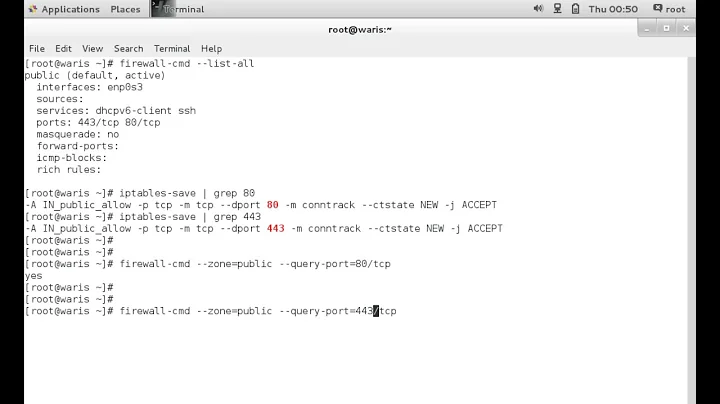
Open ports for public
Let's try something else. Start fresh. Disable firewall and remove all rules without the cruft that UFW adds and leaves behind even when you stop it:
sudo stop ufw
sudo iptables -F
sudo iptables -X
sudo iptables -t nat -F
sudo iptables -t nat -X
sudo iptables -P INPUT ACCEPT
sudo iptables -P OUTPUT ACCEPT
Is your application currently listening on this machine? Check with the command below and post output:
sudo netstat -tupln | grep 5280
Log into the machine running the service on port 5280. Launch tcpdump there to capture connections to/from port 5280:
export ext_if=$(ip ro | awk '/^default via/ {print $5}')
sudo tcpdump -i ${ext_if} port 5280
Tcpdump should be running now. Log into another machine on the same subnet and try:
wget -S- -O/dev/null 'http://192.168.1.109:5280'
Does the command return anything? Can you see packets being logged by tcpdump running on the same machine running the service on port 5280?
Related videos on Youtube
ThatsJustCheesy
Updated on September 18, 2022Comments
-
ThatsJustCheesy almost 2 years
I am quite new to Ubuntu or any Linux family OS. I am trying to run a server on my laptop (for development reasons, however I have tried this on azure Ubuntu VM too). The server runs on
5222port and the admin panel is on5280port. The server isejabberdif you need to know it's name.The server is working fine on
localhost. I can open the admin panel inlocalhost:5280/admin. However I want this server to be accessible over internet via public ip. I have tried to forward the port on router. The admin panel started working on private ip such ashttp://192.168.1.109:5280/adminon the local machine, but if I try it over the lan, it doesn't work at all. The other machine doesn't get connected to the server even if they are on the same lan. I have no luck in public ip too.I am not sure but it may be a firewall issue, however I have no idea how to check or even know if it's been blocked. I have tried nmap and this is the output of localhost and private ip on local machine -
5222/tcp open xmpp-client 5269/tcp open xmpp-server 5280/tcp open xmpp-boshBut on public ip I get
Host is up (0.0045s latency). Not shown: 997 filtered ports PORT STATE SERVICE 21/tcp open ftp 23/tcp open telnet 80/tcp open httpAny idea how can I solve the issue or what might be the exact problem here?
Update: I have tried this official guide regarding firewall to allow 5280,5222 and 5269 port. The status shows them in the allow list for anyone, but still it doesn't work. This the status output.
$ sudo ufw status Status: active To Action From -- ------ ---- 5280 ALLOW Anywhere 5222 ALLOW Anywhere 5269 ALLOW Anywhere 5280 (v6) ALLOW Anywhere (v6) 5222 (v6) ALLOW Anywhere (v6) 5269 (v6) ALLOW Anywhere (v6)The iptables output -
sudo iptables -S -P INPUT DROP -P FORWARD DROP -P OUTPUT ACCEPT -N ufw-after-forward -N ufw-after-input -N ufw-after-logging-forward -N ufw-after-logging-input -N ufw-after-logging-output -N ufw-after-output -N ufw-before-forward -N ufw-before-input -N ufw-before-logging-forward -N ufw-before-logging-input -N ufw-before-logging-output -N ufw-before-output -N ufw-logging-allow -N ufw-logging-deny -N ufw-not-local -N ufw-reject-forward -N ufw-reject-input -N ufw-reject-output -N ufw-skip-to-policy-forward -N ufw-skip-to-policy-input -N ufw-skip-to-policy-output -N ufw-track-forward -N ufw-track-input -N ufw-track-output -N ufw-user-forward -N ufw-user-input -N ufw-user-limit -N ufw-user-limit-accept -N ufw-user-logging-forward -N ufw-user-logging-input -N ufw-user-logging-output -N ufw-user-output -A INPUT -p tcp -m tcp --dport 5280 -j ACCEPT -A INPUT -j ufw-before-logging-input -A INPUT -j ufw-before-input -A INPUT -j ufw-after-input -A INPUT -j ufw-after-logging-input -A INPUT -j ufw-reject-input -A INPUT -j ufw-track-input -A FORWARD -j ufw-before-logging-forward -A FORWARD -j ufw-before-forward -A FORWARD -j ufw-after-forward -A FORWARD -j ufw-after-logging-forward -A FORWARD -j ufw-reject-forward -A FORWARD -j ufw-track-forward -A OUTPUT -p tcp -m tcp --dport 5280 -j ACCEPT -A OUTPUT -j ufw-before-logging-output -A OUTPUT -j ufw-before-output -A OUTPUT -j ufw-after-output -A OUTPUT -j ufw-after-logging-output -A OUTPUT -j ufw-reject-output -A OUTPUT -j ufw-track-output -A ufw-after-input -p udp -m udp --dport 137 -j ufw-skip-to-policy-input -A ufw-after-input -p udp -m udp --dport 138 -j ufw-skip-to-policy-input -A ufw-after-input -p tcp -m tcp --dport 139 -j ufw-skip-to-policy-input -A ufw-after-input -p tcp -m tcp --dport 445 -j ufw-skip-to-policy-input -A ufw-after-input -p udp -m udp --dport 67 -j ufw-skip-to-policy-input -A ufw-after-input -p udp -m udp --dport 68 -j ufw-skip-to-policy-input -A ufw-after-input -m addrtype --dst-type BROADCAST -j ufw-skip-to-policy-input -A ufw-after-logging-forward -m limit --limit 3/min --limit-burst 10 -j LOG --log-prefix "[UFW BLOCK] " -A ufw-after-logging-input -m limit --limit 3/min --limit-burst 10 -j LOG --log-prefix "[UFW BLOCK] " -A ufw-before-forward -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A ufw-before-forward -p icmp -m icmp --icmp-type 3 -j ACCEPT -A ufw-before-forward -p icmp -m icmp --icmp-type 4 -j ACCEPT -A ufw-before-forward -p icmp -m icmp --icmp-type 11 -j ACCEPT -A ufw-before-forward -p icmp -m icmp --icmp-type 12 -j ACCEPT -A ufw-before-forward -p icmp -m icmp --icmp-type 8 -j ACCEPT -A ufw-before-forward -j ufw-user-forward -A ufw-before-input -i lo -j ACCEPT -A ufw-before-input -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A ufw-before-input -m conntrack --ctstate INVALID -j ufw-logging-deny -A ufw-before-input -m conntrack --ctstate INVALID -j DROP -A ufw-before-input -p icmp -m icmp --icmp-type 3 -j ACCEPT -A ufw-before-input -p icmp -m icmp --icmp-type 4 -j ACCEPT -A ufw-before-input -p icmp -m icmp --icmp-type 11 -j ACCEPT -A ufw-before-input -p icmp -m icmp --icmp-type 12 -j ACCEPT -A ufw-before-input -p icmp -m icmp --icmp-type 8 -j ACCEPT -A ufw-before-input -p udp -m udp --sport 67 --dport 68 -j ACCEPT -A ufw-before-input -j ufw-not-local -A ufw-before-input -d xxx.0.0.xxx/32 -p udp -m udp --dport 5353 -j ACCEPT -A ufw-before-input -d xxx.xxx.xxx.xxx/32 -p udp -m udp --dport 1900 -j ACCEPT -A ufw-before-input -j ufw-user-input -A ufw-before-output -o lo -j ACCEPT -A ufw-before-output -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A ufw-before-output -j ufw-user-output -A ufw-logging-allow -m limit --limit 3/min --limit-burst 10 -j LOG --log-prefix "[UFW ALLOW] " -A ufw-logging-deny -m conntrack --ctstate INVALID -m limit --limit 3/min --limit-burst 10 -j RETURN -A ufw-logging-deny -m limit --limit 3/min --limit-burst 10 -j LOG --log-prefix "[UFW BLOCK] " -A ufw-not-local -m addrtype --dst-type LOCAL -j RETURN -A ufw-not-local -m addrtype --dst-type MULTICAST -j RETURN -A ufw-not-local -m addrtype --dst-type BROADCAST -j RETURN -A ufw-not-local -m limit --limit 3/min --limit-burst 10 -j ufw-logging-deny -A ufw-not-local -j DROP -A ufw-skip-to-policy-forward -j DROP -A ufw-skip-to-policy-input -j DROP -A ufw-skip-to-policy-output -j ACCEPT -A ufw-track-output -p tcp -m conntrack --ctstate NEW -j ACCEPT -A ufw-track-output -p udp -m conntrack --ctstate NEW -j ACCEPT -A ufw-user-input -p tcp -m tcp --dport 5280 -j ACCEPT -A ufw-user-input -p udp -m udp --dport 5280 -j ACCEPT -A ufw-user-input -p tcp -m tcp --dport 5222 -j ACCEPT -A ufw-user-input -p udp -m udp --dport 5222 -j ACCEPT -A ufw-user-input -p tcp -m tcp --dport 5269 -j ACCEPT -A ufw-user-input -p udp -m udp --dport 5269 -j ACCEPT -A ufw-user-limit -m limit --limit 3/min -j LOG --log-prefix "[UFW LIMIT BLOCK] " -A ufw-user-limit -j REJECT --reject-with icmp-port-unreachable -A ufw-user-limit-accept -j ACCEPTThe screenshot from Router port forwarding -

-
 s3lph about 9 yearsDoes it work when you disable ufw?
s3lph about 9 yearsDoes it work when you disable ufw?sudo ufw disable. Don't forget to re-enable it. -
ThatsJustCheesy about 9 years@the_Seppi no, it doesn't work on disabling ufw too.
-
 s3lph about 9 yearsAre the other machines on the same subnet? I.e. does the network part of their IP match the one of your server?
s3lph about 9 yearsAre the other machines on the same subnet? I.e. does the network part of their IP match the one of your server? -
 heavyguidence about 9 yearsare you even able to do ssh to the designated machine over the public ip ? if no check your log file and see what is being blocked. This means the port forwarding on your router is not functioning. Also see if your machine has a static ip. also what is the output of iptables
heavyguidence about 9 yearsare you even able to do ssh to the designated machine over the public ip ? if no check your log file and see what is being blocked. This means the port forwarding on your router is not functioning. Also see if your machine has a static ip. also what is the output of iptables -
ThatsJustCheesy about 9 years@the_Seppi yes they all are on same subnet.
-
 s3lph about 9 years@rulebreaker4 Why should he be able to ssh without a SSH server?
s3lph about 9 years@rulebreaker4 Why should he be able to ssh without a SSH server? -
ThatsJustCheesy about 9 years@rulebreaker4 local machine doesn't have a static ip yet, I am just testing it on development machine, so that I can run it later on Azure server. I have no idea why ssh is related here (ssh port is not opened as far as I know). What command should I run for iptables?
-
 heavyguidence about 9 yearsssh is not really important here however it was to make sure if your server is accessible from outside atleast. Static IP will make sure to the router to forward the traffic to the right device (your server). For iptables you can open the inbound traffic by
heavyguidence about 9 yearsssh is not really important here however it was to make sure if your server is accessible from outside atleast. Static IP will make sure to the router to forward the traffic to the right device (your server). For iptables you can open the inbound traffic bysudo iptables -I INPUT -p tcp --dport 5280 -j ACCEPTcreate a same rule for OUTPUT Table as well. Then save theiptables-saveand restart iptables service. -
ThatsJustCheesy about 9 years@rulebreaker4 I have added the output from the iptables now. It still doesn't work after the addition of the rules.
-
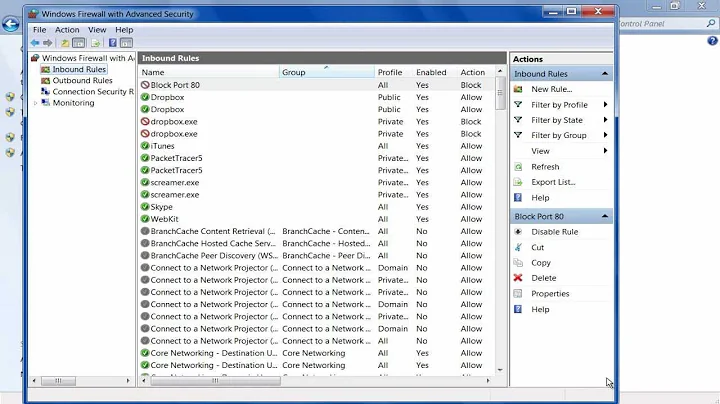
 heavyguidence about 9 yearscan you please, post the ip forwarding screenshot if possible, from your main router. Also just to verify check the routing table for all available pcs if they share the same route. last thing would be try to disable the ufw. Do you have only one router or more than one>
heavyguidence about 9 yearscan you please, post the ip forwarding screenshot if possible, from your main router. Also just to verify check the routing table for all available pcs if they share the same route. last thing would be try to disable the ufw. Do you have only one router or more than one> -
ThatsJustCheesy about 9 years@rulebreaker4 I have added the screenshot from the router's port forwarding screen. All the pcs in the network share the same port forwarding (I just checked). I am currently using a single router.
-