Using SSLv3 - Enabling Strong Ciphers Server 2008
If you haven't touched the configuration, strong ciphersuites are enabled by default. The list of default ciphersuites in Vista and Server 2008 is on MSDN.
What you listed are not quite ciphersuite names, as they are missing pieces. AES128-SHA is just part of it. A ciphersuite has few parts - key exchange algorithm, encryption/decryption algorithm, and hmac algorithm, so the AES128-SHA example is missing key exchange algorithm. A proper name will be TLS_RSA_WITH_AES_128_CBC_SHA.
I would recommend ssllabs.com for testing publicly reachable web servers.
Related videos on Youtube
Admin
Updated on September 17, 2022Comments
-
 Admin over 1 year
Admin over 1 yearI've disabled SSLv2 and SSLv3 is on. However I cannot connect to a remote server which fails with
The client and server cannot communicate, because they do not possess a common algorithm
Ran an SSL check (http://www.serversniff.net/sslcheck.php) on the remote server and ours, and noticed none of the ciphers they accept we have on our server. How can this be configured? (Windows Web Server 2008)
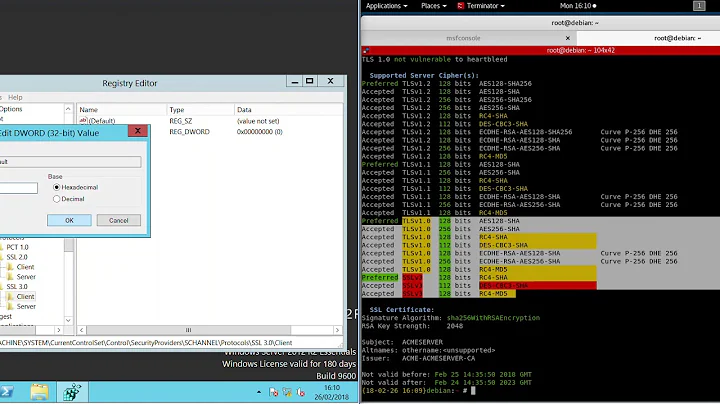
Remote Server Accepted SSL ciphers:
DHE-RSA-AES256-SHA AES256-SHA EDH-RSA-DES-CBC3-SHA DES-CBC3-SHA DHE-RSA-AES128-SHA AES128-SHAOur server by default accepts:
DES-CBC3-SHA RC4-SHA RC4-MD5 -
 grasshopper over 13 yearsThanks for the comment. I just thought that might have been the issue as the real problem is: "The client and server cannot communicate, because they do not possess a common algorithm." - msxml6.dll error '80090331'
grasshopper over 13 yearsThanks for the comment. I just thought that might have been the issue as the real problem is: "The client and server cannot communicate, because they do not possess a common algorithm." - msxml6.dll error '80090331' -
Nasko over 13 yearsThe error most likely doesn't come from MSXML.DLL, rather from the security subsystem on Windows. Look in the event log for logs from the "Schannel" component, which implements SSL/TLS on Windows. There might be some clues there. Did you actually resolve the issue?
-
 grasshopper over 13 yearsNo I never managed to resolve this issue. The only workaround was to use ASP.NET's HttpWebRequest component and most importantly, specify this: "System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Ssl3"
grasshopper over 13 yearsNo I never managed to resolve this issue. The only workaround was to use ASP.NET's HttpWebRequest component and most importantly, specify this: "System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Ssl3" -
Nasko over 13 yearsWhat is the machine you are trying to authenticate to? If it is publicly reachable, I can take a peek at what it supports and see if there is anything I can spot.
-
 grasshopper over 13 yearsThanks Nasko, the remote site has reenabled TLSv1 and the original code all works now. It seems theres no way to force SSLv3 using ServerXMLHTTP. Thanks for all your help.
grasshopper over 13 yearsThanks Nasko, the remote site has reenabled TLSv1 and the original code all works now. It seems theres no way to force SSLv3 using ServerXMLHTTP. Thanks for all your help. -
fuero about 11 yearsyou didn't answer the question asked.