Why Firefox alert me about HTTPs "Untrusted" Connection on Positivessl - Comodo certificate?
Although you did install a SSL certificate, you did not include any additional certificates that are necessary to build a trust path. See https://www.ssllabs.com/ssltest/analyze.html?d=phrecordr.com
About the trust path, the SSL client has some root certificates that are stored. When you buy a certificate C from some CA, they might use some intermediate certficate (let's call this B) that is signed by the root CA A. If you only provide the certificate C to the client, then they will not be able to establish a trust path from A to C. To fix this, append the certificate B to your certificate C.
The exact details depend on the SSL server that you are using, consult their documentation for the specifics.
Related videos on Youtube
lito
Updated on September 18, 2022Comments
-
lito over 1 year
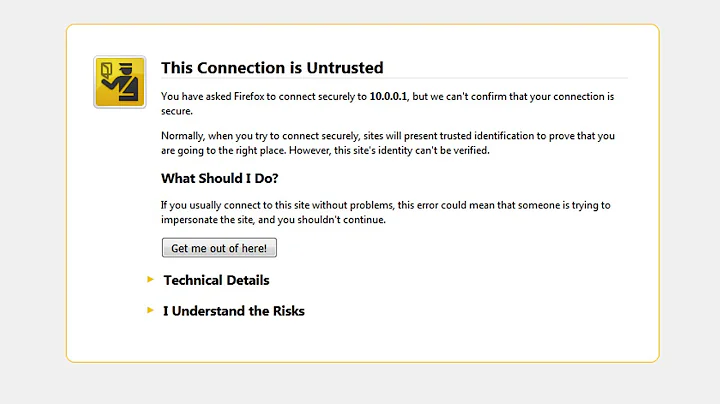
For my new startUp I got a SSL certificate from Comodo.com. I did all the painful process and finally I was able to implement it on my AWS server (I'm running MEAN Stack). Now when someone visit my website using Firefox the got this error:
Technical Details
Invalid security certificate.
The certificate is not trusted because no issuer chain was provided. (Error code: sec_error_unknown_issuer)
But obviously I don't want my users to receive that warning.
I thought that maybe the server was delivering some file by the regular http and I couldn't find any non-https content, so I imagine I'm ok about that issue (maybe not)
This is my first time using a SSL certificate and maybe I'm doing it wrong. Please if you can help me out will be great. Thanks
Here is the image:

-
lito almost 10 yearsThanks @Lekenstey, I received these files from PositiveSSL:
mydomain_com.ca-bundleandmydomain_com.crt. I am using NodeJS/ExpressJS. I took a look at the the documentation but I'm not an expert and is taking me hard times, what should I change? http://nodejs.org/api/https.html#https_server_listen_handle_callback. This is my NodeJS codevar credentials = {key: privateKey, cert: certificate, pfx:authorityChain.ca-bundle}; -
Lekensteyn almost 10 years@lito If I'm not mistaken, you should key + cert or pfx, not both. If you have a single file (for
pfx) with keys and certs concatenated, you should append the CA bundle to that file. Otherwise, append the file to the cert. I suggest to keep the keys and certs separate anyway so you can set very tigh permissions on the keys. -
Lekensteyn almost 10 yearsYou should not include the root CA. It is no use (it does not help in building a trust path) and enlarges the initial handshake size. Please test your setup with the ssllabs tool I linked above.
-
David Rice over 9 yearsProbably easiest to just supply in the ca field: ` var options = { key: fs.readFileSync(key), cert: fs.readFileSync(cert), ca: fs.readFileSync(chainCert) };` ca can also be an array of certs if you have multiple.

![[FIXED] Error Secure Connection Failed All Browsers Problem](https://i.ytimg.com/vi/sbah5QvA-4o/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLCfFovor9e0A_v6UFVGcjqM_DUImg)

![How to fix Secure Connection Failed issue in Firefox? [Solved]](https://i.ytimg.com/vi/IX_zkNAWx0c/hqdefault.jpg?sqp=-oaymwEcCOADEI4CSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLDrPA9WzX0M95C8rDuBoj_k_pVWSQ)