What is the difference between NAT OUTPUT chain and NAT POSTROUTING chain?
Solution 1
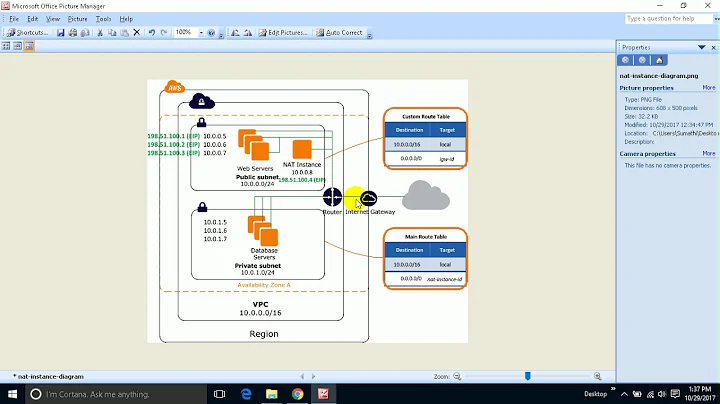
Have a look at this diagram. The green boxes are for iptables, the blue are for ebtables (ignore those).
So you see that the OUTPUT chain is only traversed for packets produced by local applications, while the POSTROUTING chain is traversed by all packets, including those routed from somewhere else.
There are two subcases for network address translation (NAT): SNAT translates the source address of the packet, while DNAT translates the destination address of the packet.
You are restricted in which chains you can do either: nat/PREROUTING and nat/OUTPUT can do DNAT, while nat/POSTROUTING and possibly nat/INPUT (not sure if this still works) can do SNAT.
Solution 2
@ x-yuri I was also confused about output NAT but finally I got the answer. Prerouting & Postrouting NAT are both for external NAT when some packets are coming to your interface or going out of it and you wanna NAT the address. But OUTPUT NAT is for your local network NAT, I mean when the packets are starting from your application. I think this is a good example to figure it out better. When you wanna change the port and IP address of a traffic as a transparent proxy such as what we do in Nginx. We can use something like this:
iptables -t nat -A OUTPUT -p tcp --dport 80 -j DNAT --to-destination 192.168.100.10:8080
you send traffic on port 80 to the other host on your network 192.168.100.10 which is listening on it's port 8080
I think it's the point I hope it is true and what you were asking for
Related videos on Youtube
ArjunCh
Updated on September 18, 2022Comments
-
ArjunCh over 1 year
IF Nating is done in OUTPUT chain of the NAT table, then what is the function of SNAT in POSTROUTING
-
derobert over 6 yearsAccording to your table (posted as an image — please fix that. Just copy and paste the descriptions; it doesn't have to be perfect) the OUTPUT table is only for traffic from the firewall itself (local sockets), e.g., not for forwarded traffic from machines "behind" it. Not sure what else you're looking for, could you clarify?
-
-
x-yuri almost 5 yearsCan you explain how
nat/OUTPUTallows to do DNAT? My understanding is that you DNAT incoming packages, and SNAT outcoming ones. Andnat/OUTPUTprocesses the outcoming ones. Which means it allows to do SNAT. What am I missing here? -
dirkt almost 5 years@x-yuri I can't explain the design choice of the kernel developers, and I've often been in a situation where I would have needed it the other way around (or just be able to DNAT and SNAT or any sort of rewriting everywhere). That said, packets incoming from a network interface are apparently treated the same way as packets "incoming" from an application to the kernel through the OUTPUT chain, hence both can do DNAT.
-
x-yuri almost 5 yearsIndeed, I can see here a brief mention that the OUTPUT chain can be used for DNAT. But what I don't understand is not the kernel developers' decision. According to the diagram you mentioned
nat/OUTPUTcomes after the reroute check. Which means you can't change the destination. Now that I think about it, that's probably a mistake. Or it may not reflect the current state of affairs. -
x-yuri almost 5 years...But if
nat/OUTPUTis for DNAT, why would I need that? I can see a case where I'm behind a router, and the packets coming from the internet gets DNAT'ed on the router. But why would I need to DNAT packets coming from a local application? -
dirkt almost 5 yearsSorry, as I said, I can't explain the "why". If I had designed it, I'd have allowed rewriting in any way everywhere. I have no idea where those restrictions come from, or if they are even necessary.
![IPTABLES [PART-1] : "UNDERSTANDING THE CONCEPT"](https://i.ytimg.com/vi/vbhr4csDeI4/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLBovKYd5heeT0eQFP4enqBJ_GCa1Q)