sudo access vs wheel group
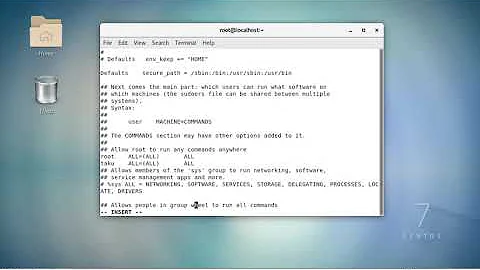
When the wheel group membership gives an user full root access through sudo, it is normally configured like this in the /etc/sudoers file:
%wheel ALL=(ALL) ALL
Meaning: "any members of group wheel on ALL hosts can sudo to ALL user accounts to run ALL commands." So it's exactly the same as your "bad" line:
bob ALL=(ALL) ALL
If you want to give an user (or a group) full access to a specific other user account and nothing else, you can do it this way:
user ALL=(targetuser) ALL
# or
%group ALL=(targetuser) ALL
Then, the user(s) can do
$ sudo -u targetuser command
to quickly execute individual commands as the target user, or
$ sudo -iu targetuser
to get a shell as the target user, with the exact same environment the target user would get when logging in directly.
For historical reasons, some people reflexively use
sudo su - targetuser
for the second purpose. This would require giving the user(s) in question at least access to run the `
su - targetuser
command as root, and it will be more difficult to piece together from the logs what the user actually did. This command was useful back when sudo did not have the -i option, but I think that option has been there for about 15 years by now.
Related videos on Youtube
Mohamed Medhat Sallam
Linux for me is a to enjoy life. Not just a kernel. echo "Thank you Linus trovalds"
Updated on September 18, 2022Comments
-
Mohamed Medhat Sallam over 1 year
I am just a little bit confused here. When you are asked to give a user sudo access to the machine. Should I just add the user to the wheel group.
# usermod -aG wheel bobOr let's say there is no wheel group or it is deleted for some reason.
then how can I grant bob sudo access to the machine.When I did
# which sudoI get the result:
/usr/bin/sudoSo can I do the following line then:
bob ALL=/usr/bin/sudoBut then I changed to user bob after and tried to execute
# sudo iptables -Land then it gives me that error message:
Sorry, user bob is not allowed to execute '/sbin/iptables -L' as root
And so am not sure how to give sudo access to the machine to a user if the group wheel is not there. And according to my knowledge
bob ALL=ALL ALLBasically makes bob have the same power like root which is not good right.
Another question I have is how to make all users on the system able to execute the last command. Do I have to create a group and then add all users to this group or is there another way?
-
 Admin over 6 years
Admin over 6 yearsbob ALL = /sbin/iptables -L. Seeman sudoers. -
 Admin over 6 yearsI know that but I want to give bob sudo access not just iptables -L
Admin over 6 yearsI know that but I want to give bob sudo access not just iptables -L -
 Admin over 6 yearsIf you "want to give bob sudo access", that means that bob will have the "same power like root". What exactly do you want? You want bob to have sudo access, but restrict certain root powers?
Admin over 6 yearsIf you "want to give bob sudo access", that means that bob will have the "same power like root". What exactly do you want? You want bob to have sudo access, but restrict certain root powers? -
 Admin over 5 yearsPlease note this should be
Admin over 5 yearsPlease note this should bebob ALL=(ALL) ALL, you're missing a set of parens in there... Check if your sudoers file has an entry for%wheel, sometimes it's commented out...
-
-
 roaima almost 4 yearsYour
roaima almost 4 yearsYoursudoers line is wrong. Adding/etc/shadowlike that means the user can run/etc/shadowas a program. It's also wrong because ordinary users should not be allowed to read/etc/shadow; you're breaking the authentication security here. -
 J. Doe almost 4 years@roaima angry user, hi there again. I mentioned in parentheses that you don't have to read
J. Doe almost 4 years@roaima angry user, hi there again. I mentioned in parentheses that you don't have to read/etc/shadow. Just drink a glass of water and calm down. Thanks for -1, by the way. Appreciate it. Everything I posted above is correct. Wanna check, go ahead. -
 roaima almost 4 yearsJ.Doe, I'm not angry. I've read your complaint and taken time to recheck carefully whether your
roaima almost 4 yearsJ.Doe, I'm not angry. I've read your complaint and taken time to recheck carefully whether yoursudoersline works as I've warned or as you've described. Here are my findings. As written, your line permits both/bin/catand/etc/shadowto be run (as any user) byuser1. (1) This means no file is secure fromuser1as they can read - and therefore copy - every file on the system (2)/etc/shadowisn't a program so although you've listed it as a possible executable it cannot be run. -
 roaima almost 4 yearsIn order for the command to work as you've described, I think you probably shouldn't have included the comma after
roaima almost 4 yearsIn order for the command to work as you've described, I think you probably shouldn't have included the comma after/bin/cat. But it's still a massive security issue