How can I set up Redmine => Active Directory authentication?
Solution 1
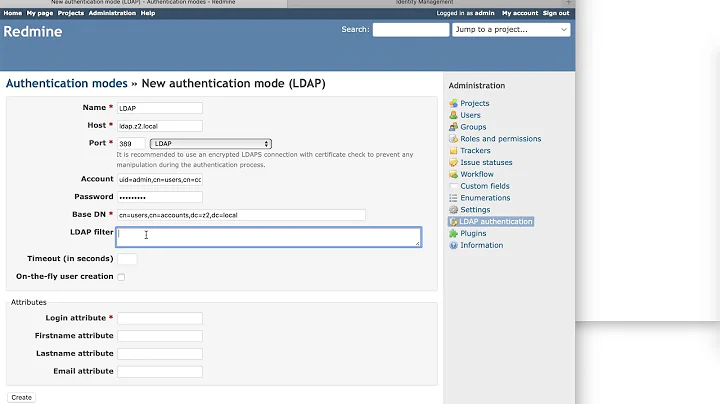
Okay, so here are the specific settings that I needed in order to make this work:
Host: ims.example.com
Port: 389
User: MYDOMAIN\accountName
Password: *******
Base DN: dc=mydomain,dc=example,dc=com
On-The-Fly User Creation: YES
Login: sAMAccountName
Firstname: givenName
Lastname: sN
Email: mail
The trick was removing cn=Users from the Base DN, after which it all sort of came together.
The other notable thing was the inclusion of a user to read the directory.
Lastly, the user that logs in uses their user name without domain qualification, and their domain password as usual. Our domain does not require an email address, so there is an additional step where the email address has to be set during user creation, but that's pretty straightforward.
Solution 2
A trick to find the Base DN for ActiveDirectory LDAP authentication is to check what the users fully qualified domain name is. you can check that with:
whoami /FQDN
if you are logged in as that user, which returns something like
CN=John Doe,OU=users,OU=department,DC=corp,DC=domain,DC=com
and the Base DN can be found by removing the first CN.
OU=users,OU=department,DC=corp,DC=domain,DC=com
Solution 3
I have no familiarity with Redmine, but it sure looks like you're trying to do an anonymous bind to Active Directory to validate credentials. That's not going to work. Having configured multiple products for LDAP integration with AD, this is a common problem that I've seen.
Out of the box, AD requires that clients authenticate when binding to the directory to perform queries.
Have a look at this Redmine wiki posting re: configuring LDAP authentication. They're talking about specifying an account and password for Redmine to use (one that has rights to read the directory-- a plain ol' "Domain User" will do) to bind to the directory.
Solution 4
Use an ldap browser and visually check the structure... luma on ubuntu works well, ldapper for the mac also.
Related videos on Youtube
Chris R
Updated on September 17, 2022Comments
-
Chris R over 1 year
First, I'm not an AD admin on site, but my manager has asked me to try to get my personal Redmine installation to integrate with ActiveDirectory in order to test-drive it for a larger-scale rollout.
Our AD server is at host:port
ims.example.com:389and I have a userIMS/me.Right now, I also have a user
mein Redmine using local authentication.I have created an ActiveDirectory LDAP authentication method in RedMine with the following parameters:
Host: ims.example.com Port: 389 Base DN: cn=Users,dc=ims,dc=example,dc=com On-The-Fly User Creation: YES Login: sAMAccountName Firstname: givenName Lastname: sN Email: mailTesting this connection works just fine.
I have, however, not successfully authenticated with it.
I've created a backup admin user so that I can get back in to the
meaccount if I break things, and then I've tried changingmeto use the ActiveDirectory credentials. However, once I do, nothing works to log in. I have tried all of these login name options:meIMS/meIMS\me
I've used my known Domain password, but no joy.
So, what setting do I have wrong, or what information do I need to acquire in order to make this work?
-
Chris R over 14 yearsWhat form should I put the username in? They don't really explain that in the wiki posting (which was my starting point for this process anyway)
-
Chris R over 14 yearsSpecifically, I tried
IMS\meand it didn't seem to work. I can't get any details on why it's failing, either. -
Spence over 14 yearsI'd specify the bind username in DOMAIN\samAccountName syntax. As far as figuring out why it's failing, I'd recommend getting a sniffer (tcpdump, wireshark, built-in Microsoft "Network Monitor", etc) out and bringing that to bear on the problem. There's no quicker way to figure out what's being said on the wire than to look at what's being said on the wire. (It sounds silly, but a lot of people don't ever think to look there...) Then, at least, you can see if the parameters you've specified are being passed as you expect them to be.
-
Chris R over 14 yearsWireshark is turning out to be a godsend here. Thanks for that tip. I've found some issues for it, and I'll be coming through and posting the details shortly.
-
Spence over 14 yearsSeeing what the boxes are saying to each other makes the cause of a lot of problems instantly clear. Glad to hear you got it working!
-
Spence over 14 yearsAhh... I didn't even think about asking you if your user accounts were under the "CN=Users, ..." default container or not.
-
Chris R over 14 yearsIt would be more useful to know how I could have determined that. I only arrived at this setup through trial and error.
-
Chris R almost 14 yearsIt didnt't actually work with my LDAP server, but I can see how it'd be useful.
-
 Ben Kreeger almost 12 yearsThis was largely trial and error for me, too, as I've hand-rolled my own AD authentication plugin for Devise that doesn't even require a specific AD Read account; it binds and authenticates to AD using the username/password logging in. This was mega helpful, Chris, thanks.
Ben Kreeger almost 12 yearsThis was largely trial and error for me, too, as I've hand-rolled my own AD authentication plugin for Devise that doesn't even require a specific AD Read account; it binds and authenticates to AD using the username/password logging in. This was mega helpful, Chris, thanks. -
coz over 11 yearsOne clarification (it took me an entire afternoon): The account needs to be formatted as a distinguished name - not a login name.
-
 Andy Arismendi about 11 yearsFor me the fix as adding the domain to the query user account e.g. the MYDOMAIN part.
Andy Arismendi about 11 yearsFor me the fix as adding the domain to the query user account e.g. the MYDOMAIN part. -
jasonmmiraglia over 8 yearsThanks for this. I was unaware of this command, very helpful.
-
user1066698 about 2 yearsWow I was having the same problem, thanks for the tip, solved everything in a sec. Thank you.