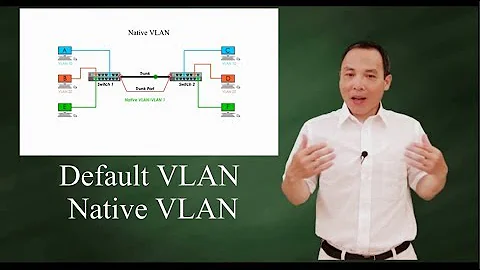
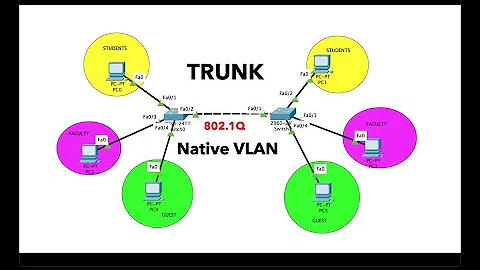
Cisco native port has to be included in allowed vlans of trunk
Solution 1
Emphasis mine:
By default, a trunk port sends traffic to and receives traffic from all VLANs. All VLAN IDs are allowed on each trunk. However, you can remove VLANs from this inclusive list to prevent traffic from the specified VLANs from passing over the trunk. You can add any specific VLANs later that you may want the trunk to carry traffic for back to the list.
And later:
switch(config-if)# switchport trunk allowed vlan { *vlan-list* all | none [ add |except | none | remove { *vlan-list* }]}Sets allowed VLANs for the trunk interface.
In short, once you put a switch trunk allowed vlan command on an interface, you deny all VLANs on that interface except for the ones specifically allowed in the command.
If you've seen configs online where it supposedly works differently, and it's definitely Cisco equipment, it's probably a mistake or a typo. I haven't worked on literally every Cisco operating system, but all the ones I've seen (which are many/most of them) work the same way.
Solution 2
The reason i ask i saw other configs in forums is they did not include the native VLAN in the list of allowed VLANs, i saw in a couple of places and wanted to check if a typo.
The one big reason to not include the native VLAN is the list of allowed VLANs is that a native VLAN is a security risk. The current best practice is to not include the native VLAN in the allowed VLANs on a trunk, and to not use VLAN 1 for anything. There is a misconception that you must have a native VLAN on a trunk.
The link-local protocols that send frames without tags will still work. They really are not part of a VLAN, native or otherwise.
Solution 3
The NATIVE VLAN should NOT be included on the "switch allowed vlan" list. However, the NATIVE VLAN should also NOT be used for ANYTHING else. If you have a vlan defined for any device/access port, then that VLAN must be allowed on the trunk port, and should NOT be used for the NATIVE VLAN.
Related videos on Youtube
morleyc
Updated on September 18, 2022Comments
-
morleyc over 1 year
I have wireless access points that have a single ethernet interface.
On this interface it has a management IP address (untagged), and can create multiple SSIDs each of which can be bridged on to its own VLAN.
As i understand, this is a form of hybrid port with untagged native VLAN and tagged frames.
I have setup the Cisco Catalyst switch with the below for my 4 APs (VLAN 15 connects to the untagged management interface of the APs, VLAN 30 is private and VLAN 300 is guest):
interface range GigabitEthernet1/0/1-4 switchport trunk native vlan 15 switchport trunk allowed vlan 30,15,300 switchport mode trunk spanning-tree portfast spanning-tree bpduguard enable !The APs can send tagged frames OK and these seem to be forwarded correctly.
However I have found to be able to communicate on the management interface I must include the management VLAN in the allowed vlan list, any reason behind this?
The reason i ask i saw other configs in forums is they did not include the native VLAN in the list of allowed VLANs, i saw in a couple of places and wanted to check if a typo.
Thanks in advance.
-
 Alexander Gonchiy about 5 yearsElaborate please.
Alexander Gonchiy about 5 yearsElaborate please.