Windows 7 appears to select inconsistent anchor during wireless connection
I had exactly this problem and solved it by downloading the DigiCert SSL Certificate Checker and running it on my IAS servers. The tool stated that one of the intermediary certificates, was incorrect and offered to install a new one. Looking at the certificate store, the tool installed a new DigiCert High Assurance CA-3, even though an apparently valid certificate was present. I checked the new certificate against the one it replaced, both had the same version number and expiry date, just a different serial number. Not sure what was wrong with the previous but it all worked with the new one.
Related videos on Youtube
Neobyte
Updated on September 17, 2022Comments
-
Neobyte over 1 year
We have a wireless authentication server (Windows 2003 SP2 with IAS). It is configured with a DigiCert certificate. The certificate chain looks like this:
Entrust.net Secure Server Certification Authority DigiCert High Assurance EV Root CA DigiCert High Assurance CA-3 ourserver.ourdomain.comWhen a Windows 7 client connects to the wireless for the first time, they get a warning about the certificate. It will look like this:
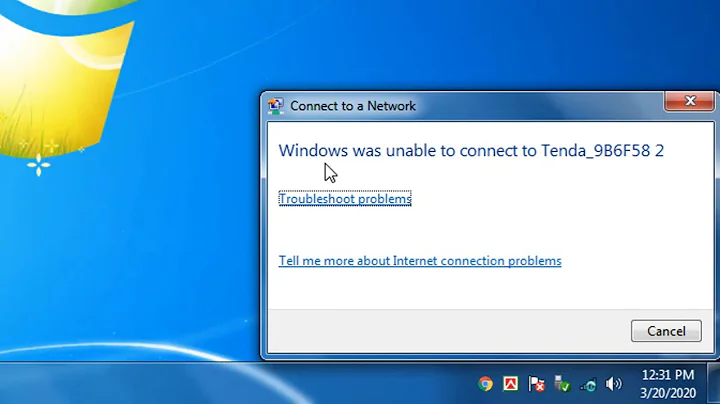
The server "ourserver.ourdomain.com" presented a valid certificate issued by "Entrust.net Secure Server Certification Authority", but "Entrust.net Secure Server Certification Authority" is not configured as a valid trust anchor for this profile.
That is not a big deal as it's supposed to be a one-off. But the root certificate it complains about is inconsistent. Half the time, they get this instead:
The server "ourserver.ourdomain.com" presented a valid certificate issued by "DigiCert High Assurance EV Root CA", but "DigiCert High Assurance EV Root CA" is not configured as a valid trust anchor for this profile.
The reason this is an issue is that it means the client is prompted a second time at some later point when they reconnect to the wireless network, where the connection seems to arbitrarily choose the "other" certificate in the chain as the missing anchor, rather than the first. The selection appears to be random.
To be clear, this has been reproduced where:
- 2 Windows 7 laptops are in the same physical location (on same AP).
- One, when initially configured, prompted with the Entrust root cert.
- The other, when initially configured, prompted with the EV root cert.
- Both were connecting to the same IAS server, which only has one certificate installed.
Any ideas as to the cause of this inconsistency, and how I can stop it?
-
 Admin about 13 yearsIf you haven't done so already, I'd recommend going into the Windows Application and Services Logs and turning on the CAPI2 (certificate api log) and WLAN-AutoConfig. They're under Event Viewer->Application and Services Logs->Microsoft->Windows. Find the operational log and click "Enable Log". It will give you more detail. Also, are your IAS servers load balanced?
Admin about 13 yearsIf you haven't done so already, I'd recommend going into the Windows Application and Services Logs and turning on the CAPI2 (certificate api log) and WLAN-AutoConfig. They're under Event Viewer->Application and Services Logs->Microsoft->Windows. Find the operational log and click "Enable Log". It will give you more detail. Also, are your IAS servers load balanced? -
 Admin about 13 yearsUnfortunately it appears CAPI2 logging is only available in Windows 2008 and up - our IAS servers are 2003. Yes our IAS servers are load balanced.
Admin about 13 yearsUnfortunately it appears CAPI2 logging is only available in Windows 2008 and up - our IAS servers are 2003. Yes our IAS servers are load balanced. -
 Admin about 13 yearsThese logs can be enabled on the clients too, it might help you find if there was something odd with the certificate negotiations between the client and the server. (e.g. a wonky subject alternative name or something)
Admin about 13 yearsThese logs can be enabled on the clients too, it might help you find if there was something odd with the certificate negotiations between the client and the server. (e.g. a wonky subject alternative name or something)
-
Neobyte about 13 yearsNone of this answers my question, which is "why am I being prompted with inconsistent trust anchors".
-
Neobyte about 12 yearsThat awkward moment when your work colleague from two metres away answers your question, 11 months later.