troubling anonymous Logon events in Windows Security event log
The "anonymous" logon has been part of Windows domains for a long time--in short, it is the permission that allows other computers to find yours in the Network Neighborhood, find what file shares or printers you are sharing, etc.
It is also why Windows admins say never to grant share permissions to the "Everyone" group (unless you know what you are doing), because "Everyone" also includes "no one"--er, ANONYMOUS. Rest assured that unless you
Anyway, in this case you probably want to lock it down with Registy settings or better yet, Local or Group Policies. Look in your policy editor under Computer Configuration\Windows Settings\SecuritySettings\Local Policies\SecurityOptions for the following options:
- Network access: Allow anonymous SID/Name translation
- Network access: Do not allow anonymous enumeration of SAM accounts
- Network access: Do not allow anonymous enumeration of SAM accounts and shares
- Network access: Let Everyone permissions apply to anonymous users
- Network access: Named Pipes that can be accessed anonymously
- Network access: Shares that can be accessed anonymously
Related videos on Youtube
blackcoil
Updated on September 17, 2022Comments
-
blackcoil almost 2 years
I have a dedicated server hosted on Rackspace Cloud, and this morning as I was casually checking the Security event log, I saw a series of successful Logon events that are troubling. It appears random IPs are successfully "logging in" to my server somehow. How is this possible? I have a very strong Administrator password. Am I overreacting here, or does it look like someone is accessing my server somehow? There are about 50 of these within an hour time span, from different IP addresses.
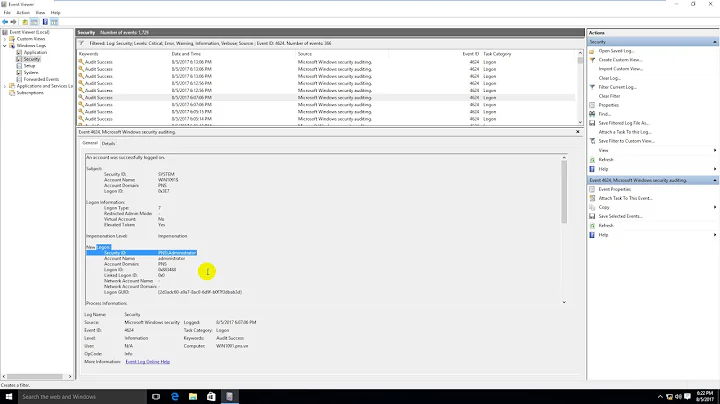
An account was successfully logged on. Subject: Security ID: NULL SID Account Name: - Account Domain: - Logon ID: 0x0 Logon Type: 3 New Logon: Security ID: ANONYMOUS LOGON Account Name: ANONYMOUS LOGON Account Domain: NT AUTHORITY Logon ID: 0x20a394 Logon GUID: {00000000-0000-0000-0000-000000000000} Process Information: Process ID: 0x0 Process Name: - Network Information: Workstation Name: ATBDMAIN2 Source Network Address: 76.164.41.214 Source Port: 36183 Detailed Authentication Information: Logon Process: NtLmSsp Authentication Package: NTLM Transited Services: - Package Name (NTLM only): NTLM V1 Key Length: 128
So is it likely someone was port scanning or looking for vulnerabilities, or why else would some random IPs from around the world want to know about my server?
-
Mark about 4 yearsIf you want to exclude anonymous and guest uesrs, rather than specifying Everyone you can specif Authenticated Users. Allowing "everyone" to connect is useful when people don't have to authenticate to your server (e.g. many web-sites allow people to read content anonymously)