Permissions on private key in .ssh folder?
Solution 1
Typically you want the permissions to be:
-
.sshdirectory:700 (drwx------) - public key (
.pubfile):644 (-rw-r--r--) - private key (
id_rsa):600 (-rw-------) - lastly your home directory should not be writeable by the group or others (at most
755 (drwxr-xr-x)).
I am assuming that you mean that you have to enter your system/user password each time, and that previously you did not have to. cdhowie's response is assuming you set a password/passphrase when generating your keys, and if you did then as he says you will have to enter your password every time unless you use an ssh agent.
Solution 2
I was struggling with this forever and finally figured out what is needed. Replace $USER everywhere with the SSH username you want to log into on the server. If you're trying to login as root you would need to use /root/.ssh etc., instead of /home/root/.ssh which is how it is for non-root users.
- Home directory on the server should not be writable by others:
chmod go-w /home/$USER - SSH folder on the server needs 700 permissions:
chmod 700 /home/$USER/.ssh - Authorized_keys file needs 644 permissions:
chmod 644 /home/$USER/.ssh/authorized_keys - Make sure that
userowns the files/folders and notroot:chown user:user authorized_keysandchown user:user /home/$USER/.ssh - Put the generated public key (from
ssh-keygen) in the user'sauthorized_keysfile on the server - Make sure that user's home directory is set to what you expect it to be and that it contains the correct
.sshfolder that you've been modifying. If not, useusermod -d /home/$USER $USERto fix the issue - Finally, restart ssh:
service ssh restart - Then make sure client has the public key and private key files in the local user's
.sshfolder and login:ssh [email protected]
Solution 3
Am posting this as a separate answer since I wanted to see man page recommendations translated into permissions.
Summary based on the man page quotes (linked at the end):
| Directory or File | Man Page | Recommended Permissions |
Mandatory Permissions |
|---|---|---|---|
~/.ssh/ |
There is no general requirement to keep the entire contents of this directory secret, but the recommended permissions are read/write/execute for the user, and not accessible by others. | 700 | |
~/.ssh/authorized_keys |
This file is not highly sensitive, but the recommended permissions are read/write for the user, and not accessible by others | 600 | |
~/.ssh/config |
Because of the potential for abuse, this file must have strict permissions: read/write for the user, and not accessible by others. It may be group-writable, provided that the group in question contains only the user. | 600 | |
~/.ssh/identity~/.ssh/id_dsa~/.ssh/id_rsa
|
These files contain sensitive data and should be readable by the user but not accessible by others (read/write/execute) | 600 | |
~/.ssh/identity.pub~/.ssh/id_dsa.pub~/.ssh/id_rsa.pub
|
Contains the public key for authentication. These files are not sensitive and can (but need not) be readable by anyone. | 644 |
All the man page quotes are from http://linuxcommand.org/lc3_man_pages/ssh1.html
Solution 4
Also ensure that your home directory is not writeable by other users.
chmod g-w,o-w ~
Solution 5
Permissions shouldn't have anything to do with this. Your private key is encrypted with the password, so you need to enter it for the private key to be decrypted and usable.
You might consider running an ssh agent, which can cache decrypted keys and will supply them to applications that need them.
Related videos on Youtube
Giacomo1968
Updated on September 17, 2022Comments
-
 Giacomo1968 over 1 year
Giacomo1968 over 1 yearI changed my permissions in my
.sshfolder and now when I use a piece of software that uses my private key, I have to type my password each time. What should my permissions be on myid_rsafile to not have to type a password each time I use an app that uses it?Currently my permissions are set to:
-rw-------@ 1 Jody staff 114 Nov 4 23:29 config -rw------- 1 Jody staff 1743 Oct 21 2009 id_rsa -rw-------@ 1 Jody staff 397 Oct 21 2009 id_rsa.pub -rw-------@ 1 Jody staff 3855 Sep 13 22:35 known_hosts-
Akhil about 4 years
#!/bin/bash find .ssh/ -type f -exec chmod 600 {} \;; find .ssh/ -type d -exec chmod 700 {} \;; find .ssh/ -type f -name "*.pub" -exec chmod 644 {} \; -
ThaJay almost 3 yearsThank you @AkhilJalagam, your code just saved me some thinking. I love stuff like that. I know how to do it but why should I if it's already here :D
-
-
user215505 over 13 yearsThanks for the additional info about the ssh agent. Looks like there is one built into Leopard so I think I'll do that. Having a bit of trouble with it but I'll ask another question.
-
 Job AJ over 9 yearsI found elsewhere that if using the authorized_keys file, that it should be chmod'd to 640, ie -rw-r----- .
Job AJ over 9 yearsI found elsewhere that if using the authorized_keys file, that it should be chmod'd to 640, ie -rw-r----- . -
Sonique over 9 yearsWhere I can find this info in man pages?
-
 JREAM about 9 yearsI have come back to this post about 30 times now. I cant believe I cant remember it.
JREAM about 9 yearsI have come back to this post about 30 times now. I cant believe I cant remember it. -
Alex W almost 9 yearsDo not underestimate permissions. They definitely still come into play.
-
cdhowie almost 9 years@AlexW They do come into play with other aspects of ssh, but not the one asked about in the question.
-
Alex W almost 9 yearsFYI, this command assumes you are logged in as the user and not root
-
 Markus Kuhn over 8 yearsYou can also safely leave the
Markus Kuhn over 8 yearsYou can also safely leave the.sshdirectory permissions at755 (drwxr-xr-x), as well as theid_*.pubandauthorized_keyspermissions at644 (-rw-r--r--). Otherwise other users cannot lookup your public keys, but being able to do so is often convenient if they need to know your public keys to grant you access to some service. -
 Markus Kuhn over 8 yearsThe only important things are that nothing in .ssh is writeable to anyone else and none of the secret keys are readable to anyone else.
Markus Kuhn over 8 yearsThe only important things are that nothing in .ssh is writeable to anyone else and none of the secret keys are readable to anyone else. -
 Michael Millar over 8 yearsRegarding your first paragraph, I am able to ssh with public/private keys with a user on my local linux box (e.g.
Michael Millar over 8 yearsRegarding your first paragraph, I am able to ssh with public/private keys with a user on my local linux box (e.g.abc), different from the user on the remote server (e.g.[email protected]). I just had to make sure the local user owned the local .ssh files (e.g.abc:abc, notroot:abc)` -
 nerdoc over 8 yearsIf you have no password on private keys (whink of automated remote called scripts), it won't help you. Permissions are necessary here.
nerdoc over 8 yearsIf you have no password on private keys (whink of automated remote called scripts), it won't help you. Permissions are necessary here. -
augurar about 8 years
-
 Nav about 8 yearsThanks for putting all the steps and commands for newbies, Alex. Yours is one of the most helpful answers here.
Nav about 8 yearsThanks for putting all the steps and commands for newbies, Alex. Yours is one of the most helpful answers here. -
 Alan Robinson almost 8 years@augurar My guess: a world-readable
Alan Robinson almost 8 years@augurar My guess: a world-readableauthorized_keysfile would expose the (public) keys that an attacker could use to gain full access to your account. They'd still need to find one of the private keys, of course. -
 Alan Robinson almost 8 yearsTo let others verify your signatures and encrypt files for you, make the public key files (
Alan Robinson almost 8 yearsTo let others verify your signatures and encrypt files for you, make the public key files (*.pub) world-readable and the.sshfolder world-readable and -executable. Without the latter, other users won't be able to view the public key files. -
Cerin over 7 yearsWhy 700? Why would you need anything under
~/.sshto be executable? -
xtian over 7 yearsWhy, after generated, would private key be writeable (600)? Generate the keys, then lock down the folder, no?
-
Florian Brucker over 7 yearsThe correct permissions for
~/.ssh/configare600. -
Thomas over 7 years@Cerin execute permission on a directory grants the ability to list immediate child files/dirs of that directory, files inside the folder don't "inherit" the execute bit of their parent folder.
-
Le Quoc Viet almost 7 years+1. "Authorized_keys file needs 644 permissions" <= that was crucial!
-
Adam Glauser over 6 yearsAt least some versions of OpenSSH require home directory permissions such that only the user can write the home directory. Otherwise,
~/.sshcould be replaced by a link, and an arbitraryauthorized_keysfile substituted. -
user3125367 over 6 yearsIf you're giving .ssh directory 700 mode, then there is no point in giving r-- to group and others, because only you can "go through" .ssh then (assuming no hard links exists for these files). The same for accepted answer. Default 755 is enough.
-
 Craig Hicks over 5 years"I have to type my password each time. What should my permissions be on my id_rsa file to not have to type a password each time I use an app that uses it?"
Craig Hicks over 5 years"I have to type my password each time. What should my permissions be on my id_rsa file to not have to type a password each time I use an app that uses it?" -
A T over 5 years400 for the pem files are sufficient in my experience.
-
Akito over 4 yearsI get
Permissions 0644 for '/home/user/.ssh/id_rsa.pub' are too open.on Debian Buster. -
Lloyd Dewolf over 4 yearsThis answer cannot be correct as the directory is more restrictive than the public key.
-
Weltraumschaf about 4 yearsAs @Akito mentioned it makes no sense to give id_rsa.pub 0644 if the parent dir has 0700 nobody else than the owner can access the file.
-
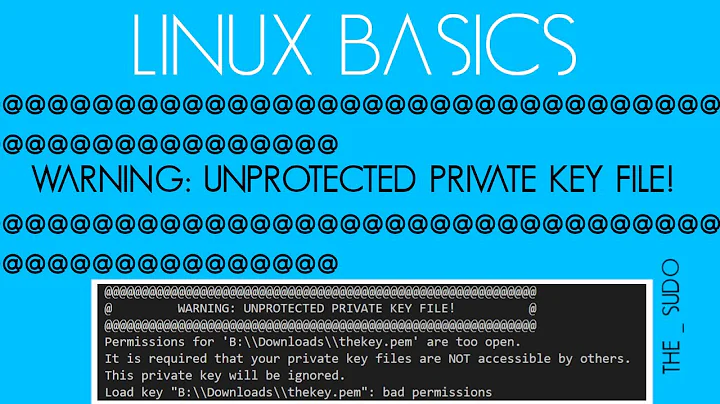
 juliangonzalez about 4 years
juliangonzalez about 4 years664will raise a WARNING: UNPROTECTED PRIVATE KEY FILE! with aPermissions 0644 for 'varys-new.pem' are too open.Use600instead. -
James Bond over 3 yearsJREAM, this is because you don't try to write this numbers yourself) You are afraid to make a mistake. But when you will try to call to mind some numbers without prompts, quite possibly you will make a mistake, but an the next you will remember information strongly. You SHOULD make a mistake. This is a way to remember. This is how a human brain works)
-
xtian about 3 yearsLet's not forget
known_hosts> "~/.ssh/known_hosts Contains a list of host keys for all hosts the user has logged into that are not already in the systemwide list of known host keys. [...] This file should be writable only by root/the owner and can, but need not be, world-readable." (linux.die.net/man/8/sshd) -
Dmitry Gusarov over 2 yearsThank you! Saved my life... Stupid me, copied authorized_keys file from user to root. Your post helped me figure out that I need chown root:root authorized_keys. That was the solution for me
-
Alan about 2 yearsWhat about 440 for the private key(id_rsa)? There is a group of 'n' users - which is same person but different accounts so x4x should be fine? Also, the private key doesn't have to be modified so why setting 6xx?