Disabling weak ciphers
Guessing the registry keys would be created here.
You don't have to guess. Le Microsoft KB:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel]
"EventLogging"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Ciphers]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\CipherSuites]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Hashes]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\KeyExchangeAlgorithms]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols\SSL 2.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols\SSL 2.0\Client]
"DisabledByDefault"=dword:00000001
So your hunch was close, but note the Ciphers subkey when you want to enable/disable ciphers, and the Protocols subkey when you want to disable/enable entire protocols.
So for instance, if you want to disable RC4, create several new keys, one for each different key size that could be used in RC4:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 64/128
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128
In each one of those keys, you need to create the new value:
Enabled REG_DWORD 0
If you wanted to disable, for example, the entire SSL v2 protocol, create the keys:
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client
HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
Inside each key, make two new values:
Enabled DWORD 0
DisabledByDefault DWORD 1
Note that these policies only affect applications which link to/call into Schannel.dll... so IIS, Internet Explorer, Remote Desktop, etc. These settings will not affect applications that use other SSL libraries such as OpenSSL.
Related videos on Youtube
user3329963
Updated on September 18, 2022Comments
-
user3329963 over 1 year
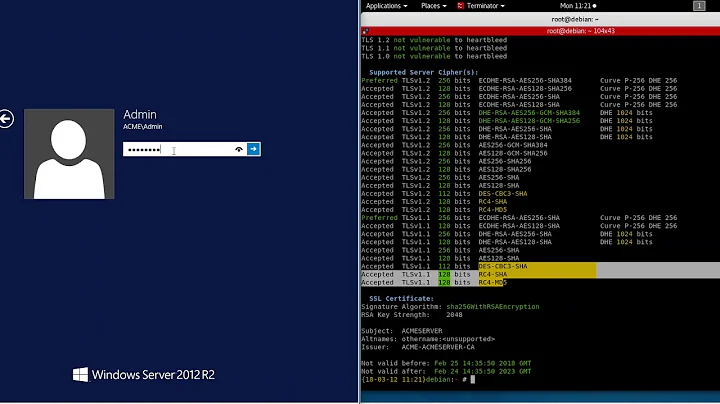
Does anyone have any experience disabling weak ciphers on Windows Registry? Server doesn't have IIS installed. Below is the results of my security scan but not 100% what registry entries should be added, i've disabled whole protocols via the registry before but never individual ciphers.
Guessing the registry keys would be created here.
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Here is the list of weak SSL ciphers supported by the remote server :
Low Strength Ciphers (< 56-bit key) TLSv1 EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES-CBC(40) Mac=SHA1 export EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES-CBC(40) Mac=SHA1 export EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export The fields above are : {OpenSSL ciphername} Kx={key exchange} Au={authentication} Enc={symmetric encryption method} Mac={message authentication code} {export flag}