How could a hacker access the /etc/shadow file if it is only accessible by root and they do not have root access?
In order to understand how a hacker could access this file you have to think like a hacker, mainly outside the box, of what most would consider to be "normal" methods for accessing a file.
To that end, someone could gain access to a daemon which may have root privileges, and then induce this daemon to read the contents of the /etc/shadow file. I've seen many examples throughout my career where developers or unknowledgeable sysadmins have run applications such as Tomcat or Apache as root.
These same methods can be used to augment the permissions on files as well, though a good hacker would not do something so obvious as to be detected, safer to read the contents of these files and stash them somewhere else or retrieve them from the box.
As to the type of file which /etc/shadow is, it's clearly marked as a text file on my CentOS 7.x system.
$ file /etc/shadow
/etc/shadow: regular file, no read permission
$ sudo file /etc/shadow
/etc/shadow: ASCII text
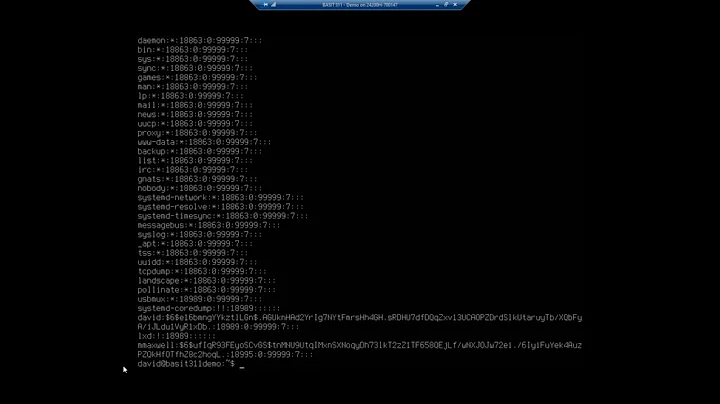
Its permissions are as follows:
$ ll /etc/shadow
----------. 1 root root 1150 Oct 29 11:44 /etc/shadow
And hashed passwords are clearly visible per user:
$ sudo grep vagrant /etc/shadow
vagrant:$1$sPqOnE53$gIcd5Q0xjmV9bM406mHpf/::0:99999:7:::
-or-
$ sudo getent shadow | grep vagrant
vagrant:$1$sPqOnE53$gIcd5Q0xjmV9bM406mHpf/::0:99999:7:::
Related videos on Youtube
Andy Meza III
I am a 32 year old student, aspiring developer and cyber security professional. Perhaps this is taking on too many tasks! I hail from Chicago, Illinois but being born in Houston I still root for the Rockets!
Updated on September 18, 2022Comments
-
Andy Meza III almost 2 years
I am reading a book on ethical hacking, and it has some examples in Python which I won't post here unless asked since this isn't Stack Overflow. But, I was wondering, if a hacker was trying to access passwords in /etc/shadow, how do they do that without root access? They can't copy it, open it; etc. Is there some brute force method?
And my /etc/shadow file is not a text file, it is a shadow file. I don't know anything about these, where can I learn?
-
Andy Meza III over 5 yearsp.s. i read about /etc/shadow in tldp but it isn't much use in figuring out how to "work" with these files except from an administrative point of view.
-
-
Andy Meza III over 5 yearswell I have /etc/passwd which is a text file, and it has the usual info as per tldp and then there is /etc/shadow which i cannot view with a text editor, it says cannot open and when i changed name to .txt it said the same thing. it has an icon like a terminal with a question mark on it, but i'm running parrot os not your run of the mill linux os. not that i think this should differ.
-
Andy Meza III over 5 yearsi'm sorry, the icon is like a terminal or window with an arrow in it, kind of like you'd see on a video file