iptables reject-with icmp-host-prohibited
iptables rules are evaluated top-down. If a packet matches one of the rules, it does what the ACTION of the rule defines. Usually that is REJECT, ACCEPT, DROP, REDIRECT (to a different port) or jump to a CHAIN.
The last rule is just a generic rule that triggers when no previous rule has triggered. Basically it's a "by default, reject anything that doesn't match a previous rule". That is standard and a good practice when implementing firewalls.
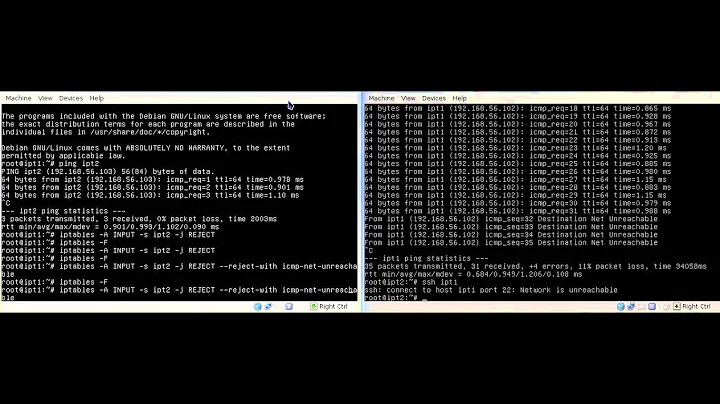
The icmp-host-prohibited is just the reject message with whom the packet gets rejected. That means that your server will notify the sender that the packet was rejected with that message.
Note that for a better hardening, it's recommended to DROP messages instead of REJECT them, because the latter may give an attacker some info like for example "this host exists and has rejected your packet", whereas DROP won't provide such information.
Related videos on Youtube
Salem F
Updated on September 18, 2022Comments
-
 Salem F over 1 year
Salem F over 1 yearI recently bough new KVM/VPS once I install OpenResty(nginx fork) and run it , my server were not accepting incoming connection on the test port
8080I manage to solve the issue by adding port 8080 to allowed rules ,iptables -I INPUT -p tcp --dport 8080 -m conntrack --ctstate NEW,ESTABLISHED -j ACCEPT iptables -I OUTPUT -p tcp --sport 8080 -m conntrack --ctstate ESTABLISHED -j ACCEPTbut I still can't understand the default rules that comes with my VPS
pkts bytes target prot opt in out source destination 361K 1192M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 1 60 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 464K 70M INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 464K 70M INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 464K 70M INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 1324 61332 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 458K 70M REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedspecially the last line is it blocks all incoming traffic !
-
 Salem F about 5 yearsGreat explain , I miss rules order part , +I agree with you about use DROP instead of REJECT specially to block some small attacks ,iptables is great tools but it commands very primitives need some times to tweak it well .Last do you know simple way to receive connection message with command line tools of via some language like (C/PHP)
Salem F about 5 yearsGreat explain , I miss rules order part , +I agree with you about use DROP instead of REJECT specially to block some small attacks ,iptables is great tools but it commands very primitives need some times to tweak it well .Last do you know simple way to receive connection message with command line tools of via some language like (C/PHP) -
nKn about 5 yearsDo you mean capture packets on the machine? If so, you can use a tool like
tcpdumporngrep. -
 Salem F about 5 yearsI mean the reply message form the other machine , e.g if I use curl won't show me that message , I don't know
Salem F about 5 yearsI mean the reply message form the other machine , e.g if I use curl won't show me that message , I don't knowtcpdump.