Disable SSLv3 in major browsers
Solution 1
I've published a blog on how to disable SSLv3 in some of the most common bowsers and server platforms: https://scotthelme.co.uk/sslv3-goes-to-the-dogs-poodle-kills-off-protocol/
Below are the key details.
How to protect your server
The easiest and most robust solution to POODLE is to disable SSLv3 support on your server. This does bring with it a couple of caveats though. For web traffic, there are some legacy systems out there that won't be able to connect with anything other than SSLv3. For example, systems using IE6 and Windows XP installations without SP3, will no longer be able to communicate with any site that ditches SSLv3. According to figures released by CloudFlare, who have completely disabled SSLv3 across their entire customer estate, only a tiny fraction of their web traffic will be affected as 98.88% of Windows XP users connect with TLSv1.0 or better.
Apache
To disable SSLv3 on your Apache server you can configure it using the following.
SSLProtocol All -SSLv2 -SSLv3
This will give you support for TLSv1.0, TLSv1.1 and TLSv1.2, but explicitly removes support for SSLv2 and SSLv3. Check the config and then restart Apache.
apachectl configtest
sudo service apache2 restart
NginX
Disabling SSLv3 support on NginX is also really easy.
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
Similar to the Apache config above, you will get TLSv1.0+ support and no SSL. You can check the config and restart.
sudo nginx -t
sudo service nginx restart
IIS
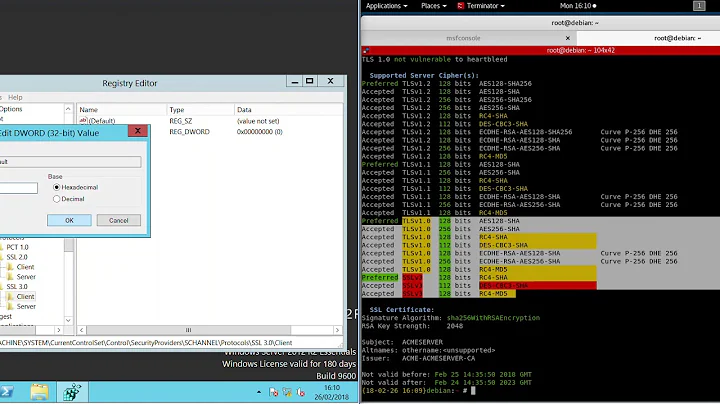
This one requires some registry tweaks and a server reboot but still isn't all that bad. Microsoft have a support article with the required information, but all you need to do is modify/create a registry DWORD value.
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders \SCHANNEL\Protocols
Inside protocols you will most likely have an SSL 2.0 key already, so create SSL 3.0 alongside it if needed. Under that create a Server key and inside there a DWORD value called Enabled with value 0. Once that's done reboot the server for the changes to take effect.

How to check your server
The easiest and probably the most widely used method to test anything to do with your SSL setup is the Qualys SSL Test. Simply navigate to the site, enter the domain for the website you want to test and hit submit to start the test.

Once the test has finished, you will get a nice summary of your results and a lot of detailed information further down the page. Specifically, you want to look in the Configuration section at your supported protocols.

What you want to see here is that you have no SSL protocols supported. You should have long since disabled SSLv2.0 and now we've just removed SSLv3.0 too. Supporting TLSv1.0 or better is good enough to support the absolute vast majority of internet users out there without exposing anyone to unecessary risk.
How to protect your browser
It is also possible to protect yourself from POODLE by disabling SSLv3 support in your browser. This means that even if the server does offer SSLv3 support, your browser will never use it, even during a protocol downgrade attack.
Firefox
Firefox users can type about:config into their address bar and then security.tls.version.min into the search box. This will bring up the setting that needs to be changed from 0 to 1. The existing setting allows Firefox to use SSLv3 where it's available and if it's required. By changing the setting you will force Firefox to only ever use TLSv1.0 or better, which is not vulnerable to POODLE.

Chrome
Chrome users don't have an option in the GUI to disable SSLv3 as Google removed it due to confusion over whether SSLv3 or TLSv1 was better with one having a higher numeric value. Instead you can add the command line flag --ssl-version-min=tls1 to enforce the use of TLS and prevent any connection using the SSL protocol. In Windows, right click on your Chrome shortcut, hit Properties and add the command line flag as seen in the image below.

If you use Google Chrome on Mac, Linux, Chrome OS or Android, you can follow these instructions here.
Internet Explorer
Fixing up Internet Explorer is also pretty easy. Go to Settings, Internet Options and click on the Advanced tab. Scroll down until you see the Use SSL 3.0 checkbox and uncheck it.

How to check your browser
If you want to check that your browser changes have definitely removed SSLv3.0 support there are a couple of sites that you can use. If you visit https://zmap.io/sslv3/ with SSLv3 enabled in your browser, you will see the warning message I'm getting here in Chrome where I haven't yet disabled SSLv3. To double check the site was working as expected, I disabled SSLv3 support in Internet Explorer and opened up the site there too. Here you can see the difference.

You can also try https://www.poodletest.com/ alongside Zmap.
Solution 2
Opera 12.16 (Linux & Windows)
- Go to opera:config#SecurityPrefs|EnableSSLv3
- Uncheck
Enable SSL v3 -
Click Save and restart Opera
Related videos on Youtube
LyK
Updated on September 18, 2022Comments
-
LyK over 1 year
As the question suggests: How to disable support of the SSL version 3 and set TLS version 1 as minimum (oldest) protocol supported in order to defend against POODLE.
One can test a browser with this test.
Basically, I haven't found a solution for Safari yet.
-
LyK over 9 yearsThanks for the additions regarding the servers! (even though they are not browsers :P) What remains is the way to do this in Safari.. :/
-
itscooper over 9 yearsThe Opera devs have put a good countermeasure into 25 as well: blogs.opera.com/security/2014/10/… (since I guess those prefs are only available pre-Chromium)
-
 jww over 9 yearsGreat post. You seem to have omitted Opera (its the reason I am here).
jww over 9 yearsGreat post. You seem to have omitted Opera (its the reason I am here). -
Knyri over 9 yearsIf you have Opera 25 you can use the instructions for Chrome to disable SSLv3. Worked for me.