Site to Site VPN error 'received hash payload does not match computed value'
There was network configuration issue on the other side. This is resolved.
I am the OP
Related videos on Youtube
Tapo
Updated on September 18, 2022Comments
-
Tapo over 1 year
We need to access a couple of Linux machines located at our client's end. Our Linux machine, from which we need to access client's machine is located on cloud.
The connection to be established is site-to-site VPN.
On restarting the ipsec service thru' command
sudo service ipsec restartthe connection ends with error received Hash Payload does not match computed valueThough, we have re-verified that
ipsec.secretshas proper key, as it was shared by the client. Also, on running commandsudo ipsec auto --up vpnthe cli hangs up.Being a toddler in networking, I am sharing most of the output which I think, maybe relevant to the error. Please let me know if more information is required.
Following information is shared below:
- Output for ipsec service restart
- Complete log in
/var/log/securewhen ipsec service is started - Configuration in
ipsec.conf - Configuration in
ipsec.secrets - Output of
ipsec.verify - Output of
ifconfig - Client's and ours documented VPN information shared
Output for ipsec service restart
[root@gbox-1 ~]# service ipsec restart ipsec_setup: Stopping Openswan IPsec... ipsec_setup: Starting Openswan IPsec 2.6.32... ipsec_setup: No KLIPS support found while requested, desperately falling back to netkey ipsec_setup: NETKEY support found. Use protostack=netkey in /etc/ipsec.conf to avoid attempts to use KLIPS. Attempting to continue with NETKEY ipsec_setup: /usr/libexec/ipsec/addconn Non-fips mode set in /proc/sys/crypto/fips_enabledComplete log in
/var/log/securewhen ipsec service is started[root@gbox-1 log]# tail -f secure Jul 31 23:43:24 gbox-1 sshd[3005]: pam_unix(sshd:session): session opened for user root by (uid=0) Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down Jul 31 23:43:38 gbox-1 pluto[32279]: forgetting secrets Jul 31 23:43:38 gbox-1 pluto[32279]: "vpn": deleting connection Jul 31 23:43:38 gbox-1 pluto[32279]: "vpn" #1: deleting state (STATE_AGGR_I1) Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface lo/lo ::1:500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface eth0/eth0 2001:4800:780e:510:acf:6c9b:ffd8:94cd:500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface lo/lo 127.0.0.1:4500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface lo/lo 127.0.0.1:500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface eth0/eth0 50.55.153.121:4500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface eth0/eth0 50.55.153.121:500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface eth1/eth1 10.180.3.132:4500 Jul 31 23:43:38 gbox-1 pluto[32279]: shutting down interface eth1/eth1 10.180.3.132:500 Jul 31 23:43:40 gbox-1 ipsec__plutorun: Starting Pluto subsystem... Jul 31 23:43:40 gbox-1 pluto[3352]: nss directory plutomain: /etc/ipsec.d Jul 31 23:43:40 gbox-1 pluto[3352]: NSS Initialized Jul 31 23:43:40 gbox-1 pluto[3352]: Non-fips mode set in /proc/sys/crypto/fips_enabled Jul 31 23:43:40 gbox-1 pluto[3352]: FIPS: not a FIPS product Jul 31 23:43:40 gbox-1 pluto[3352]: FIPS HMAC integrity verification test passed Jul 31 23:43:40 gbox-1 pluto[3352]: Starting Pluto (Openswan Version 2.6.32; Vendor ID OEhyLdACecfa) pid:3352 Jul 31 23:43:40 gbox-1 pluto[3352]: Non-fips mode set in /proc/sys/crypto/fips_enabled Jul 31 23:43:40 gbox-1 pluto[3352]: LEAK_DETECTIVE support [disabled] Jul 31 23:43:40 gbox-1 pluto[3352]: OCF support for IKE [disabled] Jul 31 23:43:40 gbox-1 pluto[3352]: SAref support [disabled]: Protocol not available Jul 31 23:43:40 gbox-1 pluto[3352]: SAbind support [disabled]: Protocol not available Jul 31 23:43:40 gbox-1 pluto[3352]: NSS support [enabled] Jul 31 23:43:40 gbox-1 pluto[3352]: HAVE_STATSD notification support not compiled in Jul 31 23:43:40 gbox-1 pluto[3352]: Setting NAT-Traversal port-4500 floating to on Jul 31 23:43:40 gbox-1 pluto[3352]: port floating activation criteria nat_t=1/port_float=1 Jul 31 23:43:40 gbox-1 pluto[3352]: NAT-Traversal support [enabled] Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating OAKLEY_TWOFISH_CBC_SSH: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating OAKLEY_TWOFISH_CBC: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating OAKLEY_SERPENT_CBC: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating OAKLEY_AES_CBC: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating OAKLEY_BLOWFISH_CBC: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_hash(): Activating OAKLEY_SHA2_512: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_hash(): Activating OAKLEY_SHA2_256: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: starting up 1 cryptographic helpers Jul 31 23:43:40 gbox-1 pluto[3352]: started helper (thread) pid=140162780645120 (fd:8) Jul 31 23:43:40 gbox-1 pluto[3352]: Kernel interface auto-pick Jul 31 23:43:40 gbox-1 pluto[3352]: Using Linux 2.6 IPsec interface code on 2.6.32-431.11.2.el6.x86_64 (experimental code) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating aes_ccm_8: Ok (ret=0) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_add(): ERROR: Algorithm already exists Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating aes_ccm_12: FAILED (ret=-17) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_add(): ERROR: Algorithm already exists Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating aes_ccm_16: FAILED (ret=-17) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_add(): ERROR: Algorithm already exists Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating aes_gcm_8: FAILED (ret=-17) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_add(): ERROR: Algorithm already exists Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating aes_gcm_12: FAILED (ret=-17) Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_add(): ERROR: Algorithm already exists Jul 31 23:43:40 gbox-1 pluto[3352]: ike_alg_register_enc(): Activating aes_gcm_16: FAILED (ret=-17) Jul 31 23:43:40 gbox-1 pluto[3352]: Could not change to directory '/etc/ipsec.d/cacerts': / Jul 31 23:43:40 gbox-1 pluto[3352]: Could not change to directory '/etc/ipsec.d/aacerts': / Jul 31 23:43:40 gbox-1 pluto[3352]: Could not change to directory '/etc/ipsec.d/ocspcerts': / Jul 31 23:43:40 gbox-1 pluto[3352]: Could not change to directory '/etc/ipsec.d/crls' Jul 31 23:43:40 gbox-1 pluto[3352]: | selinux support is NOT enabled. Jul 31 23:43:40 gbox-1 pluto[3352]: added connection description "vpn" Jul 31 23:43:40 gbox-1 pluto[3352]: listening for IKE messages Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface eth1/eth1 10.180.3.132:500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface eth1/eth1 10.180.3.132:4500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface eth0/eth0 50.55.153.121:500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface eth0/eth0 50.55.153.121:4500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface lo/lo 127.0.0.1:500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface lo/lo 127.0.0.1:4500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface eth0/eth0 2001:4800:780e:510:acf:6c9b:ffd8:94cd:500 Jul 31 23:43:40 gbox-1 pluto[3352]: adding interface lo/lo ::1:500 Jul 31 23:43:40 gbox-1 pluto[3352]: loading secrets from "/etc/ipsec.secrets" Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: initiating Aggressive Mode #1, connection "vpn" Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: received Vendor ID payload [Cisco-Unity] Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: received Vendor ID payload [XAUTH] Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: received Vendor ID payload [Dead Peer Detection] Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: ignoring Vendor ID payload [FRAGMENTATION c0000000] Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: ignoring Vendor ID payload [Cisco VPN 3000 Series] Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: Aggressive mode peer ID is ID_IPV4_ADDR: '41.78.1.143' Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: received Hash Payload does not match computed value Jul 31 23:43:40 gbox-1 pluto[3352]: "vpn" #1: sending notification INVALID_HASH_INFORMATION to 41.78.1.143:500 Jul 31 23:43:48 gbox-1 pluto[3352]: "vpn" #1: discarding duplicate packet; already STATE_AGGR_I1 Jul 31 23:43:56 gbox-1 pluto[3352]: "vpn" #1: discarding duplicate packet; already STATE_AGGR_I1 Jul 31 23:44:04 gbox-1 pluto[3352]: "vpn" #1: discarding duplicate packet; already STATE_AGGR_I1 Jul 31 23:44:12 gbox-1 pluto[3352]: "vpn" #1: encrypted Informational Exchange message is invalid because no key is knownConfiguration in
ipsec.confversion 2.0 config setup protostack=auto #netkey nat_traversal=yes #forceencaps=yes #plutodebug=none conn vpn type=tunnel authby=secret auto=start pfs=yes ike=3des-sha1;modp1024! phase2alg=3des-sha1; aggrmode=yes left=50.55.153.121 right=41.78.1.143 leftsubnet=10.180.3.132/255.255.128.0 leftnexthop=50.55.153.121 leftsourceip=10.180.3.132 rightsubnet=172.27.176.125/255.255.255.255 rightnexthop=41.78.1.143 rightsourceip=172.27.176.125Configuration in
ipsec.secrets%any %any : PSK "not_the_actual_psk"Output of
ipsec.verify[root@gbox-1 log]# ipsec verify Checking your system to see if IPsec got installed and started correctly: Version check and ipsec on-path [OK] Linux Openswan U2.6.32/K2.6.32-431.11.2.el6.x86_64 (netkey) Checking for IPsec support in kernel [OK] SAref kernel support [N/A] NETKEY: Testing for disabled ICMP send_redirects [FAILED] Please disable /proc/sys/net/ipv4/conf/*/send_redirects or NETKEY will cause the sending of bogus ICMP redirects! NETKEY detected, testing for disabled ICMP accept_redirects [FAILED] Please disable /proc/sys/net/ipv4/conf/*/accept_redirects or NETKEY will accept bogus ICMP redirects! Checking that pluto is running [OK] Pluto listening for IKE on udp 500 [OK] Pluto listening for NAT-T on udp 4500 [OK] Two or more interfaces found, checking IP forwarding [OK] Checking NAT and MASQUERADEing [OK] Checking for 'ip' command [OK] Checking /bin/sh is not /bin/dash [OK] Checking for 'iptables' command [OK] Opportunistic Encryption DNS checks: Looking for TXT in forward dns zone: gbox-1 [MISSING] Does the machine have at least one non-private address? [OK] Looking for TXT in reverse dns zone: 115.171.52.49.in-addr.arpa. [MISSING]Output of
ifconfig[root@gbox-1 ~]# ifconfig eth0 Link encap:Ethernet HWaddr BC:76:4E:04:94:B6 inet addr:50.55.153.121 Bcast:50.55.153.255 Mask:255.255.255.0 inet6 addr: 2001:4800:780e:510:acf:6c9b:ffd8:94cd/64 Scope:Global inet6 addr: fe80::be76:acf:6c9b:ffd8/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:5843131 errors:0 dropped:0 overruns:0 frame:0 TX packets:5444379 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:1587187725 (1.4 GiB) TX bytes:1356473321 (1.2 GiB) Interrupt:246 eth1 Link encap:Ethernet HWaddr BC:76:4E:04:CA:EE inet addr:10.180.3.132 Bcast:10.180.127.255 Mask:255.255.128.0 inet6 addr: fe80::be76:5e32:fd0f:cdae/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:6554243 errors:0 dropped:0 overruns:0 frame:0 TX packets:2800 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:327739177 (312.5 MiB) TX bytes:205160 (200.3 KiB) Interrupt:245 lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:16436 Metric:1 RX packets:10654186 errors:0 dropped:0 overruns:0 frame:0 TX packets:10654186 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:0 RX bytes:9532400622 (8.8 GiB) TX bytes:9532400622 (8.8 GiB)Client's and ours documented VPN information shared
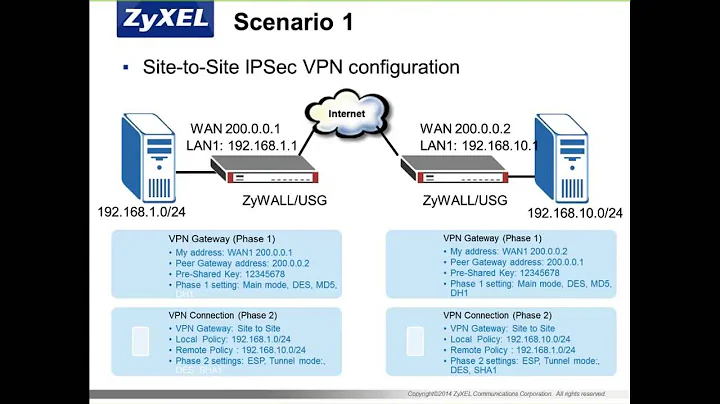
VPN Phase 1
Property | Client's VAS Device | Our VPN Device ===================================================================== Encryption Scheme | IKE | IKE Diffie-Hellman Group | Group 2 | 2 Encryption Algorithm | 3DES | 3DES Hashing Algorithm | MD5 | SHA-1 Main or Aggressive Mode | Main mode | Main Lifetime (for renegotiation) | 28800 seconds | 28800VPN Phase 2
Property | Client's VAS Device | Our VPN Device ===================================================================== Encapsulation (ESP or AH) | ESP | ESP Encryption Algorithm | 3DES | 3DES Authentication Algorithm | SHA1 | SHA1 Perfect Forward Secrecy | NO PFS | Yes, Group-2 Lifetime (for renegotiation) | 3600 seconds | 3600 Lifesize (for renegotiation) | Not Used | Key exchange for Subnets | Yes |Gateway Device Info
Property | Client's VAS Device | Our VPN Device ===================================================================== IP Address | 41.78.1.143 | 50.55.153.121 VPN Device Description | Cisco ASA 5510 | OpenSwan DN Information of VPN Gateway | | (if using certificates) | NA | Encryption Domain | 172.27.176.125-126 | 10.180.3.132

![Burp Suite - Part 13 - Intruder IV - [Jr. Penetration Tester Path]](https://i.ytimg.com/vi/6q8AeZS7Jvo/hqdefault.jpg?sqp=-oaymwEcCOADEI4CSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLCnE6OMaQLDFZWg_bjK6n5bhsX8wA)