Proper way to set up rsnapshot over ssh
You will be running as root on server A, which runs rsnapshot, and ssh-ing to your dedicated user backupmaker on B. Normally, you will want this user to be able to sudo rsync, so that you can read all the files to send back to A.
Assume, for example, you have a user on A who can sudo, and another user on B who can sudo. On B create user backupmaker and give it a password. On B create a sudoers entry for it to run rsync without a password, eg:
sudo tee /etc/sudoers.d/backupmaker <<<'backupmaker ALL = (root) NOPASSWD: /usr/bin/rsync'
(Beware when editing sudoers files. Always ensure you have a root login somewhere for recovery). On A, from your user account copy root's ssh keys to this new user:
sudo ssh-copy-id backupmaker@B
(If you don't have root keys setup yet, use sudo ssh-keygen -q -N '' on A to create them).
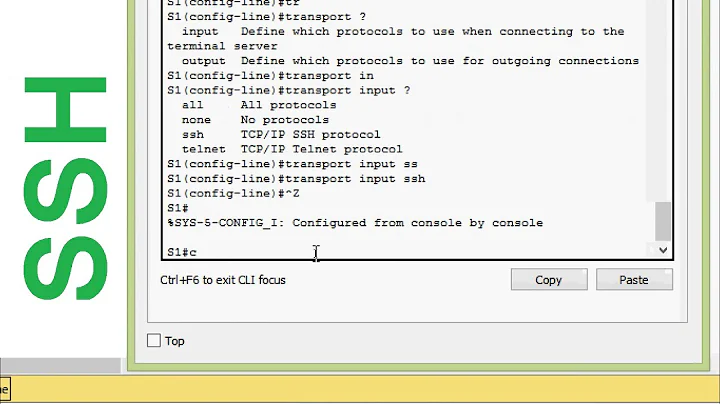
On A, test root can ssh to B without password and sudo to rsync:
sudo ssh backupmaker@B sudo rsync --version
On A configure /etc/rsnapshot.conf, removing existing backup lines and adding at the end, for example
verbose 3
cmd_ssh /usr/bin/ssh
rsync_long_args --rsync-path="sudo rsync" --delete --numeric-ids --relative --delete-excluded
backup backupmaker@B:/home/ mybackupofB/
Beware, the 2 columns are separated by tabs, not spaces. The last line is an example saying we will ssh to backupmaker@B and copy /home back to A's /.snapshots/hourly.0/mybackupofB/. Note the rsync_long_args has an option --rsync-path="sudo rsync" which means the command run on B will not be rsync but sudo rsync. To start with, use a small directory to backup rather than all of /home.
You may also want to change the default placement of backups on A from /.snapshots.
You can now try a first snapshot on A.
sudo rsnapshot -vvv hourly
This will run on A the commands:
/usr/bin/ssh -l backupmaker B sudo rsync --server --sender -logDtprRe.iLsfx --numeric-ids . /home
/usr/bin/rsync -a --rsync-path='sudo rsync' --delete --numeric-ids --relative --delete-excluded --rsh=/usr/bin/ssh backupmaker@B:/home /.snapshots/hourly.0/backupmaker/
and on B:
sh -c sudo rsync --server --sender -logDtprRe.iLsfx --numeric-ids . /home
Look in /var/log/rsnapshot for logs.
Related videos on Youtube
Forkbeard
Updated on September 18, 2022Comments
-
 Forkbeard almost 2 years
Forkbeard almost 2 yearsI have two Debian 8 servers:
- Server A: at home, lots of storage
- Server B: vps at commercial host, running web and mail services
Both are pet projects, not business stuff.
Server B runs rsnapshot which works fine. Server A and B can SSH to each other passwordlesly with certificates, that also works fine. They do not allow root to SSH in directly but they have regular user accounts that can sudo su to become root. For non-automated SSH sessions I use password protected certs.
The last couple of days I have been trying to set up rsnapshot on server B to create backups from server B to server A, or on server A to pull backups from server B to server A, which seems the proper way according to rsnapshot documentation.
My problem is that a lot a documentation mentions servers relatively, for example they say 'do x on your server' or 'copy y to ~/somepath'. Seldom did I find documentation that explicitly lays out which server has which functions and which user's home directory it is that you need to copy y to.
So:
- The production data that needs to be backed up is on server B.
- The backups need to be saved to server A.
- Server A is going to run rsnapshot.
Questions:
In the rsnapshot config, which user account do I need to say is going to log in via SSH on server B? Either root (which gets either complicated or unsafe) or a dedicated regular user account, for example a user called 'backupmaker' (Debian has a system user called 'backup' which is eligable but I don't want to mess with).
I have read both and I understand the Linux mantra that more ways can be fine but I am really looking for some practicle advice from someone who has this set up in a production environment, preferably with relevant lines from /etc/rsnapshot.conf and /home//.ssh/authorized_keys (do you really use from="a.b.c.d",command="/home/remoteuser/cron/validate-rsync", and is that 'validate-rsync' script mandatory or can it be any command, e.g. /home/serverAuser/myrsnapscript.sh?).
Do you use the root account for creating backups on server B, a regular user account, a custom dedicated account or the built-in 'backup' account?
I am not looking for sshfs or other alternatives; I want to do this right, maybe expand it to a hub backup system later on.
Any insights and advice are welcome!
-
 Forkbeard over 7 yearsExactly the type of answer I was looking for. Thanks!
Forkbeard over 7 yearsExactly the type of answer I was looking for. Thanks! -
DrSAR over 4 yearssmall niggle: use
visudoto edit your sudoers file (just as the comment at the top of said file admonishes you to do)