Postfix and OpenSSL: "Unable to get local issuer certificate"
It sounds like you've installed it correctly, but your verification step is incorrect. OpenSSL doesn't know where to look to find root certificates unless you explicitly tell it.
Try openssl s_client -connect mail.example.com:25 -starttls smtp -CApath /etc/ssl/certs instead. That should work.
Related videos on Youtube
Jaap Joris Vens
Roads? Where we're going we don't need roads.
Updated on September 18, 2022Comments
-
 Jaap Joris Vens over 1 year
Jaap Joris Vens over 1 yearI bought a certicifate for my mail server and configured it in Postfix like so:
smtpd_tls_security_level=may smtpd_tls_CAfile = /etc/ssl/certs/ca-certificates.crt smtpd_tls_cert_file = /somepath/chain.crt smtpd_tls_key_file = /somepath/myserver.keyI created
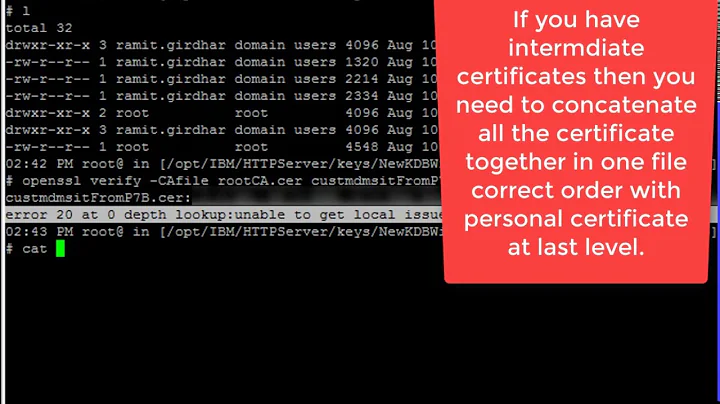
chain.crtper Postfix instructions by concatenating my certificate and the two intermediate CA certs. (To be precise, my own cert first, thenCOMODORSADomainValidationSecureServerCA.crtand thenCOMODORSAAddTrustCA.crt) According to the logs, most connections to my mail server are now encrypted so everything seems to work.However, when I connect to the server using
openssl s_client -connect mail.example.com:25 -starttls smtpI get the following output, which seems to indicate that something is wrong:CONNECTED(00000003) depth=2 C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO RSA Certification Authority verify error:num=20:unable to get local issuer certificate verify return:0 --- Certificate chain 0 s:/OU=Domain Control Validated/OU=PositiveSSL/CN=mail.example.com i:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO RSA Domain Validation Secure Server CA 1 s:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO RSA Domain Validation Secure Server CA i:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO RSA Certification Authority 2 s:/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO RSA Certification Authority i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root --- Server certificate -----BEGIN CERTIFICATE----- 8< -----END CERTIFICATE----- subject=/OU=Domain Control Validated/OU=PositiveSSL/CN=mail.example.com issuer=/C=GB/ST=Greater Manchester/L=Salford/O=COMODO CA Limited/CN=COMODO RSA Domain Validation Secure Server CA --- No client certificate CA names sent --- SSL handshake has read 5217 bytes and written 489 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 2048 bit Secure Renegotiation IS supported Compression: zlib compression Expansion: zlib compression SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: B2736D2B1639153CB8379480ACDBC1F0B1DCC51DE7CC27DA59061740F0186EA1 Session-ID-ctx: Master-Key: 9EE658D6B1835F94D140E7BBF05A5A8960566584A8BC6FF40DD5D038C70127A63BAB580A41BC55DEEA3C031FCC7FA550 Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 3600 (seconds) TLS session ticket: 0000 - 09 8a 6d 68 70 0c 64 c0-23 2e fc f2 d4 21 ca bd ..mhp.d.#....!.. 0010 - 0a 15 4f 36 06 a8 ea f9-e2 84 de 18 cf 31 af 77 ..O6.........1.w 0020 - 2a a1 98 d5 f8 df 54 48-82 68 cb c3 91 9b 38 60 *.....TH.h....8` 0030 - dc 2e 18 f4 b9 bd 43 3e-26 cf 80 49 48 bb a4 98 ......C>&..IH... 0040 - bc 94 7d 1e 5f 51 7e 52-d6 ad 7f 8b e5 36 ee 55 ..}._Q~R.....6.U 0050 - 7a bb 15 d3 c2 7f b2 f4-5a 85 a5 80 1b 9e 67 98 z.......Z.....g. 0060 - 3a 2f 5c d1 34 d5 bb 11-c7 8f fc 10 cb c3 b4 cb :/\.4........... 0070 - 49 61 41 ac aa b1 cb eb-6f 7a 22 e5 79 a2 c6 1f IaA.....oz".y... 0080 - 98 25 39 f0 f0 79 b4 ee-95 72 93 04 0f a2 f3 69 .%9..y...r.....i 0090 - 8f 8a 86 c6 8f a5 38 ed-25 ba fc c8 db 6b 9a 8e ......8.%....k.. 00a0 - 13 1e e5 c6 28 98 e4 17-ce 69 d5 c2 aa 1a de 4b ....(....i.....K Compression: 1 (zlib compression) Start Time: 1400131328 Timeout : 300 (sec) Verify return code: 20 (unable to get local issuer certificate) ---Also, when running
openssl verify chain.crtI get the same error message:chain.crt: OU = Domain Control Validated, OU = PositiveSSL, CN = mail.example.com error 20 at 0 depth lookup:unable to get local issuer certificateI have tried adding the
AddTrustExternalCARoot.crtto the end ofchain.crtwhich makes the error message change toverify error:num=19:self signed certificate in certificate chain. Besides, the machine I'm connecting from already has this certificate installed so there should be no need for it.So my question is: Is there something wrong with my mailserver or am I just using the
opensslcommand incorrectly? And should I include the root certificate in the chain or not?