Is Injection Possible through Dynamic LINQ?
Solution 1
Well, I do not agree that the injection is not possible in Dynamic Linq.
What described in the answer by Ɖiamond ǤeezeƦ is correct but appies to standard Linq as constructed within the given language - C# or VB.Net or by calling extension methods like .Where with lambda functions.
Then, true, it is not possible to inject anything as the .NET Linq to Sql translator is, of course, decently written. Thus, the "SQL injection" is not possible, that's true.
However, what is possible with Dynamic Linq is "Linq injection" attack. In the explanation for safety of linq quoted by OP, it is stated:
LINQ to Entities queries are not composed by using string manipulation or concatenation, and they are not susceptible to traditional SQL injection attacks.
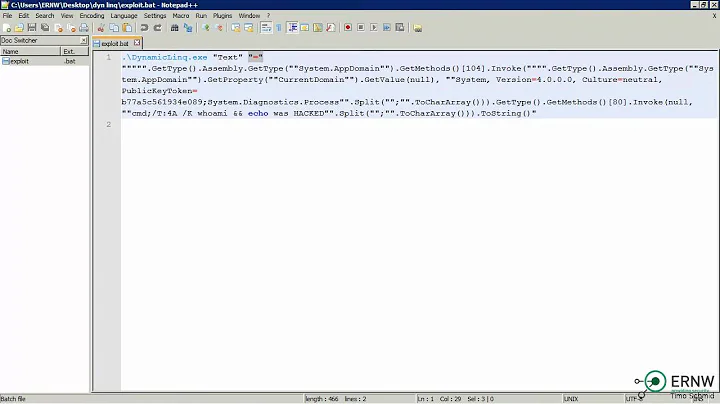
And basically this is a gist. If queries are composed by string manipulation then it is prone to injection attacks. And Dynamic Linq is actually composed from strings, therefore it is potentially prone to attack by injection.
Obviously, the attacker will have to be aware of the fact that you are using DynamicLinq and could attack only preparing the data so it results in valid malicious Dynamic Linq query.
I want to highlight this fact - the final SQL is composed safely, but whether original dynamic Linq is safe depends on you.
The must to make your dynamic linq query safe is to use placeholders for all user input. Never concatenate your string!
Imagine the following query:
dataset.Where("allowed == 1 and code == \"" + user_entered_data + "\"");
If input is not sanitized and not escaped, the attacker could potentially input:
200" or allowed == 0 and code == "200
which will result in:
allowed == 1 and code == "200" or allowed == 0 and code == "200"
In order to avoid this, you should use placeholders:
dataset.Where("allowed == 1 and code == @0", user_entered_data);
DynamicLinq will make the placeholder (in this case: user-entered data) a lambda argument (instead of concatenating it into query) and depend on Linq-To-Entities (or whatever backend is) to safely convert to SQL.
Solution 2
From what I know from examining the System.Data.Linq namespace is that an SQL object tree is built from the LINQ query and as part of this process the SqlParameterizer class is called to replace all inline values with parameters. The values are then assigned to the parameters. So SQL injection attacks should not be possible.
Related videos on Youtube
Seph
Updated on June 07, 2022Comments
-
Seph almost 2 years
Using the Dynamic LINQ library (link), is it vulnerable to injection? and (if so) how can this be protected against?
Some background from Security Considerations (Entity Framework):
LINQ to Entities injection attacks:
Although query composition is possible in LINQ to Entities, it is performed through the object model API. Unlike Entity SQL queries, LINQ to Entities queries are not composed by using string manipulation or concatenation, and they are not susceptible to traditional SQL injection attacks.
Since Dynamic SQL is composed using strings does that mean that it might be susceptible to injection vectors? Or will LINQ to SQL automatically take care of parametrizing your values based on the underlying datatype within the Dynamic LINQ library?
Or is it entirely safe since the dynamic query will be performed in memory rather than against the SQL (thereby negating any benefits from SQL indexes)?
I have been working through understanding the
DynamicLibrary.cscode but I'm sure I could be easily overlooking something.As this question is about the Dynamic LINQ Library itself, this question can be considered to apply to both
linq-to-sqlandlinq-to-entities(despite above reference to Entity Framework). -
Krizz over 12 yearsIt is generally true for linq, but not necessarily for dynamic linq (which OP asks about) where queries are strings, see my answer.
-
Seph over 12 yearsSo injection resulting in leaking data is still possible, but you are still isolated from a 'bobby tables' (dropping / alter data / delete data) incident; that is can you cause a select and where clause to alter the records in a database?
-
Krizz over 12 years@Seph - no, it is not possible to alter the records as linq queries will never translate to update, insert or drop SQL. The only possible attack may be to obtain an access to unauthorized data by modifying "where" filters.
-
Krizz over 12 years@Seph - anyway, if you use placeholders as I noted for all user input, you are fine.
-
Cracker over 11 years@Krizz: When you require something like dataset.Where("allowed == 1 and code == \"" + user_entered_data + "\""); you can use this instead -> dataset.Where("allowed == 1").where("code == \"" + user_entered_data + "\"");. The expression in second where call would be in parenthesis. So even if the user enters something like OR 1=1 this would not give him this records where allowed <> 1. Am I right?
-
 Flater about 3 years@Cracker: You're not wrong about the specific example but it's not always this simple to spot and/or avoid.
Flater about 3 years@Cracker: You're not wrong about the specific example but it's not always this simple to spot and/or avoid.