem,57u
firefox 6261 chazelas 45u IPv4 741950 0t0 TCP UNKNOWN:44232->host24-rangeA-akamai-aanp.cdn.thlon.isp.sky.com:http (ESTABLISHED)
firefox 6261 chazelas 53u unix 0xffff880178356800 0t0 741947 type=STREAM ->INO=743008 3575,Xorg,56u
firefox 6261 chazelas 60u IPv4 743011 0t0 TCP UNKNOWN:52760->a95-101-128-57.deploy.akamaitechnologies.com:http (ESTABLISHED)
firefox 6261 chazelas 73u IPv4 742158 0t0 TCP UNKNOWN:54674->lhr35s01-in-f14.1e100.net:http (ESTABLISHED)
firefox 6261 chazelas 87u IPv4 743521 0t0 TCP UNKNOWN:33564->stackoverflow.com:https (ESTABLISHED)
firefox 6261 chazelas 91u IPv4 743522 0t0 TCP UNKNOWN:53940->93.184.220.29:http (ESTABLISHED)
firefox 6261 chazelas 92u IPv4 742153 0t0 TCP UNKNOWN:36836->151.101.65.69:https (ESTABLISHED)
firefox 6261 chazelas 94u IPv4 742154 0t0 TCP UNKNOWN:33716->192.0.73.2:https (ESTABLISHED)
firefox 6261 chazelas 96u IPv4 742157 0t0 TCP UNKNOWN:51166->lhr26s04-in-f234.1e100.net:https (ESTABLISHED)
firefox 6261 chazelas 113u IPv4 744875 0t0 TCP UNKNOWN:43262->lhr35s01-in-f1.1e100.net:https (ESTABLISHED)
Solution 2
With ss.
As an example, I have a pid from proftpd:
[root@ftp ~]# ps fax | grep proftpd
7461 ? Ss 1:46 proftpd: (accepting connections)
Now, grep the output of ss for that process id.
[root@ftp ~]# ss -nap | grep 7461
LISTEN 0 5 *:21 *:* users:(("proftpd",7461,0))
Where:
-a: Display all sockets-n: Do not resolve well known port numbers into names(*:22will become*:ssh)-p: Show process information
Take care. This approach can create some false positives, for example, if you have a pid 22, that can also be the tcp port where you ssh server is listening to.
Solution 3
Probably, this will show the information you want:
netstat -46pan
But it will only show all process numbers if the command is run as root.
So, as root:
netstat -46pan | grep "$pid"
Related videos on Youtube
John
Updated on September 18, 2022Comments
-
John over 1 year
If I have a PID, how can I then find all the connections that are open for that process? I have tried with
netstat | grep $PIDbut this does not seem to work. I need a command that will take that PID and print all the open network connections but I have no idea how. I have seen on other forms about strace but this does not make sense to me.
-
dirkt almost 7 yearsUse
lsof. Seeman lsoffor details.
-
![Config Parameter KP,TI,TD All PID Compact On WINCC/HMI TIA Portal[ Đưa Các Thống Số PID Lên WINCC]](https://i.ytimg.com/vi/aaKvB055i-I/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLBmXiTJR_BfG5DRgvIjSNFba96OzQ)