ldapsearch - Strong(er) authentication required - Transport encryption required
Are you sure TLS is even configured in your Active Directory deployment? It is not by default.
Anyhow using LDAPS (default port 636):
ldapsearch -H ldaps://10.128.1.254
Using LDAP and enforce StartTLS extended operation to succeed (default port 389):
ldapsearch -H ldap://10.128.1.254 -ZZ
Note that OpenLDAP's client utils perform strict TLS hostname check. Therefore the server certificate must contain the DNS name or IP address used with -H in the cert's subjectAltName or CN attribute.
If you want to use SASL with GSSAPI/Kerberos you have to obtain a Kerberos ticket-granting ticket before with kinit.
Related videos on Youtube
BrainStone
Updated on September 18, 2022Comments
-
BrainStone over 1 year
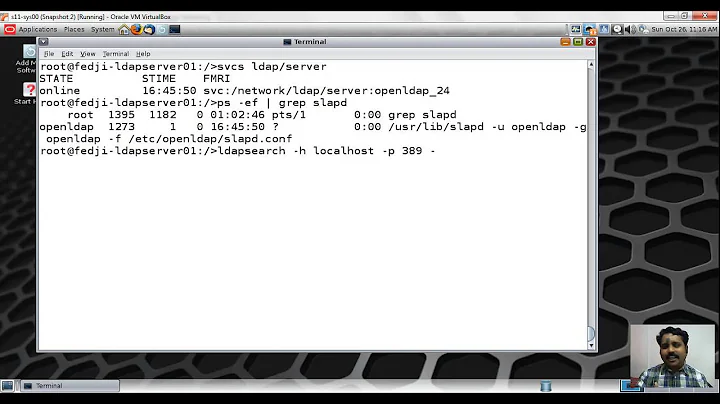
I'm trying search my company's AD with
ldapsearch. However I always get the error:ldap_bind: Strong(er) authentication required (8) additional info: BindSimple: Transport encryption required.I tried to use LDAPS in every combination possible, but I can't seem to be able to connect to the server in any other way than just LDAP on the default port.
Weirdly enough I have no issues whatsoever using Active Directory Explorer.I was thinking that it could be that the firewall isn't configured correctly and blocking the LDAPS (636) Port, but that wouldn't explain Active Directory Explorer working...
Also GitLab seems to be able to connect to it just fine too. Except that it won't authenticate. But that's what I'm trying to debug with
ldapsearchtoo.That's the command I'm using:
ldapsearch -D "cn=myuser,cn=Users,dc=company,dc=local" -w "<password>" \ -p 389 -h 10.128.1.254 \ -b "cn=Users,dc=company,dc=local"The server is correct, so is the bind_dn (according to Active Directory Explorer) and the corresponding password, I tried using upper an lowercase for the stuff like
cn, I tried all possible configurations of using LDAPS (like-H ldaps://10.128.1.254,-H ldaps://10.128.1.254:389,-H ldaps://10.128.1.254:636) and the flag-x, so I'm really running out of ideas.If it's relevant, the AD server is the Active Directory Server on Synology/DSM, which is a linux SAMBA server under the hood.
Any help is greatly apprechiated.
UPDATE:
Looks like adding
-Y NTLMgets me further.Now I get:
SASL/NTLM authentication started ldap_sasl_interactive_bind_s: Invalid credentials (49) additional info: SASL:[NTLM]: NT_STATUS_OBJECT_NAME_NOT_FOUNDwhich is weird, as I know the password is correct.
UPDATE 2:
Now using
-Y GSSAPIcreates this rather nothing saying error:SASL/GSSAPI authentication started ldap_sasl_interactive_bind_s: Local error (-2) additional info: SASL(-1): generic failure: GSSAPI Error: Unspecified GSS failure. Minor code may provide more information (No Kerberos credentials available (default cache: FILE:/tmp/krb5cc_0))
UPDATE 3:
The parameter
-ZZ(-Ztoo) ends with this error:ldap_start_tls: Connect error (-11) additional info: The TLS connection was non-properly terminated. -
BrainStone over 5 yearsI’m certainly not using LDAPS. I’ve also tried it with the
Hparameter as you showed it in your second example. That leads me to the same error messages as before. -
Michael Ströder over 5 yearsYou mentioned port 636 which is the default port for LDAPS. Anyhow, did you try to use StartTLS ext.op. instead like described in my 2nd example?
-
BrainStone over 5 yearsMy apologies. On mobile the last parameter was cut off. I will try that.
-
BrainStone over 5 yearsSorry for the late response. I was not at work and unable to test it. Adding the
-ZZparameter yields:The TLS connection was non-properly terminated.. I've added the full error as Edit 3 in the original post. -
Michael Ströder over 5 yearsI repeat the first sentence of my answer: Are you sure TLS is even configured in your Active Directory deployment? It is not by default.
-
BrainStone over 5 yearsI honestly don't know. The interface on the Synology proivides exactly 0 configuration. And about just as much information.
-
Michael Ströder over 5 yearsSo I'd assume that using TLS is not supported because you would at least need a config option to add CA root certificate and TLS server certificate/key.