Debian 8 Jessie with OpenVPN client
I'm guessing I'm missing something new with how systemd controls the service.
Yes, and it is explained in the commentary at the top of /lib/systemd/system/openvpn.service. You, as the other questioner did, are calling a System 5 rc script directly. Do not call System 5 rc scripts directly, especially on a system where System 5 rc isn't used, such as Debian version 8.
OpenVPN is a templatized service under systemd — be that with Fedora, Ubuntu, or Debian Linux. The services are named openvpn@config.service. So you should be starting your /etc/openvpn/servervpn.conf instance with
systemctl start [email protected]
Further reading
Related videos on Youtube
Tim Jones
Updated on September 18, 2022Comments
-
Tim Jones over 1 year
I have a Debian 8 Jessie server that I need to connect to my home network and I'm using an OpenVPN server on a pfSense 2.2 box at home. I have done this fine under older Debian versions, so I'm guessing I'm missing something new with how systemd controls the service...
I have everything I need in
/etc/openvpn/, with a reasonable simple setup:client dev tun proto udp remote home.dynamic-domain.com 1194 resolv-retry infinite nobind user nobody group nobody persist-tun persist-key ca /etc/openvpn/ca.crt cert /etc/openvpn/hostname.crt key /etc/openvpn/hostname.key tls-auth /etc/openvpn/tls.key 1 cipher "AES-256-CBC" comp-lzo verb 3and the relevant certs/keys are present and correct.
Bringing up the config manually works great:
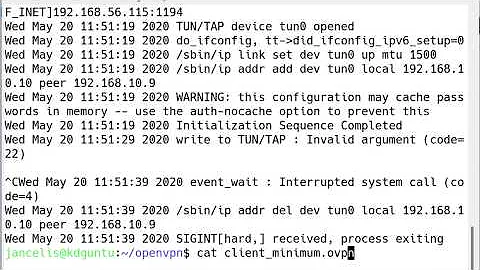
~# openvpn --config /etc/openvpn/servervpn.conf Sat Jun 27 13:26:08 2015 OpenVPN 2.3.4 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [MH] [IPv6] built on Dec 1 2014 Sat Jun 27 13:26:08 2015 library versions: OpenSSL 1.0.1k 8 Jan 2015, LZO 2.08 Sat Jun 27 13:26:08 2015 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info. Sat Jun 27 13:26:08 2015 Control Channel Authentication: using '/etc/openvpn/servervpn/tls.key' as a OpenVPN static key file Sat Jun 27 13:26:08 2015 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Sat Jun 27 13:26:08 2015 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication Sat Jun 27 13:26:08 2015 Socket Buffers: R=[212992->131072] S=[212992->131072] Sat Jun 27 13:26:08 2015 NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay Sat Jun 27 13:26:08 2015 UDPv4 link local: [undef] Sat Jun 27 13:26:08 2015 UDPv4 link remote: [AF_INET]x.x.x.x:1194 Sat Jun 27 13:26:08 2015 TLS: Initial packet from [AF_INET]x.x.x.x:1194, sid=531d85a9 2201aab6 Sat Jun 27 13:26:08 2015 VERIFY OK: depth=1, xxxxxxxx Sat Jun 27 13:26:08 2015 VERIFY OK: depth=0, xxxxxxxx Sat Jun 27 13:26:13 2015 Data Channel Encrypt: Cipher 'AES-256-CBC' initialized with 256 bit key Sat Jun 27 13:26:13 2015 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Sat Jun 27 13:26:13 2015 Data Channel Decrypt: Cipher 'AES-256-CBC' initialized with 256 bit key Sat Jun 27 13:26:13 2015 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication Sat Jun 27 13:26:13 2015 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA Sat Jun 27 13:26:13 2015 [hm-py-router-01] Peer Connection Initiated with [AF_INET]188.78.154.7:11193 Sat Jun 27 13:26:15 2015 SENT CONTROL [hm-py-router-01]: 'PUSH_REQUEST' (status=1) Sat Jun 27 13:26:15 2015 PUSH: Received control message: 'PUSH_REPLY,route 192.168.10.0 255.255.255.0,topology net30,ping 5,ping-restart 60,ifconfig 192.168.11.6 192.168.11.5' Sat Jun 27 13:26:15 2015 OPTIONS IMPORT: timers and/or timeouts modified Sat Jun 27 13:26:15 2015 OPTIONS IMPORT: --ifconfig/up options modified Sat Jun 27 13:26:15 2015 OPTIONS IMPORT: route options modified Sat Jun 27 13:26:15 2015 ROUTE_GATEWAY 176.126.240.1/255.255.248.0 IFACE=eth0 HWADDR=00:16:3c:89:81:e0 Sat Jun 27 13:26:15 2015 TUN/TAP device tun0 opened Sat Jun 27 13:26:15 2015 TUN/TAP TX queue length set to 100 Sat Jun 27 13:26:15 2015 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0 Sat Jun 27 13:26:15 2015 /sbin/ip link set dev tun0 up mtu 1500 Sat Jun 27 13:26:15 2015 /sbin/ip addr add dev tun0 local 192.168.11.6 peer 192.168.11.5 Sat Jun 27 13:26:15 2015 /sbin/ip route add 192.168.10.0/24 via 192.168.11.5 Sat Jun 27 13:26:15 2015 GID set to nogroup Sat Jun 27 13:26:15 2015 UID set to nobody Sat Jun 27 13:26:15 2015 Initialization Sequence Completed ^CSat Jun 27 13:28:17 2015 event_wait : Interrupted system call (code=4) Sat Jun 27 13:28:17 2015 /sbin/ip route del 192.168.11.1/32 RTNETLINK answers: Operation not permitted Sat Jun 27 13:28:17 2015 ERROR: Linux route delete command failed: external program exited with error status: 2 Sat Jun 27 13:28:17 2015 /sbin/ip route del 192.168.51.0/24 RTNETLINK answers: Operation not permitted Sat Jun 27 13:28:17 2015 ERROR: Linux route delete command failed: external program exited with error status: 2 Sat Jun 27 13:28:17 2015 Closing TUN/TAP interface Sat Jun 27 13:28:17 2015 /sbin/ip addr del dev tun0 local 192.168.11.6 peer 192.168.11.5 RTNETLINK answers: Operation not permitted Sat Jun 27 13:28:17 2015 Linux ip addr del failed: external program exited with error status: 2 Sat Jun 27 13:28:17 2015 SIGINT[hard,] received, process exitingUnfortunately, starting openvpn as a service doesn't seem to bring the tunnel up, or do much of anything I can see...
~# systemctl start openvpn.service ~# systemctl status openvpn.service ● openvpn.service - OpenVPN service Loaded: loaded (/lib/systemd/system/openvpn.service; enabled) Active: active (exited) since Sat 2015-06-27 13:29:12 EDT; 4min 3s ago Process: 13873 ExecStart=/bin/true (code=exited, status=0/SUCCESS) Main PID: 13873 (code=exited, status=0/SUCCESS) CGroup: /system.slice/openvpn.serviceThe tunnel just never seems to come up... So I try the 'old' way too:
~# /etc/init.d/openvpn start [ ok ] Starting openvpn (via systemctl): openvpn.service. ~# /etc/init.d/openvpn status ● openvpn.service - OpenVPN service Loaded: loaded (/lib/systemd/system/openvpn.service; enabled) Active: active (exited) since Sat 2015-06-27 13:09:12 EDT; 8min ago Process: 13873 ExecStart=/bin/true (code=exited, status=0/SUCCESS) Main PID: 13873 (code=exited, status=0/SUCCESS) CGroup: /system.slice/openvpn.serviceBut it seems the SysV init script just call to systemctrl anyways.
I've look through the Debian wiki page for OpenVPN and when running as a service it should parse any
*.conffile in /etc/openvpn and bring up the interfaces unless explicitly listed in/etc/default/openvpn.Not sure of my next step.
-
Tim Jones almost 9 yearsThanks for this, sorry for asking a repeated question. My Google-Fu must be weak today... Also, as a side, I'm heading on out to find some proper systemd tutorials. It's WAY more different than I expected.
-
Tim Jones almost 9 yearsThe only commentary at the beginning of my
/lib/systemd/system/openvpn.serviceis# This service is actually a systemd target, but we are using a service since targets cannot be reloaded.. To me that doesn't explain anything no provide a solution. However in/usr/share/doc/openvpn/README.Debian.gzit is explained properlyif you're running systemd, you cannot pass arguments to init.d scripts. In order to start/stop a particular VPN you may use: service openvpn@VPN_NAME start or systemctl start openvpn@VPN_NAME. -
jchook over 6 yearsOn Ubuntu I used:
sudo service openvpn@servervpn start