"Remove the following redirect chain if possible" on Nginx
Just change $scheme to https, I can't tell why that's there in the first place since you're unlikely to get anything other than http over port 80 unless your users are doing something weird.
EDIT: Add missing https->https redirect.
Didn't notice you don't actually have an explicit default_server.
Go with something along the lines of:
server {
listen 80;
server_name example.com www.example.com;
return 301 https://www.example.com$request_uri;
}
server {
listen 443;
server_name example.com;
return 301 https://www.example.com$request_uri;
}
Ashish's answer might work but I'd stay away from if as much as possible (read If is Evil).
Related videos on Youtube
user3108268
Updated on September 18, 2022Comments
-
user3108268 over 1 year
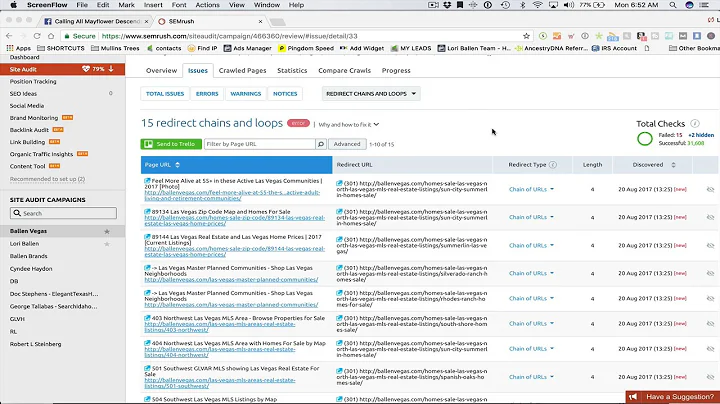
I ran Pingdom test on my 1 plain html file site and I get F rating for this:
Remove the following redirect chain if possible:
http://example.com/ http://www.example.com/ https://www.example.com/And the only redirect in my .conf I have is:
server { listen 80; server_name example.com; return 301 $scheme://www.example.com$request_uri; }Next block is SSL and and the rest.
server { listen 443 ssl http2; etc... }There are no other configs. All I need is to redirect non-www to www and always https only and pass the test.
Updated: Full .conf
server { listen 80; server_name example.com; return 301 https://www.example.com$request_uri; } server { listen 443 ssl http2; ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers 'EECDH+CHACHA20:EECDH+AES128:RSA+AES128:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5'; ssl_dhparam /etc/nginx/ssl/dhparams.pem; ssl_session_timeout 1d; ssl_session_cache shared:SSL:50m; ssl_stapling on; ssl_stapling_verify on; add_header Strict-Transport-Security max-age=15768000; root /var/www/example.com/htdocs; server_name example.com www.example.com; location / { autoindex on; try_files $uri $uri/ =404; } location ~* /img/.*\.gif$ { expires 30d; add_header Pragma public; add_header Cache-Control "public"; } }-
 Admin about 7 yearsUpdated with full conf
Admin about 7 yearsUpdated with full conf
-
-
 Jenny D about 7 yearsI think you're missing a negation there. I'd say it's unlikely not to get http over port 80.
Jenny D about 7 yearsI think you're missing a negation there. I'd say it's unlikely not to get http over port 80. -
user3108268 about 7 yearswhat it has to do with godaddy, i'm on vultr with namescheap.
-
user3108268 about 7 yearsHi, I did and it only removed
http://www.example.com/from the list and I still get an F. -
user3108268 about 7 yearsalso does not redirect from
https://example.comtohttps://www.example.com -
user3108268 about 7 yearsalso does not redirect from
https://example.comtohttps://www.example.com -
 Ashish Gupta about 7 yearsIf user want to enforce all non www to www only then best is to use godaddy redirection. From you godaddy dns manager can permanently redirect to https and www no need to add in nginx.
Ashish Gupta about 7 yearsIf user want to enforce all non www to www only then best is to use godaddy redirection. From you godaddy dns manager can permanently redirect to https and www no need to add in nginx. -
 Ashish Gupta about 7 yearsIn my new code block location match will be present in both 80 and 443
Ashish Gupta about 7 yearsIn my new code block location match will be present in both 80 and 443 -
Tero Kilkanen about 7 yearsOne does not want to use
ifin cases like this when it can be easily avoided.

![Redirect Chains [How to Fix]](https://i.ytimg.com/vi/PmLw_WdvrZE/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLB5AqH4DOQI6T_BffvPQU9A6hP5zg)