Can't make httpd use correct SSL
Solution 1
SSLCACertificateFile /var/cosign/certs/CA/publickey.pem
Unless that PEM file actually contains the CA certificate for the client certificates you wish to grant access, this is incorrect; to provide apache with a certificate chain, use SSLCertificateChainFile instead.
Apache must have the actual certificate and any intermediate certificates used to sign/produce the endpoint certificate, up to and including a root certificate that is trusted by browsers.
To verify the certificate they gave you, run:
openssl verify -CApath /path/to/CA/certs -purpose sslserver -verbose /your/certificate
Quite apart from the certificate issues, you're missing an SSLRequireSSL directive in your vhost; without it, apache will not check for a secure connection.
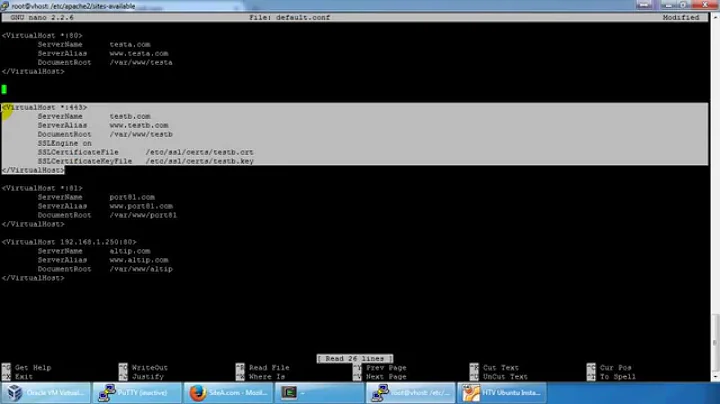
You should also not use _default_ as the virtualhost, and you're missing a ServerName.
Use either *:443 or IP:443 as the virtualhost.
Every vhost must have a valid ServerName set, and in addition, an SSL vhost must have a ServerName that corresponds to the certificate's CN.
For example:
<VirtualHost 1.2.3.4:443>
ServerName your.certificates.common.name
ServerAlias any.subject.alternate.names
DocumentRoot /your/protected/content
SSLEngine On
SSLCertificateChainFile /path/to/your/issuers/CA/cert/bundle
SSLCertificateFile /path/to/your/certificate.crt
SSLCertificateKeyfile /path/to/your/private.key
-OR-
SSLCertificateFile /path/to/your/combined.cert-and-keyfile
SSLRequireSSL
</VirtualHost>
Study the documentation for a bit.
Solution 2
Run
# Debian/Ubuntu
apache2ctl -S
# RHEL/CentOS
httpd -S
It should produce something like this:
*:443 is a NameVirtualHost
default server hostname (/etc/apache2/sites-enabled/000-default:1)
port 443 namevhost hostname (/etc/apache2/sites-enabled/000-default:1)
Verify that you run the openssl command with the correct hostname to access your vhost, I'm assuming you have multiple vhosts for port 443 and the one that was defined in your distro's default setup takes precedence.
Related videos on Youtube
monkeymatrix
A regular bloke that often struggles with the odd bit of code.
Updated on September 18, 2022Comments
-
monkeymatrix almost 2 years
I have a signed CA, issued by my university. I generated my CSR using their public key file as so:
openssl genrsa -out myservername.key 2048 (new key) openssl req -new -key myservername.key -out myservername.csrI sent them the CSR, they sent me back the signed .crt file.
I created a directory for my CA keys and certs and placed them in there.
The relevent part of my httpd.conf looks like this:
<VirtualHost _default_:443> SSLEngine on SSLCACertificateFile /var/cosign/certs/CA/publickey.pem SSLCertificateFile /var/cosign/certs/myserver.crt SSLCertificateKeyFile /var/cosign/certs/myserver.key DocumentRoot /var/www/html/ <Directory /var/www/html> Options -Indexes AllowOverride All </Directory>But it's not using this certificate for SSL. If I do this command:
openssl s_client -connect localhost:443 -showcertsI get this:
CONNECTED(00000003) depth=0 C = --, ST = SomeState, L = SomeCity, O = SomeOrganization, OU = SomeOrganizationalUnit, CN = portcharlotte, emailAddress = root@portcharlotte verify error:num=18:self signed certificate verify return:1 depth=0 C = --, ST = SomeState, L = SomeCity, O = SomeOrganization, OU = SomeOrganizationalUnit, CN = portcharlotte, emailAddress = root@portcharlotte verify return:1 --- Certificate chainMy CSR contained proper details, not this 'SomeState', 'SomeCity' nonsense which I'm guessing is a default.
The openssl module is installed, and loaded.
The only errors I get in logs are:
[Fri Jan 25 13:27:40 2013] [warn] RSA server certificate is a CA certificate (BasicConstraints: CA == TRUE !?) [Fri Jan 25 13:27:40 2013] [warn] RSA server certificate CommonName (CN) `portcharlotte' does NOT match server name!?I'm guessing this mismatch is because it's using the wrong certificate.
My question is, how do I make it use the correct one? What am I missing?
-
adaptr over 11 yearsThere will never be an entry for a
port 80 namevhost hostnameunder a *:443 list.