Software VPN connection to Amazon AWS VPC private instance
Yes it's possible:
you need to do the following:
1- Install openvpn server on the public instance.
Configure the openvpn server to send routes or ip range of your private instance.
in the config file add:
Assuming the private range is 192.168.1.0/24
push "route 192.168.1.0 255.255.255.0"
Allow traffic from the VPN traffic to the Private instance, using iptables.
2- Create one or move vpn clients and enjoy your direct connection.
If you need any details of the above i'll be glad to help.
Related videos on Youtube
tilmik
Updated on September 18, 2022Comments
-
tilmik over 1 year
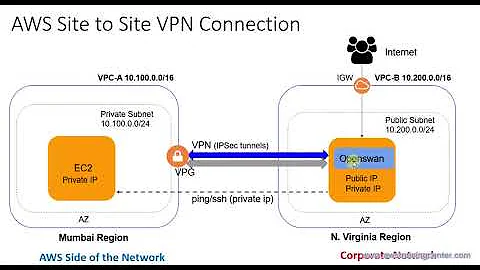
I have a Virtual Private Cloud (VPC) instance on Amazon AWS. Inside the VPC, I have a private instance which is running the database and a public instance which has the front-end web pages for accessing the database.
There is no way to login into the private instance directly from outside as it does not have any public ip. However, I can login into it from the public instance using its private ip.
I want to create a VPN gateway inside my VPC which will allow me to directly connect to the private instance from outside using software VPNs like OpenVPN or OpenSwan.
My questions are -
- Is this possible at all?
- If yes, what are the steps to setup this mechanism?
Thanks in advance.
-
 Admin about 9 yearsThis is a problem that is being faced every day by developers working on AWS projects. Amazon's literature is not as bad as the 'bad old days' of Oracle, but only slightly. I.E., they are minimal and opaque to newcomers to the VPC, networking, DNS, etc issues that a 'virtual data center' like AWS VPC. So to block a question by saying, "You don't know enough to ask the question right" blocks a lot of beginner dev ops people who are a large part of the target audience of this website and Amazon/Rackspace/et al. VPNs are difficult to work with, especially as a client and not network to network.
Admin about 9 yearsThis is a problem that is being faced every day by developers working on AWS projects. Amazon's literature is not as bad as the 'bad old days' of Oracle, but only slightly. I.E., they are minimal and opaque to newcomers to the VPC, networking, DNS, etc issues that a 'virtual data center' like AWS VPC. So to block a question by saying, "You don't know enough to ask the question right" blocks a lot of beginner dev ops people who are a large part of the target audience of this website and Amazon/Rackspace/et al. VPNs are difficult to work with, especially as a client and not network to network. -
 Admin over 8 yearsThis question should be re-opened. There's no good documentation about doing this with openswan and openvpn is not viable for long-term use when using 2fa.
Admin over 8 yearsThis question should be re-opened. There's no good documentation about doing this with openswan and openvpn is not viable for long-term use when using 2fa. -
 Admin over 8 years+1 for re-opening question...
Admin over 8 years+1 for re-opening question...
-
tilmik over 10 yearsThanks for the reply. I have setup a IPSEC / L2TP gateway on one of the public EC2 instance but I am struggling with the VPN client part. Can you suggest a VPN client which can use IPSEC / L2TP / PPP? If this doesn't work, I am going to try your suggestion with OpenVPN.
-
tilmik over 10 yearsActually, from the default ipsec-l2tp vpn client I am getting the following error - "Error 230: No default gateway found or failed to write default gateway information". What could be the problem?
-
slayedbylucifer almost 10 years@MohyedeenN, I am going through similar thoughts. I have a question. Apart from what you have suggested above, Do I have to configure VPC security groups rules to allow traffic from VPN Server (in pub subnet) to other resources (In Private subnet). And, also security group rules in Private subnet to accept traffic from VPN server in Pub subnet ? It sound logical to me though. Thanks. and +1.
-
MohyedeenN almost 10 years@slayedbylucifer, For sure you need to allow the needed ports, in the security groups, also using iptables if you are applying any rules in conjunction with security groups, you are right it's completely logical :)
-
 jorfus over 8 yearsYou also need to: disable source destination checking (EC2 setting) and add a route to the route table on your VPC public subnet. I did this with openvpn relatively easily, openswan is a bit more involved. docs.openvpn.net/how-to-tutorialsguides/virtual-platforms/…
jorfus over 8 yearsYou also need to: disable source destination checking (EC2 setting) and add a route to the route table on your VPC public subnet. I did this with openvpn relatively easily, openswan is a bit more involved. docs.openvpn.net/how-to-tutorialsguides/virtual-platforms/…