Prevent XSS attacks site-wide
Solution 1
I hate to break it out to you, but -
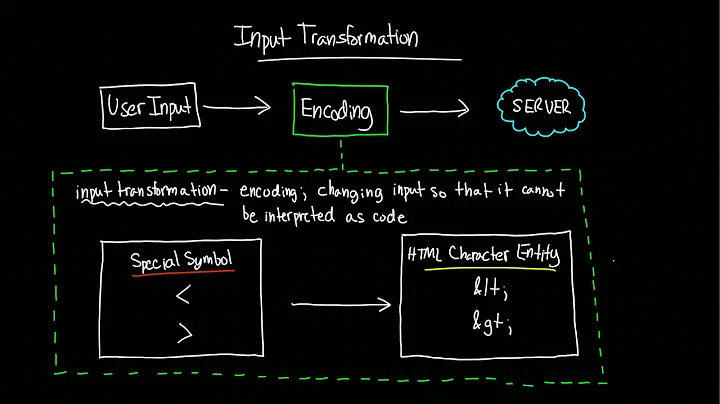
- XSS is an Output problem, not an Input problem. Filtering/Validating input is an additional layer of defence, but it can never protect you completely from XSS. Take a look at XSS cheatsheet by RSnake - there's just too many ways to escape a filter.
- There is no easy way to fix a legacy application. You have to properly encode anything that you put in your html or javascript files, and that does mean revisiting every piece of code that generates html.
See OWASP's XSS prevention cheat sheet for information on how to prevent XSS.
Some comments below suggest that input validation is a better strategy rather than encoding/escaping at the time of output. I'll just quote from OWASP's XSS prevention cheat sheet -
Traditionally, input validation has been the preferred approach for handling untrusted data. However, input validation is not a great solution for injection attacks. First, input validation is typically done when the data is received, before the destination is known. That means that we don't know which characters might be significant in the target interpreter. Second, and possibly even more importantly, applications must allow potentially harmful characters in. For example, should poor Mr. O'Malley be prevented from registering in the database simply because SQL considers ' a special character?
To elaborate - when the user enters a string like O'Malley, you don't know whether you need that string in javascript, or in html or in some other language. If its in javascript, you have to render it as O\x27Malley, and if its in HTML, it should look like O'Malley. Which is why it is recommended that in your database the string should be stored exactly the way the user entered, and then you escape it appropriately according to the final destination of the string.
Solution 2
One thing you should look at is implementing an application firewall like Portcullis: http://www.codfusion.com/blog/page.cfm/projects/portcullis which includes a much stronger system then the built in scriptProtect which is easily defeated.
These are a good starting point for preventing many attacks but for XSS you are going to end up going in by hand and verifying that you are using things like HTMLEditFormat() on any outputs that can be touched by the client side or client data to prevent outputting valid html/js code.
Related videos on Youtube
Steven
Updated on May 02, 2022Comments
-
Steven almost 2 years
I'm new to ColdFusion, so I'm not sure if there's an easy way to do this. I've been assigned to fix XSS vulnerabilities site-wide on this CF site. Unfortunately, there are tons of pages that are taking user input, and it would be near impossible to go in and modify them all.
Is there a way (in CF or JS) to easily prevent XSS attacks across the entire site?
-
BalusC over 13 yearsNote that you'd like to prevent it using the server side programming language/framework, not using the client side one (like JS). Client side languages are namely disableable, hackable and spoofable by the client.
-
-
Sripathi Krishnan over 13 years@Klinky - See my updated response. Input filtering helps, but isn't a sure-shot solution to XSS.
-
Klinky over 13 yearsGood points, your update and actually reading the OWASP in more detail makes it a bit more clear why escaping on output would be advantageous and more flexible. I would still say validation is a requirement on things that can be validated effectively, for example you don't want to accept user input of a string when your db or javascript is going to be expecting an integer. That would not be an XSS issue though.
-
Sripathi Krishnan over 13 years@Klinky - Agree, input validation is very important and should always be a requirement. I am only against considering that as the solution to XSS and other related injection problems.
-
Om Shankar about 11 years@Klinky, "you don't want to accept user input of a string" - From an HTML Page, user can only input strings - never mind, just digging posts :)
-
 Nihal Rp over 7 years@yeouuu . It's down.
Nihal Rp over 7 years@yeouuu . It's down. -
 Mayank about 6 years@SripathiKrishnan what if we replace or prevent "<" and ">" onBlur or key up or form submit ,somthing like html.replace(/</g, "<").replace(/>/g, ">");
Mayank about 6 years@SripathiKrishnan what if we replace or prevent "<" and ">" onBlur or key up or form submit ,somthing like html.replace(/</g, "<").replace(/>/g, ">");