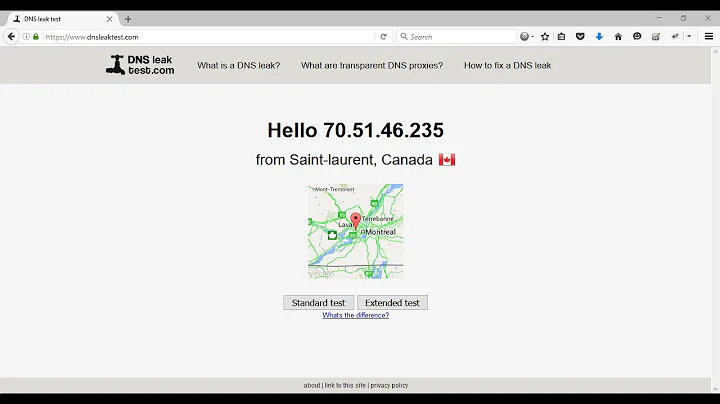
How can you test for a DNS leak for an OpenVPN provider?
OpenVPN won't assign server's DNS resolver(s) if you run it from terminal. This is a known behavior and until OpenVPN developers fix it, you have to run an external script to assign the DNS resolvers once the tunnel is connected, and revert when disconnected. This should work on Ubuntu, Debian, and any Debian based distros.
Step 1
First, you have to update the
.ovpnprofiles to run a script that will assign a DNS resolver and restore your original resolver when the VPN connection will shut-down. Add the following lines to the.ovpnfile:script-security 2 up updatedns.sh down updatedns.shNote that this applies if you run openvpn [server profile.ovpn] from the current folder, not eg.
openvpn /home/myself/Downloads/openvpn-profiles/server-location.ovpnIf you run from different folder, you will have to include the full path accordingly (also to the mass-update command below)
To mass-update all
.ovpnprofiles in a folder, unzip the server profiles, then from the same folder run:for filename in *.ovpn; do echo -e "script-security 2\nup updatedns.sh\ndown updatedns.sh" >> $filename; doneStep 2
Get the updatedns.sh script:
wget https://vpn.ac/configs/misc/updatedns.shRun
chmod +x updatedns.sh to make it executableStep 3Connect by running:
openvpn ./[location-profile].ovpnOnce connected, check dnsleak test. It should report our DNS resolvers.
When you disconnect, the original
resolv.confwill be restored. If anything goes wrong it it doesn't restore properly (ie. openvpn process killed), restore it manually by running:cp -a /etc/resolv.conf.orig /etc/resolv.conf
Source:VPN.AC
Related videos on Youtube
Wayne Len
Updated on September 18, 2022Comments
-
Wayne Len over 1 year
I'm currently using VPNBook with OpenVPN. I just recently learned about DNS leaking. Is there a way to scan for it?