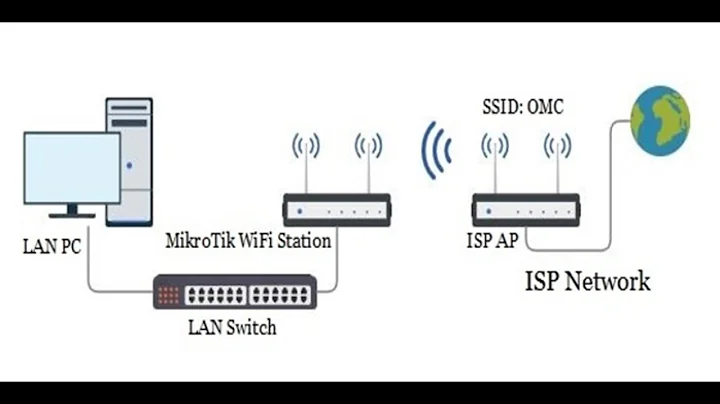
MikroTik Configuration - Add a Public Wireless Router (internet only) to Office LAN
Solved this by following the instructions in this article and finding the equivalent commands in the RouterOS webgui.
Summary of steps:
-
Create Guest Bridge
/interface bridge add name=bridge-guest -
Create DHCP-server on bridge
/ip address add address=172.16.0.1/24 interface=bridge-guest network=172.16.0.0 /ip pool add name=guest ranges=172.16.0.100-172.16.0.254 /ip dhcp-server add address-pool=guest disabled=no interface=bridge-guest name=guest /ip dhcp-server network add address=172.16.0.0/24 dns-server=172.16.0.1 gateway=172.16.0.1 -
Make a NAT rule to route traffic out to internet (I didn't need to do this as the default masquerade rule already did this. The src-address netmask is incorrect in the original article.)
/ip firewall nat add action=masquerade chain=srcnat out-interface=ether1-gateway src-address=172.16.0.0/24 -
Filter all traffic coming from bridge to anywhere except the gateway
/ip firewall filter add action=drop chain=forward in-interface=bridge-guest out-interface=!ether1-gateway -
Block traffic coming from guest-bridge to gateway on port 80 to keep guest users from accessing MikroTik console
/ip firewall filter add action=drop chain=input in-interface=bridge-guest dst-address=192.168.1.1 dst-port=80
Note that in step 5 the dst-address should be the address of the MikroTik router and the protocol may need to be set to 6(tcp)
Result
I now have a port on my MikroTik router that only allows internet access and blocks attempts to connect to the admin panel. Attached to this is the Netgear wireless router with standard settings. The benefit of this approach is that the security of the LAN does not rely on the security of the wireless router at all.
Related videos on Youtube
Jack
Updated on September 18, 2022Comments
-
Jack almost 2 years
Goal
Provide internet access for employees' personal devices without providing access to the internal network.
Equipment
- Netgear WNDR4500v2: Wireless router intended for the guest network (has wireless isolation feature)
- MikroTik RB2011Ui AS-RM: The primary router for this network. Attached to it are a few switches that comprise the wired internal lan. Upstream of this a Juniper fiber device that I have no administrative access to.
Connections
Juniper -> MikroTik -> Cisco Switches -> Clients, Printers, Etc
The Netgear is currently connected to a port of the MikroTik that is a slaveport to the same masterport used by the Cisco Switches. Changing this might be part of the solution, but I'm not sure.
Where I'm at
I configured the Netgear to use wireless isolation and set its internal ip range to match the office network then connected it to the MikroTik router. My intent was to have requests for office resources fail to escape the Netgear's range (e.g. a request for 192.168.1.1 would return the netgear admin panel rather than the mikrotik) but it did some autoconfiguration when I connected it and switched to a different range, so now I can access the MikroTik and ping office devices. Not what I'm looking for.
This seemed like the hack way to do it anyway, considering the MikroTik is probably capable of something more elegant. What is the correct way to isolate my wireless router with this equipment?
-
Diamond over 8 yearsHave you configured the Wireless device in router mode? You can configure it manually from the admin panel and assign a custom lan address range. If you have access to the MikroTik, then you can configure the firewall there to block certain network and many things.
-
Jack over 8 yearsI think configuring MikroTik is a better focus for my question. I currently have a single bridge connecting a gateway port on the MikroTik to a cisco switch. The Netgear router is attached to another port but I'm unsure how to connect that to the bridge without disrupting or accessing the LAN. I haven't been able to find the relevant instructions in the MikroTik wiki. Any help on this would be appreciated.
-
MrGigu over 8 yearsIf you wanted to take this a step further and have some users that do have access to internal resources, and your WiFi access point supports it (I haven't researched that device), you can create a 2nd SSID using, say WPA2-Enterprise, and pop it on the internal VLAN, or put it onto another different VLAN and allow some firewall rules so that it can access the internal network if you wanted to.

![Configure MikroTik Router to access internet [part4]](https://i.ytimg.com/vi/aTskFdLvIZc/hq720.jpg?sqp=-oaymwEcCNAFEJQDSFXyq4qpAw4IARUAAIhCGAFwAcABBg==&rs=AOn4CLAMiVL4DwjkWW0YWA4bdYsCSkTo9Q)