How can I setup a VPN for remote users to connect to a AWS RDS server?
Solution 1
A very simple solution would be to just use SSH tunnels to carry the SQL traffic. You don't mention what OS you're running on your EC2 instances, so I'll assume you're running Linux (if you're not running Linux, just spin up a t1.micro instance for this purpose. That will provide plenty of horsepower for this type of traffic). So - with Linux server in hand, getting this set up will be quite easy. Each developer will need an account on that server, and they'll need to generate a keypair for themselves and provide you the public key to deploy on their server accounts.
If they were using a unixy OS, they'd run a command similar to this:
$ ssh user@ec2-host -L3306:a.b.c.d:3306
...where "a.b.c.d" is the IP address of the RDS instance. You'll just need to make sure that each user has appropriate grants on the RDS database to connect from the ec2 host they're ssh'ing through.
After doing this, the developers will connect to their localhost, port 3306, and that traffic will be tunneled through to the RDS instance.
(I've never actually used RDS, but being that it's built to be a drop-in MySQL replacement, I feel my assumption is correct that is uses port 3306. If it uses a different port, then change the port number on the end of the above command)
Solution 2
Yeah, you're not going to be able to do this without a bit of mucking around. The easiest solution would be to NAT the VPN traffic when the gateway sends it to RDS, so that RDS knows to send the traffic back to your gateway before it files off the NAT and sends it back down the VPN. The other way that might work is using a VPC; I've never used it with RDS (or, to be honest, much at all), but as I understand the way that VPC networking works, it's possible that RDS hooks into your VPC and hence might be able to use a gateway. I think, though, that NAT will end up being the easiest option.
Related videos on Youtube
Morgan
Updated on September 18, 2022Comments
-
Morgan over 1 year
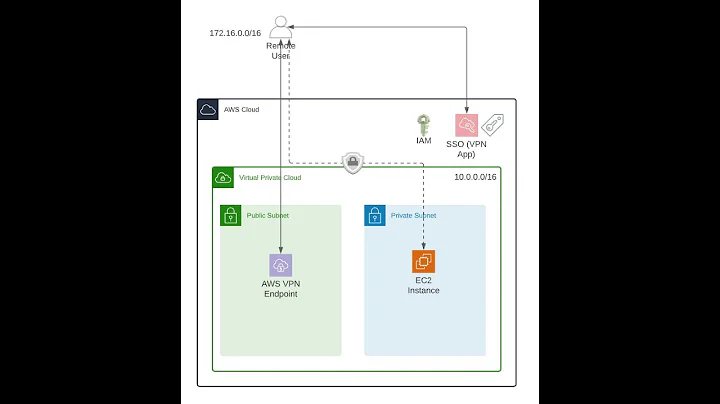
I have remote developers that travel and have constantly changing IP addresses. I would like them to be able to connect to a VPN running on a instance on EC2. Once they are connected to the VPN with a key they then can use the VPN to relay traffic to the RDS server. Constantly changing security group settings every day for each developer is not a option.
I have looked into OpenVPN and can create a VPN connection directly to the instance hosting the VPN. I believe my route is not working because the RDS does not know how to route replies back to the RDS instance.
- Is it possible to setup OpenVPN to route like I would like?
- If 1 is not possible what options do I have for creating a secure known connection to RDS from unknown remote sources.
-
Wesley about 12 yearsIn your scenario, does "RDS" stand for Remote Data Services?
-
Morgan about 12 yearsIn this scenario RDS stands for Relational Database Service. A RDS instance is a special EC2 instance that is dedicated to running a database like MySQL. You cannot ssh into or configure the OS on these types.
-
ceejayoz about 12 yearsHave you looked into VPC?
-
Chris Johnson almost 12 yearsGood answer, ssh tunneling is handy. Note the a.b.c.d part of the ssh command line is an address from the remote host's perspective. You might get some performance or security benefit from using an internal address, e.g. localhost or an internal-only IP address. Erik did say "IP address" but if you are a first-time user of SSH -L you may not realize this doesn't have to be an external IP address!