Why can I not ping my host behind the firewall? Cisco asa 5505
Solution 1
I have found the solution!
Indeed I had to extend my access-list on my outside interface!!!
I have succeeded using ASDM.
First I created a NEW network object for each of my servers. When you create a new object you will be asked for the internal IP address and "this is where the magic happens" you have to set the NAT IP address (the external address) !!!
Secondly I extended my access-list on my outside interface by defining every server and the required service (echo, echo-reply) in the "Public server list". When I performed these 2 steps I was able to ping the server from the internet.
My access-list looks the following now:
access-list OutsideToInside extended permit icmp any4 object SERVER2003 object-group DM_INLINE_ICMP_2 access-list OutsideToInside extended permit icmp any4 object SERVER2002 object-group DM_INLINE_ICMP_1 access-list OutsideToInside extended permit icmp any4 object SERVER2004 object-group DM_INLINE_ICMP_0
object network SERVER2004 nat (inside,outside) static 82.94.xxx.xxx object network SERVER2002 nat (inside,outside) static 82.94.xxx.xxx object network SERVER2003 nat (inside,outside) static 82.94.xxx.xxx
Solution 2
All you configuration looks fine and I can see that you have only allowed desired traffic to your servers using ACL. If you would like to anyone to be able to ping your server on public IP interface, you will need to add below ACL:
access-list OutsideToInside extended permit icmp any any
Or you can choose the servers instead of allowing ping to all/any.
Related videos on Youtube
Banks
Updated on September 18, 2022Comments
-
Banks over 1 year
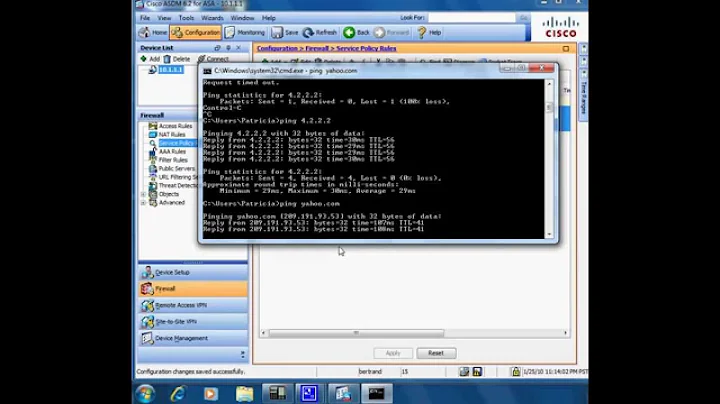
Can anyone please help me to figure out, what in my configuration of the Cisco asa 5505 is wrong or missing? I have multiple host behind my firewall. These hosts run different websites on port 80. I can ping the server from one to another, but I am not able to ping the servers from the Internet. I am using static NAT. Is there a translation issue going on here?
======== CISCOASACLOUD# show run CISCOASACLOUD# show running-config : Saved : ASA Version 9.0(1) ! hostname CISCOASACLOUD enable password ************* encrypted passwd ************* encrypted names ip local pool VPN_IP_POOL 10.0.2.50-10.0.2.75 mask 255.255.255.0 ! interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 ! interface Ethernet0/2 ! interface Ethernet0/3 ! interface Ethernet0/4 ! interface Ethernet0/5 ! interface Ethernet0/6 ! interface Ethernet0/7 ! interface Vlan1 nameif inside security-level 100 ip address 10.0.2.254 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 82.94.XX.XX 255.255.255.0 ! ftp mode passive clock timezone CEST 1 clock summer-time CEDT recurring last Sun Mar 2:00 last Sun Oct 3:00 dns domain-lookup inside dns domain-lookup outside dns server-group DefaultDNS name-server 194.109.104.104 name-server 194.109.9.99 same-security-traffic permit inter-interface same-security-traffic permit intra-interface object network obj_any subnet 0.0.0.0 0.0.0.0 object network VPN_NETWORK subnet 10.0.2.0 255.255.255.0 object network NETWORK_OBJ_10.0.2.0_24 subnet 10.0.2.0 255.255.255.0 object network NETWORK_OBJ_10.0.2.0_25 subnet 10.0.2.0 255.255.255.128 object network SERVER2003_HTTP host 10.0.2.104 object network SERVER2003_HTTPS host 10.0.2.104 object network SERVER2004_HTTP host 10.0.2.105 object network SERVER2004_HTTPS host 10.0.2.105 object network SERVER2002_HTTP host 10.0.2.103 object network SERVER2002_HTTPS host 10.0.2.103 object network SERVER2002_NAGIOS host 10.0.2.103 object network SERVER2003_NAGIOS host 10.0.2.104 object network SERVER2002_NAGIOS_NSCP host 10.0.2.103 object network SERVER2003_NAGIOS_NSCP host 10.0.2.104 object network SERVER2004_NAGIOS host 10.0.2.105 object network SERVER3001_NAGIOS host 10.0.2.202 object network SERVER2001_NAGIOS host 10.0.2.102 object network SERVER3001_HTTP host 10.0.2.202 object network SERVER3001_HTTPS host 10.0.2.202 object network SERVER2004_FTP host 10.0.2.105 object network SERVER2004_FTP_TCP host 10.0.2.105 object network SERVER2004_FTP_SSL host 10.0.2.105 object network SERVER2005_HTTP host 10.0.2.106 object network SERVER2005_HTTPS host 10.0.2.106 object network SERVER3001_ICMP host 10.0.2.201 access-list Default_Tunnel_Group_Name_VPN_splitTunnelAcl standard permit 10.0.2.0 255.255.255.0 access-list OutsideToInside extended permit tcp any host 10.0.2.104 eq www access-list OutsideToInside extended permit tcp any host 10.0.2.104 eq https access-list OutsideToInside extended permit tcp any host 10.0.2.105 eq www access-list OutsideToInside extended permit tcp any host 10.0.2.105 eq https access-list OutsideToInside extended permit tcp any host 10.0.2.103 eq www access-list OutsideToInside extended permit tcp any host 10.0.2.103 eq https access-list OutsideToInside extended permit tcp any host 10.0.2.102 eq 12489 access-list OutsideToInside extended permit tcp any host 10.0.2.103 eq 12489 access-list OutsideToInside extended permit tcp any host 10.0.2.104 eq 12489 access-list OutsideToInside extended permit tcp any host 10.0.2.105 eq 12489 access-list OutsideToInside extended permit tcp any host 10.0.2.202 eq 12489 access-list OutsideToInside extended permit tcp any host 10.0.2.202 eq www access-list OutsideToInside extended permit tcp any host 10.0.2.202 eq https access-list OutsideToInside extended permit tcp any host 10.0.2.105 eq ftp access-list OutsideToInside extended permit tcp any host 10.0.2.105 eq ftp-data access-list OutsideToInside extended permit tcp any host 10.0.2.105 eq 990 access-list OutsideToInside extended permit tcp any host 10.0.2.106 eq www access-list OutsideToInside extended permit tcp any host 10.0.2.106 eq https access-list inside_access_in extended permit ip any any pager lines 24 logging enable logging asdm informational mtu inside 1500 mtu outside 1500 icmp unreachable rate-limit 1 burst-size 1 icmp permit any inside icmp permit any outside no asdm history enable arp timeout 14400 no arp permit-nonconnected nat (inside,outside) source static any any destination static VPN_NETWORK VPN_NETWORK route-lookup nat (inside,outside) source static NETWORK_OBJ_10.0.2.0_24 NETWORK_OBJ_10.0.2.0_24 destination static NETWORK_OBJ_10.0.2.0_25 NETWORK_OBJ_10.0.2.0_25 no-proxy-arp route-lookup ! object network obj_any nat (inside,outside) dynamic interface object network SERVER2003_HTTP nat (inside,outside) static 82.94.XXX.XXX service tcp www www object network SERVER2003_HTTPS nat (inside,outside) static 82.94.XXX.XXX service tcp https https object network SERVER2004_HTTP nat (inside,outside) static 82.94.XXX.XXX service tcp www www object network SERVER2004_HTTPS nat (inside,outside) static 82.94.XXX.XXX service tcp https https object network SERVER2002_HTTP nat (inside,outside) static 82.94.XXX.XXX service tcp www www object network SERVER2002_HTTPS nat (inside,outside) static 82.94.XXX.XXX service tcp https https object network SERVER2002_NAGIOS nat (inside,outside) static 82.94.XXX.XXX service tcp 12489 12489 object network SERVER2003_NAGIOS nat (inside,outside) static 82.94.XXX.XXX service tcp 12489 12489 object network SERVER2004_NAGIOS nat (inside,outside) static 82.94.XXX.XXX service tcp 12489 12489 object network SERVER3001_NAGIOS nat (inside,outside) static 82.94.XXX.XXX service tcp 12489 12489 object network SERVER2001_NAGIOS nat (inside,outside) static 82.94.XXX.XXX service tcp 12489 12489 object network SERVER3001_HTTP nat (inside,outside) static 82.94.XXX.XXX service tcp www www object network SERVER3001_HTTPS nat (inside,outside) static 82.94.XXX.XXX service tcp https https object network SERVER2004_FTP nat (inside,outside) static 82.94.XXX.XXX service tcp ftp ftp object network SERVER2004_FTP_TCP nat (inside,outside) static 82.94.XXX.XXX service tcp ftp-data ftp-data object network SERVER2004_FTP_SSL nat (inside,outside) static 82.94.XXX.XXX service tcp 990 990 object network SERVER2005_HTTP nat (inside,outside) static 82.94.XXX.XXX service tcp www www object network SERVER2005_HTTPS nat (inside,outside) static 82.94.XXX.XXX service tcp https https access-group inside_access_in in interface inside access-group OutsideToInside in interface outside route outside 0.0.0.0 0.0.0.0 82.94.XXX.XXX 1 timeout xlate 3:00:00 timeout pat-xlate 0:00:30 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute timeout tcp-proxy-reassembly 0:01:00 timeout floating-conn 0:00:00 dynamic-access-policy-record DfltAccessPolicy user-identity default-domain LOCAL aaa authentication serial console LOCAL aaa authentication ssh console LOCAL aaa authentication http console LOCAL http server enable http XXX.XXX.XXX.XXX 255.255.255.255 outside http XXX.XXX.XXX.XXX 255.255.255.255 outside http XXX.XXX.XXX.XXX 255.255.255.255 outside http XXX.XXX.XXX.XXX 255.255.255.255 outside http 10.0.2.0 255.255.255.0 inside no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac crypto ipsec security-association pmtu-aging infinite crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5 crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP crypto map outside_map interface outside crypto ca trustpool policy crypto ikev1 enable outside crypto ikev1 policy 10 authentication crack encryption aes-256 hash sha group 2 lifetime 86400 crypto ikev1 policy 20 authentication rsa-sig encryption aes-256 hash sha group 2 lifetime 86400 crypto ikev1 policy 30 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 crypto ikev1 policy 40 authentication crack encryption aes-192 hash sha group 2 lifetime 86400 crypto ikev1 policy 50 authentication rsa-sig encryption aes-192 hash sha group 2 lifetime 86400 crypto ikev1 policy 60 authentication pre-share encryption aes-192 hash sha group 2 lifetime 86400 crypto ikev1 policy 70 authentication crack encryption aes hash sha group 2 lifetime 86400 crypto ikev1 policy 80 authentication rsa-sig encryption aes hash sha group 2 lifetime 86400 crypto ikev1 policy 90 authentication pre-share encryption aes hash sha group 2 lifetime 86400 crypto ikev1 policy 100 authentication crack encryption 3des hash sha group 2 lifetime 86400 crypto ikev1 policy 110 authentication rsa-sig encryption 3des hash sha group 2 lifetime 86400 crypto ikev1 policy 120 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 crypto ikev1 policy 130 authentication crack encryption des hash sha group 2 lifetime 86400 crypto ikev1 policy 140 authentication rsa-sig encryption des hash sha group 2 lifetime 86400 crypto ikev1 policy 150 authentication pre-share encryption des hash sha group 2 lifetime 86400 telnet timeout 5 ssh 10.0.2.0 255.255.255.0 inside ssh XXX.XXX.XXX.XXX 255.255.255.255 outside ssh XXX.XXX.XXX.XXX 255.255.255.255 outside ssh XXX.XXX.XXX.XXX 255.255.255.255 outside ssh XXX.XXX.XXX.XXX 255.255.255.255 outside ssh timeout 60 console timeout 0 management-access inside dhcpd auto_config outside ! threat-detection basic-threat threat-detection statistics access-list no threat-detection statistics tcp-intercept ntp server 213.132.202.192 source outside ntp server 72.251.252.11 source outside ntp server 131.211.8.244 source outside group-policy Default_Tunnel_Group_Name_VPN internal group-policy Default_Tunnel_Group_Name_VPN attributes dns-server value 194.109.104.104 194.109.9.99 vpn-tunnel-protocol ikev1 split-tunnel-policy tunnelspecified split-tunnel-network-list value Default_Tunnel_Group_Name_VPN_splitTunnelAcl username ******* password ************* encrypted privilege 0 username ******* attributes vpn-group-policy Default_Tunnel_Group_Name_VPN username ******* password ************* encrypted privilege 15 username ******* password ************* encrypted privilege 0 username ******* attributes vpn-group-policy Default_Tunnel_Group_Name_VPN username ******* password ************* encrypted privilege 0 username ******* attributes vpn-group-policy Default_Tunnel_Group_Name_VPN tunnel-group Default_Tunnel_Group_Name_VPN type remote-access tunnel-group Default_Tunnel_Group_Name_VPN general-attributes address-pool VPN_IP_POOL default-group-policy Default_Tunnel_Group_Name_VPN tunnel-group Default_Tunnel_Group_Name_VPN ipsec-attributes ikev1 pre-shared-key ***** ! class-map inspection_default match default-inspection-traffic ! ! policy-map type inspect dns preset_dns_map parameters message-length maximum client auto message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect ip-options inspect icmp error inspect ftp inspect icmp ! service-policy global_policy global prompt hostname context no call-home reporting anonymous Cryptochecksum:655f9d00d6ed1c593506cbf9a876cd49 : end CISCOASACLOUD# -
Banks about 9 yearsMany thanks for your response. I have added "access-list OutsideToInside extended permit icmp any any" to my configuration but still no echo responses. To be clear I am pinging using the external IP address (82.94.) for the server. The internal IP address is in the 10.0. range. Any more ideas?
-
Banks about 9 yearsNo it did not work.
-
Banks about 9 yearsYes I am able to ping the ASA public IP address. This traffic is being logged on my ASA. When I ping any servers behind the firewall using the external IP address non of this traffic is being logged. 6 Apr 21 2015 13:36:14 302021 188.207.72.222 57892 82.94.xxx.xxx 0 Teardown ICMP connection for faddr 188.207.72.222/57892 gaddr 82.94.xxx.xxx/0 laddr 82.94.xxx.xxx/0 ||||| 6 Apr 21 2015 13:36:14 302020 188.207.72.222 57892 82.94.xxx.xxx 0 Built inbound ICMP connection for faddr 188.207.72.222/57892 gaddr 82.94.xxx.xxx/0 laddr 82.94.xxx.xxx/0
-
 Amir about 9 yearsI just tried to ping your ASA ip: 188.207.72.222 and unable to ping. Also, if you are using ASDM to configure, you can use packet tracer to check your configuration. above rule should allow you to ping. I guess you internet is working? would you please confirm?
Amir about 9 yearsI just tried to ping your ASA ip: 188.207.72.222 and unable to ping. Also, if you are using ASDM to configure, you can use packet tracer to check your configuration. above rule should allow you to ping. I guess you internet is working? would you please confirm? -
 Amir about 9 yearsI didn't see any deny rule in above config, If you have added deny rule for outside interface after this post, please make sure allow ACL is added before deny rule.
Amir about 9 yearsI didn't see any deny rule in above config, If you have added deny rule for outside interface after this post, please make sure allow ACL is added before deny rule. -
Banks about 9 yearsThat is not the IP address of my ASA but the IP address of my cell phone connected over 3/4G. I am not using ASDM to configure the ASA. However when I check the traffic using the tracer I first select the interface "outside" set the packet type to ICMP, set the source IP address and destination 82.94.xx.xx and type to echo. The result is "the packet is dropped" info : (no route) No route to host.
-
Banks about 9 yearsI have already tried this. But it is still not working. Any more ideas. Is my routing OK?
-
 ewwhite about 9 yearsI don't know. Can you ping 8X.XXX.1XX.XXX?!?
ewwhite about 9 yearsI don't know. Can you ping 8X.XXX.1XX.XXX?!? -
 Amir about 9 yearsAlso, would you please let me know the version of ASA system firmware as there is a requirement of setting Public Server from version 8.4 onwards. Unfortunately, I didn't get any luck trying to this up with CLI. I had to use ASDM to configure public server under Firewall. Please set this and test again please. Apologies for testing on wrong IP, realised it lately.
Amir about 9 yearsAlso, would you please let me know the version of ASA system firmware as there is a requirement of setting Public Server from version 8.4 onwards. Unfortunately, I didn't get any luck trying to this up with CLI. I had to use ASDM to configure public server under Firewall. Please set this and test again please. Apologies for testing on wrong IP, realised it lately. -
Banks about 9 yearsCan you please explain you question to me in more detail. I'm not able to follow you.
-
Banks about 9 yearsAmir, Many thanks for your support. you have helped me to find the solution..
-
 Amir about 9 yearsGreat that you managed to fix the issue and explained here for others. I have also marked your answer as useful.
Amir about 9 yearsGreat that you managed to fix the issue and explained here for others. I have also marked your answer as useful.