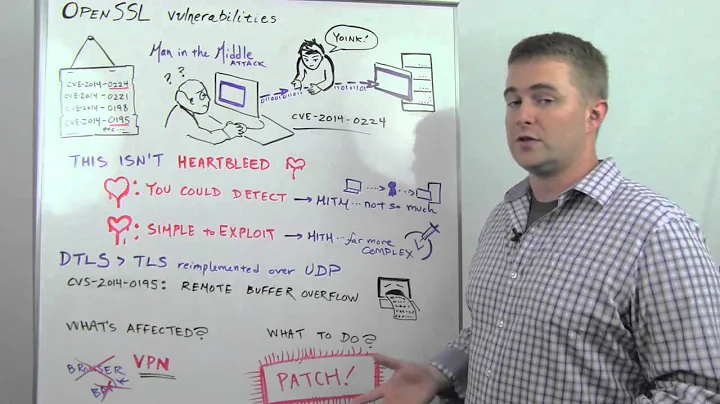
How to patch the Vulnerability [CVE-2014-0224] in OpenSSL?
Solution 1
The answer given does not answer the question, and as far as the latest package for x86_64 14.04 the latest openssl package info is (if others have dif please let me know):
openssl:
Installed: 1.0.1f-1ubuntu2.3
Candidate: 1.0.1f-1ubuntu2.3
Version table:
*** 1.0.1f-1ubuntu2.3 0
500 mirror://mirrors.ubuntu.com/mirrors.txt/ trusty-updates/main amd64 Packages
500 mirror://mirrors.ubuntu.com/mirrors.txt/ trusty-security/main amd64 Packages
500 http://us.archive.ubuntu.com/ubuntu/ trusty-updates/main amd64 Packages
500 http://security.ubuntu.com/ubuntu/ trusty-security/main amd64 Packages
100 /var/lib/dpkg/status
1.0.1f-1ubuntu2 0
500 mirror://mirrors.ubuntu.com/mirrors.txt/ trusty/main amd64 Packages
500 http://us.archive.ubuntu.com/ubuntu/ trusty/main amd64 Packages
I have been messing around with installing/upgrading that to version 1.0.1h from HERE with no luck yet, when I make some headway I will check back in.
*****UPDATE: So I found the solution on another thread that just needed to be updated (source post listed below):**
Below the single command line to compiling and install the last openssl version.
curl https://www.openssl.org/source/openssl-1.0.1h.tar.gz | tar xz && cd openssl-1.0.1h && sudo ./config && sudo make && sudo make install
Replace old openssl binary file by the new one via a symlink. Go to /usr/bin in terminal and run command below
sudo ln -sf /usr/local/ssl/bin/openssl `which openssl`
Reboot and you are good to go. You may want/need to create new certificates. Here is the original thread/post I updated. SOURCE
My output after running commands and rebooting:
OpenSSL 1.0.1h 5 Jun 2014
built on: Sat Jun 14 22:43:13 EDT 2014
platform: linux-x86_64
options: bn(64,64) rc4(16x,int) des(idx,cisc,16,int) idea(int) blowfish(idx)
compiler: gcc -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -Wa,--noexecstack -m64 -DL_ENDIAN -DTERMIO -O3 -Wall -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DWHIRLPOOL_ASM -DGHASH_ASM
OPENSSLDIR: "/usr/lib/ssl"
Solution 2
-
Make sure you have a currently supported release: 10.04-server, 12.04, 14.04 or 13.10.
~$ lsb_release -a No LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 12.04.4 LTS Release: 12.04 Codename: precise Make sure you install the latest updates.
sudo apt-get update && sudo apt-get upgrade-
Verify.
apt-cache policy opensslshould show as installed version1.0.1-4ubuntu5.14.apt-cache policy openssl openssl: Installed: 1.0.1-4ubuntu5.14 Candidate: 1.0.1-4ubuntu5.14 Version table: *** 1.0.1-4ubuntu5.14 0 500 http://archive.ubuntu.com/ubuntu/ precise/main i386 Packages 500 http://archive.ubuntu.com/ubuntu/ precise-security/main i386 Packages 500 http://archive.ubuntu.com/ubuntu/ precise-updates/main i386 Packages 100 /var/lib/dpkg/status Restart any services or the system just to be sure.
Related videos on Youtube
Shadin
Updated on September 18, 2022Comments
-
Shadin over 1 year
I've received a warning from the authority that generated my certificate, it says that there is bug in OpenSSL and it has been found affecting versions 1.0.1.
As I understand, I have to upgrade to 1.0.1h to fix this bug.
This is the first time I deal with these stuff and I'm worried about how it will affect my server.
Do I have to restart any services? And what exactly? I have to make sure this is not going to take too long.
-
VenkiPhy6 almost 10 years@cshubhamrao This is not the heartbleed bug. This is a different one. So not a dupe.
-
cshubhamrao almost 10 yearsReally sorry, my bad.
-
theTuxRacer almost 10 yearsJust as an FYI, you will not need to change/renew your certificate.
-
-
trysis almost 10 years
apt-get updateandapt-get upgradeare the same command by default on many (most?) systems. The user has to specifically make them not the same by changing a setting somewhere. -
 Admin almost 10 years@trysis
Admin almost 10 years@trysisupdateupdates the package sources,upgradeupdates actual packages, so they aren't the same and both are needed (unless that was changed). -
Shadin almost 10 yearsam gonna install the update from here openssl.org/source [ openssl-1.0.1h.tar.gz] is it the same version [1.0.1-4ubuntu5.14] ?
-
mikewhatever almost 10 yearsNot sure why you'd do that. I'd recommend installing updates from the Ubuntu repositories only if possible. The version is not the same, as the numbering tells.
-
Shadin almost 10 yearsi found this earlier digicert.com/openssl-ccs-injection-fix.htm you see the patches list at the Remediation/Fix section. what do you think of this?
-
dobey almost 10 yearsThis doesn't properly answer how to update in Ubuntu to get the fix; which is to simply install the updates from the security updates channel. Also, the bug affects both clients and servers, and is only exploitable by some path between both endpoints, when both endpoints are vulnerable.
-
dobey almost 10 years@Shadin that clearly says "update from your vendor." In this case, the "vendor" is Ubuntu, and those updates are available, and should be installed.
-
saiarcot895 almost 10 yearsThat's because Ubuntu doesn't publish completely new versions of software in released distros; they take the patches that address the security/functionality issues and apply them to the existing version, hence the
.3at the end of the version string. -
saiarcot895 almost 10 years10.04 is also supported for this package, I think.
-
mikewhatever almost 10 years@saiarcot895 Thanks, you are quite right. Corrected above.
-
J Bourne over 9 yearsJohn..You are the man...! Super like for this answer
![Ubuntu: How to patch the Vulnerability [CVE-2014-0224] in OpenSSL? (2 Solutions!!)](https://i.ytimg.com/vi/MhEjTbvqDa8/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLAWhRp3HVnuaFbDPMDc5iIhdnHMvQ)