Java CertificateException in Domino 9 when trying to access HTTPS URL
So for Domino 9, as the new feature OpenSocial was added, a lot of functionality was changed around certificates to make it easier to maintain.
As such there is a new API "com.ibm.domino.napi.ssl.DominoX509TrustManager". What this API does is now check the Domino certificates for the related trusted certificate which is also cross certified against the server certificate.
It checks first in the CACERTS. If it can't find this, then it will check the Domino certificates.
So in order to get the code above to work you need to do the following.
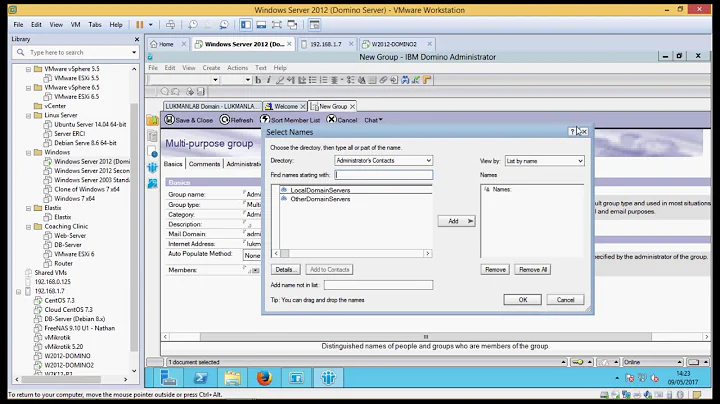
Open the Domino Administrator client and select the ""People and Groups -> Certificates".

In the actions menu select "Import Internet Certificates".

Select the related certificate file to import using the file dialog. It may ask you for the file structure when importing, so select the correct structure if needed. It should appear in the view once completed.

Open the document and from the actions menu select "Create Cross Certificate".

A dialog pops up. You select the certificate and click OK.

Next dialog make sure you have it set correctly for your server. ie. The right server and certifier. Click Cross Certify when done.

This should create a cross certificate in the view:

At this point you need to restart the HTTP process with the following commands.
tell http quit
load http
Related videos on Youtube
Panu Haaramo
Java EE developer and consultant at Sovellustalo Alestalo & Haaramo, a company specializing in Java and Domino development. You can find my contact information in the company web site (in finnish).
Updated on September 18, 2022Comments
-
Panu Haaramo over 1 year
When we upgraded our Domino development server from 8.5.3 to 9 the HTTPS connections from Java code to sites having GoDaddy certificate stopped working. Connections to servers having DigiCert certificate work fine. This happens in both agents and XPages.
Here is an XPage sample code:
<?xml version="1.0" encoding="UTF-8"?> <xp:view xmlns:xp="http://www.ibm.com/xsp/core"> <xp:this.beforePageLoad> <![CDATA[#{javascript:new java.net.URL("https://www.sslshopper.com/").openStream();]]> </xp:this.beforePageLoad> </xp:view>I've also tried with
UrlConnection. Here is the exception:javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: 3659 com.ibm.jsse2.o.a(o.java:15) com.ibm.jsse2.SSLSocketImpl.a(SSLSocketImpl.java:460) com.ibm.jsse2.kb.a(kb.java:294) com.ibm.jsse2.kb.a(kb.java:533) com.ibm.jsse2.lb.a(lb.java:55) com.ibm.jsse2.lb.a(lb.java:581) com.ibm.jsse2.kb.s(kb.java:11) com.ibm.jsse2.kb.a(kb.java:394) com.ibm.jsse2.SSLSocketImpl.a(SSLSocketImpl.java:44) com.ibm.jsse2.SSLSocketImpl.h(SSLSocketImpl.java:496) com.ibm.jsse2.SSLSocketImpl.a(SSLSocketImpl.java:528) com.ibm.jsse2.SSLSocketImpl.startHandshake(SSLSocketImpl.java:505) com.ibm.net.ssl.www2.protocol.https.c.afterConnect(c.java:83) com.ibm.net.ssl.www2.protocol.https.d.connect(d.java:31) sun.net.www.protocol.http.HttpURLConnection.getInputStream(HttpURLConnection.java:1184) com.ibm.net.ssl.www2.protocol.https.b.getInputStream(b.java:40) java.net.URL.openStream(URL.java:1022)...
java.security.cert.CertificateException: 3659 com.ibm.domino.napi.ssl.DominoX509TrustManager.checkServerTrusted(DominoX509TrustManager.java:98) com.ibm.jsse2.lb.a(lb.java:468) com.ibm.jsse2.lb.a(lb.java:581) com.ibm.jsse2.kb.s(kb.java:11) com.ibm.jsse2.kb.a(kb.java:394) com.ibm.jsse2.SSLSocketImpl.a(SSLSocketImpl.java:44) com.ibm.jsse2.SSLSocketImpl.h(SSLSocketImpl.java:496) com.ibm.jsse2.SSLSocketImpl.a(SSLSocketImpl.java:528) com.ibm.jsse2.SSLSocketImpl.startHandshake(SSLSocketImpl.java:505) com.ibm.net.ssl.www2.protocol.https.c.afterConnect(c.java:83) com.ibm.net.ssl.www2.protocol.https.d.connect(d.java:31) sun.net.www.protocol.http.HttpURLConnection.getInputStream(HttpURLConnection.java:1184) com.ibm.net.ssl.www2.protocol.https.b.getInputStream(b.java:40) java.net.URL.openStream(URL.java:1022)I imported the GoDaddy certificates to domino_path\jvm\lib\security\cacerts keystore according to these instructions:
http://drcs.ca/blog/adding-godaddy-intermediate-certificates-to-java-jdk/
But that did not help and I also imported gd-class2-root.crt with no results. I also tried renaming the cacerts file and copying the one from 8.5.3 server but it did not help either. I've been booting HTTP and Domino server after these changes.
Of course I could use Java code that does not care about certificates but I believe that's not a great solution for production. Also we have code in a lot of different places (including JARs) which make HTTPS connection to this URL.
Update 1
This is in error-log-0.xml:
Certificate with subject CN=www.sslshopper.com, OU=Domain Control Validated, O=www.sslshopper.com, issued by SERIALNUMBER=07969287, CN=Go Daddy Secure Certification Authority, OU=http://certificates.godaddy.com/repository, O="GoDaddy.com, Inc.", L=Scottsdale, ST=Arizona, C=US, is not trusted. Validation failed with error 3659.
I think this message is quite clear. I also noticed that
System.getProperty("javax.net.ssl.trustStore")returns null but that happens also in 8.5.3 server where this works. I tried setting the trustStore withsetPropertybut the error is still the same.Update 2
It works with Simon's code that uses
createSocket. But all our code usejava.net.URL,UrlConnection,HttpsUrlConnectionor Apache HTTP Client. Some of these are provided by 3rd party as a JAR. We cannot change all those to usecreateSocket.Any ideas? Thanks.
-
Simon O'Doherty almost 11 yearsHave you tried enabling debug mode to get more details as to the nature of the failure? eg. System.setProperty("javax.net.debug", "ssl");
-
Panu Haaramo almost 11 yearsThanks, that's a good idea. I added that but don't see any additional logging (maybe I don't know where to look). However I found a bit more info when looking at the logs, will update the question. It would be interesting to know if this happens to you also with the above sample code.
-
Simon O'Doherty almost 11 yearsYou need to set your trust store. Here is some sample code: www-10.lotus.com/ldd/ddwiki.nsf/dx/…
-
Simon O'Doherty almost 11 yearsyea, I'd say try that sample code. If that works you can rule out an issue with your certificates.
-
Panu Haaramo almost 11 yearsYes it works. But I don't know what to try next. I think there will be a ticket coming to you :-)
-
Simon O'Doherty almost 11 yearsThat would be my next suggestion if no joy here. :)
-
-
Panu Haaramo almost 11 yearsThanks Simon! Btw. I could not get it to work with CACERTS so for me it looks like it does not check the CACERTS file.
-
Simon O'Doherty almost 11 yearsIt appears it needs a cross certificate created by the Server certificate. So that would need to be in the CACERTS as well. Steps above save you having to import that as well. The earlier steps we were just putting in the GoDaddy certificates alone. If it is still failing in CACERTS with the cross certificate let me know and I'll create an SPR. Cheers! :)
-
Panu Haaramo almost 11 yearsOK thanks! I'm happy with the Domino Directory solution and no need to go back to CACERTS.
![SSL Certificate Error Fix [Tutorial]](https://i.ytimg.com/vi/Xp5G8x3SNhE/hqdefault.jpg?sqp=-oaymwEcCOADEI4CSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLDbPsM9guRh7myRvKhCABz8ha1lOg)