How do I force `sudo` to ask for a password each time when a specific command is used?
Solution 1
As noted in other answers, sudo can set a timeout on the cached credential timestamp. This can be done specifically for a given command using Defaults in sudoers:
Defaults!/bin/rm timestamp_timeout=0
Always remember to edit sudoers with visudo. I recommend a drop-in file in /etc/sudoers.d instead of editing /etc/sudoers directly. For example:
sudo visudo -f /etc/sudoers.d/always-ask-pass-for-rm
From the manpage for sudoers:
Defaults
Certain configuration options may be changed from their default values at run-time via one or more
Default_Entrylines. These may affect all users on any host, all users on a specific host, a specific user, a specific command, or commands being run as a specific user. Note that per-command entries may not include command line arguments. If you need to specify arguments, define aCmnd_Aliasand reference that instead.Default_Type ::= 'Defaults' | 'Defaults' '@' Host_List | 'Defaults' ':' User_List | 'Defaults' '!' Cmnd_List | 'Defaults' '>' Runas_List Default_Entry ::= Default_Type Parameter_List Parameter_List ::= Parameter | Parameter ',' Parameter_List Parameter ::= Parameter '=' Value | Parameter '+=' Value | Parameter '-=' Value | '!'* Parameter
Note that it does say you can affect "commands being run as a specific user", but doesn't mention commands being run by a specific user, so it might not be possible to constrain it only for your user. The examples in the manpage don't include anything for that.
Solution 2
You can use k option with sudo to reset the timestamp.
If sudo -k is used as a command, it would expire/invalidate the cached credentials immediately.
But if sudo -k is used with some command, for example, sudo -k rm /some/file, the shell would ask for password even if some credentials are already cached. In this case, the new credentials won't be cached. That means if another command with sudo is executed after that, it won't ask for password (if credentials were cached previously).
From sudo's manpage:
-k [command]
When used alone, the -k (kill) option to sudo invalidates the user's cached credentials. The next time sudo is run a password will be required. This option does not require a password and was added to allow a user to revoke sudo permissions from a .logout file. Not all security policies support credential caching.
When used in conjunction with a command or an option that may require a password, the -k option will cause sudo to ignore the user's cached credentials. As a result, sudo will prompt for a password (if one is required by the security policy) and will not update the user's cached credentials.
If you want to make sudo to ask for password for specific commands without using k every time, you can define custom functions in .bashrc. For example, from pa4080's comment:
sudo() { if [[ $@ =~ ^rm ]]; then /usr/bin/sudo -k "$@"; else /usr/bin/sudo "$@"; fi; }
Solution 3
You can set sudo to always ask for a password:
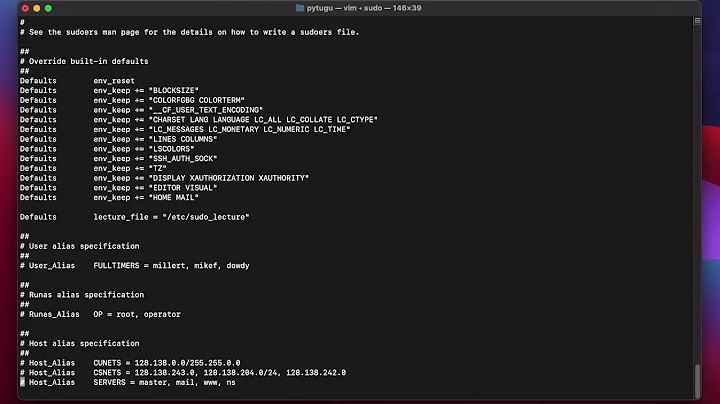
$ sudo cat /etc/sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset, timestamp_timeout=120, pwfeedback
#Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
In my configuration I have sudo timeout set at 2 hours (120 minutes) before it asks for a password again. Setting it to 0 will require password every time you use sudo
Solution 4
rm wrapper script
Sometime ago I wrote a wrapper script for the rm command:
Some of the notable features:
- An encrypted password must be used each time
rmis called unless it is being used within a batch job likesudo apt-getorsudo update-grub. - Ensure top level directories are never removed even if a relative path was passed.
- Every time
rmis used it is logged tojournalctland/var/log/syslog.
Related videos on Youtube
pa4080
I have a degree as a Mechanical Engineer and Doctor of Engineering Science as well. However, since I am self-educated at Computer Science and English language, please be tolerant at my mistakes and feel free to correct them when it is necessary. Actually my real name is Sраs Zdrаvkоv Sраsоv. In my birthplace Pacho is "short" for Spas. So the first two letters of my nickname - 'pa' - comes from there. Written in Bulgarian, the number '4' starts with the letter 'ч' that is pronounced as 'ch'. The number '0' looks like the letter 'o'. So we have 'pa40', and finally '80' is my birth year ;) This nickname originates from the time before ICQ and mIRC was modern. Create Digital Ocean account and get $100 in credit to use for 2 months just for signing up.
Updated on September 18, 2022Comments
-
 pa4080 over 1 year
pa4080 over 1 yearIs there a way to force the
sudocommand to ask for a password each time when I'm usingsudo rm /path/file?I want to protect my self from stupid mistakes, committed due to low attention when I'm running some commands from the history.
-
chepner over 4 yearsWhy set it to 1 minute? The OP asks for no caching of credentials; set it to 0.
-
chepner over 4 yearsBut why so much emphasis on the values the user isn't asking about? Setting it to 0 seems like an afterthought, when it should be the entire answer.
-
 WinEunuuchs2Unix over 4 years@chepner I've revised answer. Thanks.
WinEunuuchs2Unix over 4 years@chepner I've revised answer. Thanks. -
 bac0n over 4 yearsit is easy to circumvent by using full path to sudo so i think it gives a false sense of security.
bac0n over 4 yearsit is easy to circumvent by using full path to sudo so i think it gives a false sense of security. -
 bac0n over 4 years
bac0n over 4 yearsln -s /bin/rm rmdo; sudo ./rmdo <file> -
sudo mcsudoface over 4 years@bac0n I'm operating under the assumption that this is more to deter accidental gun-to-foot scenarios rather than to prevent deliberate attack. Otherwise one would be pretty dumb to allow arbitrary
sudocommands for any account with shell access. -
ymbirtt over 4 years@bac0n, I agree that this is easy to circumvent, but I don't think this means that it gives a false sense of security. The use-case here is like a fire alarm with a cover over it; the cover isn't to stop malicious users from triggering the alarm, it's to stop an inattentive user from accidentally leaning against the button. The fact that it's easy to deliberately bypass is kind of the intention, not an exploit.
-
 WinEunuuchs2Unix over 4 yearsGreat first time answer from a user account created just today! It's like my own answer below on steroids. Well done.
WinEunuuchs2Unix over 4 yearsGreat first time answer from a user account created just today! It's like my own answer below on steroids. Well done. -
 Kulfy over 4 yearsHow do I adopt this method when there isn't any specific executable binary, for eg. Shell in-built commands?
Kulfy over 4 yearsHow do I adopt this method when there isn't any specific executable binary, for eg. Shell in-built commands? -
Eliah Kagan over 4 years@Kulfy How would you run a shell builtin with
sudo? -
 Kulfy over 4 years@EliahKagan For example
Kulfy over 4 years@EliahKagan For examplesudo alias? This might sound odd but I'm just curious. -
Eliah Kagan over 4 years@Kulfy
sudoonly runs external commands.sudo aliasgives the error "sudo: alias: command not found" outside the unusual case that you also have an external command calledalias. Some shells, like Bash, have some builtins that shadow external commands. If one tries to run them withsudo, one really runs the same-named external commands. For example,sudo kill,sudo printf, andsudo echorun external commands. See Why doesn't `sudo cd /var/named` work?, Why is there a /bin/echo and why would I want to use it?. -
 Kulfy over 4 years@EliahKagan I see. Thanks for the information.
Kulfy over 4 years@EliahKagan I see. Thanks for the information.