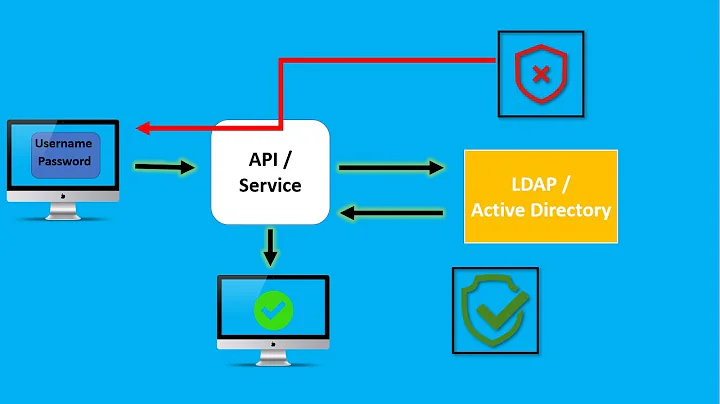
LDAP Auth proxy adding headers according to LDAP groups
Solution 1
Would require-group instead of require-user help?
Also see this question about nested group enumeration.
Require ldap-filter memberof:1.2.840.113556.1.4.1941:=CN=Access to Apache,OU=My Organization Unit,DC=company,DC=com
Solution 2
Since you are using LDAP, you can avoid mod_rewrite. Though setting:
AuthLDAPRemoteUserAttribute sAMAccountName
had no effect for me with Apache-2.4 -- contrary to the documentation -- what did work, was %{AUTHENTICATE_sAMAccountName}e. For example:
RequestHeader set X-App2-Remote-User %{AUTHENTICATE_sAMAccountName}e
Note, that the AuthLDAPURL needs to contain ?sAMAccountName at the end for AUTHENTICATE_sAMAccountName to be created in the environment by mod_ldap. You already have it in your example.
Related videos on Youtube
Jean-Rémy Revy
Professional profile : https://fr.linkedin.com/in/jeanremyrevy http://fr.viadeo.com/fr/profile/revy.jean-remy IT Consultant & Architect for Ippon Technologies As an architect I deal with API, microservices, scalables architectures & teams. My main skills: API & Microservices : RESTful API, Domain Driven Design DevOps (continuous integration, deployement, Testing, Agility) Java development Web development Accessibility (visual impaired, ...) Scalables architectures (LoadBalancing, High Availability)
Updated on September 18, 2022Comments
-
Jean-Rémy Revy over 1 year
I'm trying to setup some WebSSO mechanisms, that allow my customer to authenticate people against internal Active Directory and then add secure (https) headers containing credential information.
Version 1 OK : authenticate and adding headers
The first version is "quite" simple. I'm using Apache and mod_auth_kerb to autenticate, and then I add headers. The following configuration is a kinsnippet of existing one.
<VirtualHost *:80> ServerName external-sso.corp.fr RewriteEngine On </VirtualHost> <location /app2> # Authentication AuthType Kerberos AuthName "Active Directory Authentication" KrbMethodNegotiate On KrbMethodK5Passwd On KrbLocalUserMapping On KrbAuthRealms CORP.REALM.FR Krb5KeyTab /etc/krb5/http-myserver.corp.realm.fr.keytab Require valid-user # Identification AuthLDAPURL "ldaps://corp.realm.fr:636/DC=realm,DC=corp,DC=fr?sAMAccountName?sub?(objectClass=*)" AuthLDAPBindDN "CN=App2,OU=cloud,OU=prod,OU=Authentication,DC=realm,DC=corp,DC=fr" AuthLDAPBindPassword "*******" AuthLDAPGroupAttributeIsDN on Require valid-user # Adding Information into headers RewriteCond %{REMOTE_USER} (.+) RewriteRule .* - [E=RU:%{REMOTE_USER}] RequestHeader set X-App2-Remote-User %{RU}e </location>Version 2 no idea ! : authenticate and adding headers according to groups
Into the next version, I would like to add specific headers ONLY if the user belongs to a group, e.g. user account name if he is allowed to access to APP2, generic account if not.
I don't know how to achieve that, even creating two different vhosts ..., even if it's possible.
Could you please give me some hints ? Don't hesitate to add advises, even I know that :
- Active Directoy already have web-sso mechanisms with AD/AM
- Adding headers is not really secured (no matter here, using HTTPS and IP filtering)
- I really need a full web-sso (we are actually comparing Shibboleth, AD/AM and other solutions but don't have time to wait :) ... you know, business is business !
-
Jean-Rémy Revy over 10 yearsThose links are interesting, because they provide me a way to apply many filters. But this don't help to realize different actions according to the groups users belong to. Thanks anyway.
-
Jean-Rémy Revy over 7 yearsSince I no longer work for this company, I won't be able anymore to test your solution, but tanks anyway :)