AWS Fargate + Application Load Balancer SSL Termination
9,147
Yes it is possible.
- Create a SSL certificate for your domain in ACM (Amazon Certificate Manager).
- Create a HTTPS Listener in the ALB that will listen on port 443 and configure it to use the above SSL Certificate.
- Open the ALB Security Group to permit inbound traffic on port 443.
That's it, pretty much. The ALB must have one Listener per port, so if you are accepting traffic on both HTTP/80 and HTTPS/443 you'll need 2 listeners.
The Target Group doesn't change, it will still connect to your Fargate containers over HTTP.
Hope that helps :)
Related videos on Youtube
Author by
Jeremy Blalock
Updated on September 18, 2022Comments
-
Jeremy Blalock over 1 year
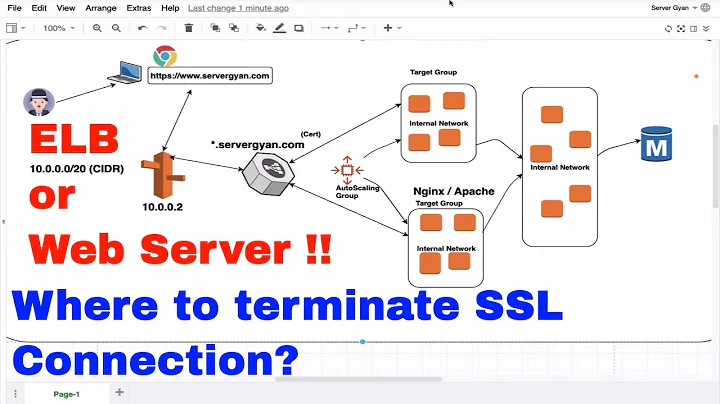
I'm trying to configure ECS Fargate behind an Application Loader Balancer (ELBv2), and I would like to terminate the TLS/SSL connections on the ALB, and send HTTP traffic (port 80) to the Fargate images, which listen on port 80.
This is the diagram of what I'm trying to do:
- I am currently able to send HTTP traffic from the internet to Fargate, but I have not found a way to terminate the TLS connection at the Application Loader Balancer and forward HTTP traffic to ECS. Is this possible?
- I am hosting a fairly static application with no sensitive user data, hence I am not particularly worried about data in transit between the ALB and ECS.
Any help appreciated!
-
Stefano almost 5 yearsAs an aside, you can also configure the ALB to redirect any traffic arriving on 80 to go to 443: docs.aws.amazon.com/elasticloadbalancing/latest/application/…
-
Mark Entingh over 4 yearsWhat about encrypting the response back to the client via TLS? How would you set that up? In my case, the ALB is on a public subnet, ECS is on a private subnet, and my NAT sends traffic from ECS back to the client
-
 MLu over 4 years@MarkEntingh Are you sure that the the return traffic goes thriugh NAT and not through the ALB? That’d be quite unusual, perhaps if you’re using some obscure protocol over multiple ports that may be the case. Normal HTTPS or WebSocket traffic simply goes back through the same ALB and is therefore TLS protected between the client and ALB in both directions.
MLu over 4 years@MarkEntingh Are you sure that the the return traffic goes thriugh NAT and not through the ALB? That’d be quite unusual, perhaps if you’re using some obscure protocol over multiple ports that may be the case. Normal HTTPS or WebSocket traffic simply goes back through the same ALB and is therefore TLS protected between the client and ALB in both directions.